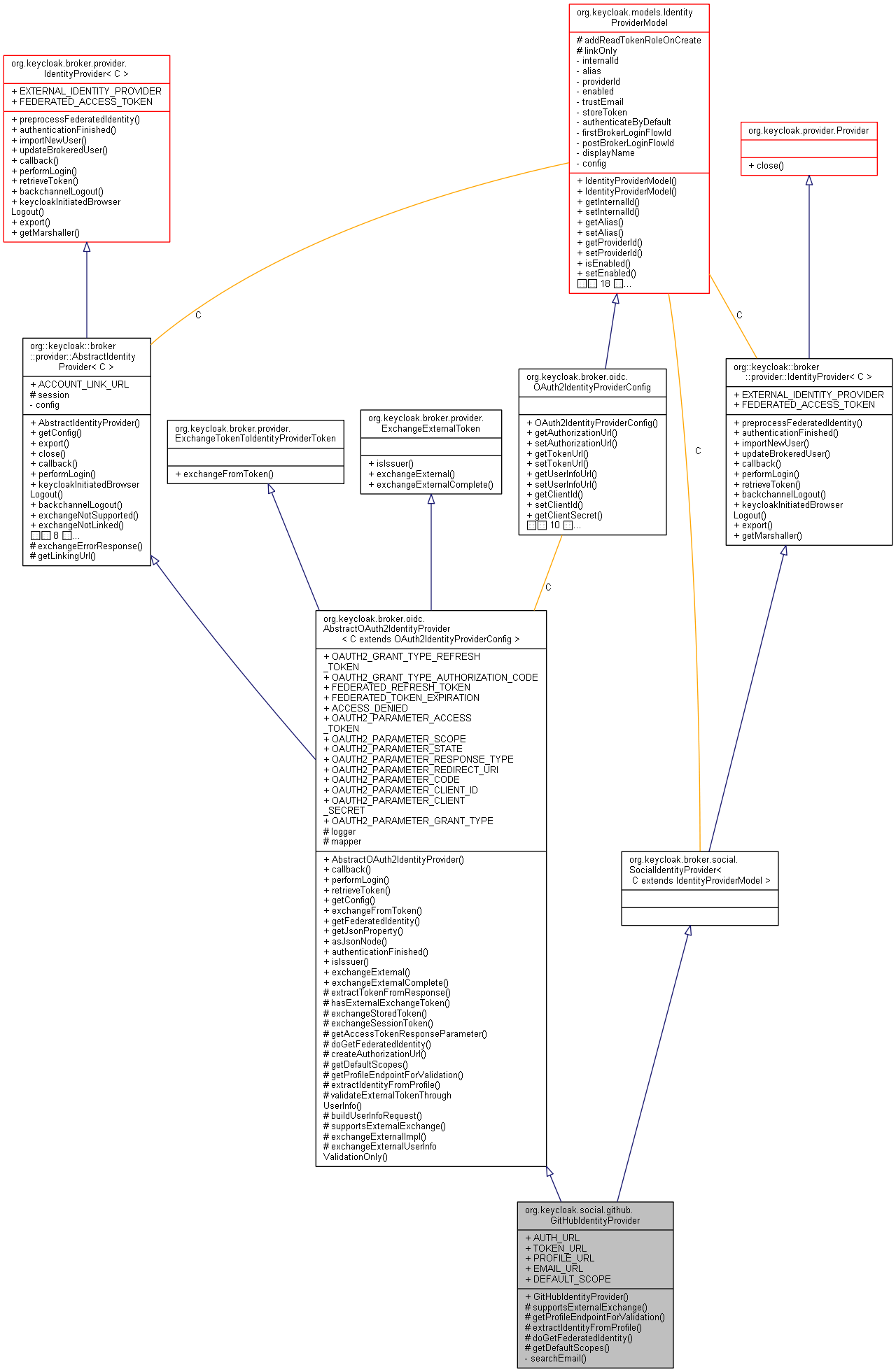
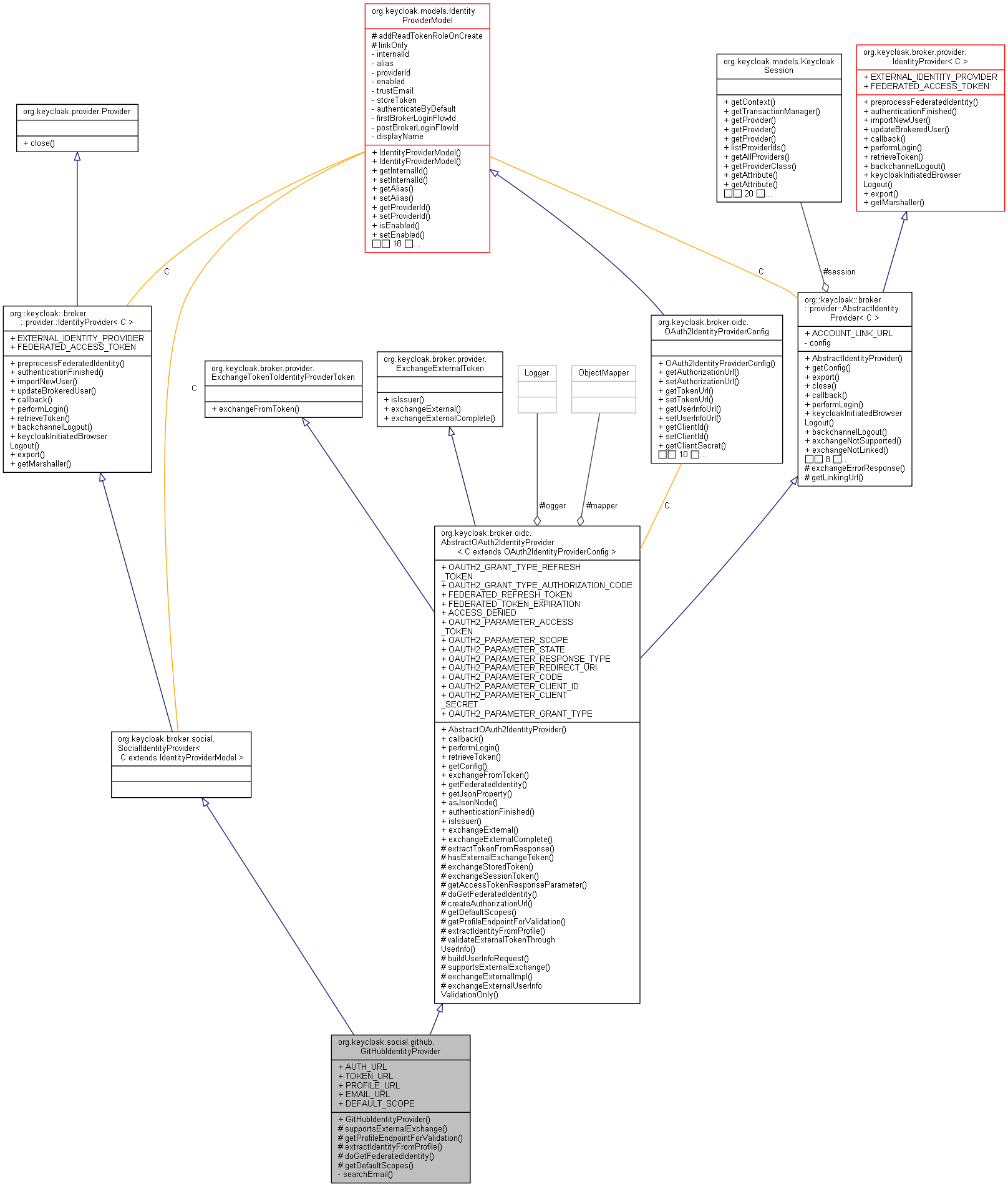
公開メンバ関数 | |
| GitHubIdentityProvider (KeycloakSession session, OAuth2IdentityProviderConfig config) | |
| Object | callback (RealmModel realm, AuthenticationCallback callback, EventBuilder event) |
| Response | performLogin (AuthenticationRequest request) |
| Response | retrieveToken (KeycloakSession session, FederatedIdentityModel identity) |
| C | getConfig () |
| Response | exchangeFromToken (UriInfo uriInfo, EventBuilder event, ClientModel authorizedClient, UserSessionModel tokenUserSession, UserModel tokenSubject, MultivaluedMap< String, String > params) |
| BrokeredIdentityContext | getFederatedIdentity (String response) |
| String | getJsonProperty (JsonNode jsonNode, String name) |
| JsonNode | asJsonNode (String json) throws IOException |
| void | authenticationFinished (AuthenticationSessionModel authSession, BrokeredIdentityContext context) |
| boolean | isIssuer (String issuer, MultivaluedMap< String, String > params) |
| final BrokeredIdentityContext | exchangeExternal (EventBuilder event, MultivaluedMap< String, String > params) |
| void | exchangeExternalComplete (UserSessionModel userSession, BrokeredIdentityContext context, MultivaluedMap< String, String > params) |
| Response | export (UriInfo uriInfo, RealmModel realm, String format) |
| void | close () |
| Response | keycloakInitiatedBrowserLogout (KeycloakSession session, UserSessionModel userSession, UriInfo uriInfo, RealmModel realm) |
| void | backchannelLogout (KeycloakSession session, UserSessionModel userSession, UriInfo uriInfo, RealmModel realm) |
| Response | exchangeNotSupported () |
| Response | exchangeNotLinked (UriInfo uriInfo, ClientModel authorizedClient, UserSessionModel tokenUserSession, UserModel tokenSubject) |
| Response | exchangeNotLinkedNoStore (UriInfo uriInfo, ClientModel authorizedClient, UserSessionModel tokenUserSession, UserModel tokenSubject) |
| Response | exchangeTokenExpired (UriInfo uriInfo, ClientModel authorizedClient, UserSessionModel tokenUserSession, UserModel tokenSubject) |
| Response | exchangeUnsupportedRequiredType () |
| void | preprocessFederatedIdentity (KeycloakSession session, RealmModel realm, BrokeredIdentityContext context) |
| void | importNewUser (KeycloakSession session, RealmModel realm, UserModel user, BrokeredIdentityContext context) |
| void | updateBrokeredUser (KeycloakSession session, RealmModel realm, UserModel user, BrokeredIdentityContext context) |
| IdentityProviderDataMarshaller | getMarshaller () |
| void | preprocessFederatedIdentity (KeycloakSession session, RealmModel realm, BrokeredIdentityContext context) |
| void | authenticationFinished (AuthenticationSessionModel authSession, BrokeredIdentityContext context) |
| void | importNewUser (KeycloakSession session, RealmModel realm, UserModel user, BrokeredIdentityContext context) |
| void | updateBrokeredUser (KeycloakSession session, RealmModel realm, UserModel user, BrokeredIdentityContext context) |
| Object | callback (RealmModel realm, AuthenticationCallback callback, EventBuilder event) |
| Response | performLogin (AuthenticationRequest request) |
| Response | retrieveToken (KeycloakSession session, FederatedIdentityModel identity) |
| void | backchannelLogout (KeycloakSession session, UserSessionModel userSession, UriInfo uriInfo, RealmModel realm) |
| Response | keycloakInitiatedBrowserLogout (KeycloakSession session, UserSessionModel userSession, UriInfo uriInfo, RealmModel realm) |
| Response | export (UriInfo uriInfo, RealmModel realm, String format) |
| IdentityProviderDataMarshaller | getMarshaller () |
| void | close () |
公開変数類 | |
| String | EXTERNAL_IDENTITY_PROVIDER |
| String | FEDERATED_ACCESS_TOKEN |
| String | EXTERNAL_IDENTITY_PROVIDER = "EXTERNAL_IDENTITY_PROVIDER" |
| String | FEDERATED_ACCESS_TOKEN = "FEDERATED_ACCESS_TOKEN" |
静的公開変数類 | |
| static final String | AUTH_URL = "https://github.com/login/oauth/authorize" |
| static final String | TOKEN_URL = "https://github.com/login/oauth/access_token" |
| static final String | PROFILE_URL = "https://api.github.com/user" |
| static final String | EMAIL_URL = "https://api.github.com/user/emails" |
| static final String | DEFAULT_SCOPE = "user:email" |
| static final String | OAUTH2_GRANT_TYPE_REFRESH_TOKEN = "refresh_token" |
| static final String | OAUTH2_GRANT_TYPE_AUTHORIZATION_CODE = "authorization_code" |
| static final String | FEDERATED_REFRESH_TOKEN = "FEDERATED_REFRESH_TOKEN" |
| static final String | FEDERATED_TOKEN_EXPIRATION = "FEDERATED_TOKEN_EXPIRATION" |
| static final String | ACCESS_DENIED = "access_denied" |
| static final String | OAUTH2_PARAMETER_ACCESS_TOKEN = "access_token" |
| static final String | OAUTH2_PARAMETER_SCOPE = "scope" |
| static final String | OAUTH2_PARAMETER_STATE = "state" |
| static final String | OAUTH2_PARAMETER_RESPONSE_TYPE = "response_type" |
| static final String | OAUTH2_PARAMETER_REDIRECT_URI = "redirect_uri" |
| static final String | OAUTH2_PARAMETER_CODE = "code" |
| static final String | OAUTH2_PARAMETER_CLIENT_ID = "client_id" |
| static final String | OAUTH2_PARAMETER_CLIENT_SECRET = "client_secret" |
| static final String | OAUTH2_PARAMETER_GRANT_TYPE = "grant_type" |
| static final String | ACCOUNT_LINK_URL = "account-link-url" |
限定公開メンバ関数 | |
| boolean | supportsExternalExchange () |
| String | getProfileEndpointForValidation (EventBuilder event) |
| BrokeredIdentityContext | extractIdentityFromProfile (EventBuilder event, JsonNode profile) |
| BrokeredIdentityContext | doGetFederatedIdentity (String accessToken) |
| String | getDefaultScopes () |
| String | extractTokenFromResponse (String response, String tokenName) |
| Response | hasExternalExchangeToken (EventBuilder event, UserSessionModel tokenUserSession, MultivaluedMap< String, String > params) |
| Response | exchangeStoredToken (UriInfo uriInfo, EventBuilder event, ClientModel authorizedClient, UserSessionModel tokenUserSession, UserModel tokenSubject) |
| Response | exchangeSessionToken (UriInfo uriInfo, EventBuilder event, ClientModel authorizedClient, UserSessionModel tokenUserSession, UserModel tokenSubject) |
| String | getAccessTokenResponseParameter () |
| UriBuilder | createAuthorizationUrl (AuthenticationRequest request) |
| BrokeredIdentityContext | validateExternalTokenThroughUserInfo (EventBuilder event, String subjectToken, String subjectTokenType) |
| SimpleHttp | buildUserInfoRequest (String subjectToken, String userInfoUrl) |
| BrokeredIdentityContext | exchangeExternalImpl (EventBuilder event, MultivaluedMap< String, String > params) |
| BrokeredIdentityContext | exchangeExternalUserInfoValidationOnly (EventBuilder event, MultivaluedMap< String, String > params) |
| Response | exchangeErrorResponse (UriInfo uriInfo, ClientModel authorizedClient, UserSessionModel tokenUserSession, String errorCode, String reason) |
| String | getLinkingUrl (UriInfo uriInfo, ClientModel authorizedClient, UserSessionModel tokenUserSession) |
限定公開変数類 | |
| final KeycloakSession | session |
静的限定公開変数類 | |
| static final Logger | logger = Logger.getLogger(AbstractOAuth2IdentityProvider.class) |
| static ObjectMapper | mapper = new ObjectMapper() |
非公開メンバ関数 | |
| String | searchEmail (String accessToken) |
詳解
構築子と解体子
◆ GitHubIdentityProvider()
|
inline |
関数詳解
◆ asJsonNode()
|
inlineinherited |
◆ authenticationFinished() [1/2]
|
inherited |
◆ authenticationFinished() [2/2]
|
inlineinherited |
◆ backchannelLogout() [1/2]
|
inlineinherited |
◆ backchannelLogout() [2/2]
|
inherited |
◆ buildUserInfoRequest()
|
inlineprotectedinherited |
◆ callback() [1/2]
|
inherited |
JAXRS callback endpoint for when the remote IDP wants to callback to keycloak.
- 戻り値
org.keycloak.social.twitter.TwitterIdentityProviderで実装されています。
◆ callback() [2/2]
|
inlineinherited |
◆ close() [1/2]
|
inherited |
org.keycloak.models.sessions.infinispan.InfinispanUserSessionProvider, org.keycloak.storage.UserStorageManager, org.keycloak.protocol.saml.SamlProtocol, org.keycloak.storage.ldap.LDAPStorageProvider, org.keycloak.forms.login.freemarker.FreeMarkerLoginFormsProvider, org.keycloak.models.cache.infinispan.RealmCacheSession, org.keycloak.models.jpa.JpaUserProvider, org.keycloak.models.cache.infinispan.UserCacheSession, org.keycloak.forms.account.freemarker.FreeMarkerAccountProvider, org.keycloak.protocol.oidc.OIDCLoginProtocol, org.keycloak.models.jpa.session.JpaUserSessionPersisterProvider, org.keycloak.credential.UserCredentialStoreManager, org.keycloak.services.managers.DefaultBruteForceProtector, org.keycloak.connections.jpa.updater.liquibase.LiquibaseJpaUpdaterProvider, org.keycloak.email.freemarker.FreeMarkerEmailTemplateProvider, org.keycloak.protocol.saml.EntityDescriptorDescriptionConverter, org.keycloak.federation.kerberos.KerberosFederationProvider, org.keycloak.models.jpa.JpaUserCredentialStore, org.keycloak.storage.ClientStorageManager, org.keycloak.keys.infinispan.InfinispanPublicKeyStorageProvider, org.keycloak.models.sessions.infinispan.InfinispanAuthenticationSessionProvider, org.keycloak.services.clientregistration.AbstractClientRegistrationProvider, org.keycloak.authentication.authenticators.x509.AbstractX509ClientCertificateAuthenticator, org.keycloak.authentication.authenticators.resetcred.ResetCredentialEmail, org.keycloak.authentication.forms.RegistrationRecaptcha, org.keycloak.authentication.authenticators.browser.ScriptBasedAuthenticator, org.keycloak.email.DefaultEmailSenderProvider, org.keycloak.models.jpa.JpaRealmProvider, org.keycloak.exportimport.dir.DirImportProvider, org.keycloak.protocol.docker.DockerAuthV2Protocol, org.keycloak.authentication.authenticators.browser.SpnegoAuthenticator, org.keycloak.authorization.AuthorizationProvider, org.keycloak.authentication.authenticators.resetcred.ResetCredentialChooseUser, org.keycloak.authentication.forms.RegistrationUserCreation, org.keycloak.connections.jpa.updater.liquibase.lock.LiquibaseDBLockProvider, org.keycloak.theme.ExtendingThemeManager, org.keycloak.protocol.saml.installation.KeycloakSamlClientInstallation, org.keycloak.models.cache.infinispan.authorization.StoreFactoryCacheSession, org.keycloak.protocol.saml.installation.SamlIDPDescriptorClientInstallation, org.keycloak.authentication.authenticators.challenge.BasicAuthAuthenticator, org.keycloak.authentication.authenticators.cli.CliUsernamePasswordAuthenticator, org.keycloak.protocol.oidc.installation.KeycloakOIDCClientInstallation, org.keycloak.authentication.forms.RegistrationProfile, org.keycloak.authentication.requiredactions.UpdatePassword, org.keycloak.authentication.requiredactions.UpdateProfile, org.keycloak.protocol.saml.mappers.RoleNameMapper, org.keycloak.authentication.forms.RegistrationPassword, org.keycloak.protocol.oidc.OIDCWellKnownProvider, org.keycloak.events.log.JBossLoggingEventListenerProvider, org.keycloak.protocol.saml.profile.ecp.authenticator.HttpBasicAuthenticator, org.keycloak.connections.jpa.updater.liquibase.conn.DefaultLiquibaseConnectionProvider, org.keycloak.authentication.authenticators.console.ConsoleUsernamePasswordAuthenticator, org.keycloak.authentication.authenticators.broker.AbstractIdpAuthenticator, org.keycloak.protocol.saml.installation.ModAuthMellonClientInstallation, org.keycloak.authentication.authenticators.browser.IdentityProviderAuthenticator, org.keycloak.credential.hash.Pbkdf2PasswordHashProvider, org.keycloak.events.jpa.JpaEventStoreProvider, org.keycloak.authentication.authenticators.browser.UsernamePasswordForm, org.keycloak.authentication.authenticators.browser.OTPFormAuthenticator, org.keycloak.authentication.requiredactions.ConsoleUpdateTotp, org.keycloak.authentication.requiredactions.ConsoleVerifyEmail, org.keycloak.authentication.requiredactions.VerifyEmail, org.keycloak.authentication.requiredactions.TermsAndConditions, org.keycloak.authorization.protection.introspect.RPTIntrospectionProvider, org.keycloak.protocol.oidc.installation.KeycloakOIDCJbossSubsystemClientInstallation, org.keycloak.authentication.requiredactions.UpdateTotp, org.keycloak.models.UserProvider, org.keycloak.exportimport.dir.DirExportProvider, org.keycloak.models.UserSessionProvider, org.keycloak.scripting.DefaultScriptingProvider, org.keycloak.protocol.oidc.AccessTokenIntrospectionProvider, org.keycloak.protocol.saml.installation.SamlSPDescriptorClientInstallation, org.keycloak.exportimport.singlefile.SingleFileExportProvider, org.keycloak.exportimport.singlefile.SingleFileImportProvider, org.keycloak.policy.HashIterationsPasswordPolicyProviderFactory, org.keycloak.services.migration.DefaultMigrationProvider, org.keycloak.authentication.authenticators.resetcred.AbstractSetRequiredActionAuthenticator, org.keycloak.storage.ldap.mappers.AbstractLDAPStorageMapper, org.keycloak.services.clientregistration.AdapterInstallationClientRegistrationProvider, org.keycloak.timer.basic.BasicTimerProvider, org.keycloak.theme.FolderThemeProvider, org.keycloak.models.RealmProvider, org.keycloak.policy.HistoryPasswordPolicyProvider, org.keycloak.protocol.saml.installation.KeycloakSamlSubsystemInstallation, org.keycloak.storage.jpa.JpaUserFederatedStorageProvider, org.keycloak.authentication.authenticators.browser.CookieAuthenticator, org.keycloak.keys.AbstractGeneratedSecretKeyProvider, org.keycloak.authorization.jpa.store.JPAStoreFactory, org.keycloak.events.email.EmailEventListenerProvider, org.keycloak.authentication.authenticators.challenge.NoCookieFlowRedirectAuthenticator, org.keycloak.policy.BlacklistPasswordPolicyProvider, org.keycloak.authentication.authenticators.console.ConsoleOTPFormAuthenticator, org.keycloak.authentication.requiredactions.ConsoleTermsAndConditions, org.keycloak.models.sessions.infinispan.InfinispanCodeToTokenStoreProvider, org.keycloak.policy.RegexPatternsPasswordPolicyProvider, org.keycloak.models.sessions.infinispan.InfinispanStickySessionEncoderProvider, org.keycloak.cluster.infinispan.InfinispanClusterProvider, org.keycloak.authentication.requiredactions.ConsoleUpdateProfile, org.keycloak.exportimport.KeycloakClientDescriptionConverter, org.keycloak.policy.DefaultPasswordPolicyManagerProvider, org.keycloak.services.x509.AbstractClientCertificateFromHttpHeadersLookup, org.keycloak.theme.ClasspathThemeProvider, org.keycloak.policy.DigitsPasswordPolicyProvider, org.keycloak.policy.LowerCasePasswordPolicyProvider, org.keycloak.policy.SpecialCharsPasswordPolicyProvider, org.keycloak.policy.UpperCasePasswordPolicyProvider, org.keycloak.models.session.DisabledUserSessionPersisterProvider, org.keycloak.policy.NotUsernamePasswordPolicyProvider, org.keycloak.theme.DefaultThemeSelectorProvider, org.keycloak.connections.infinispan.DefaultInfinispanConnectionProvider, org.keycloak.provider.ExceptionConverter, org.keycloak.policy.LengthPasswordPolicyProvider, org.keycloak.authentication.forms.RegistrationPage, org.keycloak.protocol.oidc.OIDCClientDescriptionConverter, org.keycloak.theme.ClasspathThemeResourceProviderFactory, org.keycloak.policy.HashAlgorithmPasswordPolicyProviderFactory, org.keycloak.models.sessions.infinispan.InfinispanActionTokenStoreProvider, org.keycloak.authentication.authenticators.x509.X509ClientCertificateAuthenticator, org.keycloak.locale.DefaultLocaleSelectorProvider, org.keycloak.policy.ForceExpiredPasswordPolicyProviderFactory, org.keycloak.authentication.authenticators.directgrant.AbstractDirectGrantAuthenticator, org.keycloak.protocol.docker.installation.DockerComposeYamlInstallationProvider, org.keycloak.truststore.FileTruststoreProvider, org.keycloak.protocol.oidc.mappers.AbstractOIDCProtocolMapper, org.keycloak.authentication.authenticators.AttemptedAuthenticator, org.keycloak.authorization.policy.provider.drools.DroolsPolicyProvider, org.keycloak.services.clientregistration.policy.ClientRegistrationPolicy, org.keycloak.services.x509.DefaultClientCertificateLookup, org.keycloak.connections.jpa.DefaultJpaConnectionProvider, org.keycloak.authorization.config.UmaWellKnownProvider, org.keycloak.protocol.saml.mappers.AbstractSAMLProtocolMapper, org.keycloak.urls.HostnameProvider, org.keycloak.authentication.authenticators.client.AbstractClientAuthenticator, org.keycloak.keys.KeyProvider, org.keycloak.protocol.docker.installation.DockerRegistryConfigFileInstallationProvider, org.keycloak.protocol.docker.installation.DockerVariableOverrideInstallationProvider, org.keycloak.protocol.docker.mapper.DockerAuthV2ProtocolMapper, org.keycloak.transaction.JtaTransactionManagerLookup, org.keycloak.broker.provider.AbstractIdentityProviderMapper, org.keycloak.authentication.AbstractFormAuthenticator, org.keycloak.crypto.SignatureProvider, org.keycloak.credential.CredentialProvider, org.keycloak.protocol.oidc.ext.OIDCExtProvider (計143項目)で実装されています。
◆ close() [2/2]
|
inlineinherited |
◆ createAuthorizationUrl()
|
inlineprotectedinherited |
◆ doGetFederatedIdentity()
|
inlineprotected |
◆ exchangeErrorResponse()
|
inlineprotectedinherited |
◆ exchangeExternal()
|
inlineinherited |
org.keycloak.broker.provider.ExchangeExternalTokenを実装しています。
◆ exchangeExternalComplete()
|
inlineinherited |
◆ exchangeExternalImpl()
|
inlineprotectedinherited |
◆ exchangeExternalUserInfoValidationOnly()
|
inlineprotectedinherited |
◆ exchangeFromToken()
|
inlineinherited |
org.keycloak.broker.provider.ExchangeTokenToIdentityProviderTokenを実装しています。
◆ exchangeNotLinked()
|
inlineinherited |
◆ exchangeNotLinkedNoStore()
|
inlineinherited |
◆ exchangeNotSupported()
|
inlineinherited |
◆ exchangeSessionToken()
|
inlineprotectedinherited |
◆ exchangeStoredToken()
|
inlineprotectedinherited |
◆ exchangeTokenExpired()
|
inlineinherited |
◆ exchangeUnsupportedRequiredType()
|
inlineinherited |
◆ export() [1/2]
|
inlineinherited |
◆ export() [2/2]
|
inherited |
Export a representation of the IdentityProvider in a specific format. For example, a SAML EntityDescriptor
- 戻り値
◆ extractIdentityFromProfile()
|
inlineprotected |
◆ extractTokenFromResponse()
|
inlineprotectedinherited |
◆ getAccessTokenResponseParameter()
|
inlineprotectedinherited |
◆ getConfig()
|
inlineinherited |
◆ getDefaultScopes()
|
inlineprotected |
◆ getFederatedIdentity()
|
inlineinherited |
◆ getJsonProperty()
|
inlineinherited |
Get JSON property as text. JSON numbers and booleans are converted to text. Empty string is converted to null.
- 引数
-
jsonNode to get property from name of property to get
- 戻り値
- string value of the property or null.
◆ getLinkingUrl()
|
inlineprotectedinherited |
◆ getMarshaller() [1/2]
|
inherited |
Implementation of marshaller to serialize/deserialize attached data to Strings, which can be saved in clientSession
- 戻り値
◆ getMarshaller() [2/2]
|
inlineinherited |
◆ getProfileEndpointForValidation()
|
inlineprotected |
◆ hasExternalExchangeToken()
|
inlineprotectedinherited |
check to see if we have a token exchange in session in other words check to see if this session was created by an external exchange
- 引数
-
tokenUserSession params
- 戻り値
◆ importNewUser() [1/2]
|
inherited |
◆ importNewUser() [2/2]
|
inlineinherited |
◆ isIssuer()
|
inlineinherited |
org.keycloak.broker.provider.ExchangeExternalTokenを実装しています。
◆ keycloakInitiatedBrowserLogout() [1/2]
|
inlineinherited |
◆ keycloakInitiatedBrowserLogout() [2/2]
|
inherited |
Called when a Keycloak application initiates a logout through the browser. This is expected to do a logout with the IDP
- 引数
-
userSession uriInfo realm
- 戻り値
- null if this is not supported by this provider
◆ performLogin() [1/2]
|
inherited |
Initiates the authentication process by sending an authentication request to an identity provider. This method is called only once during the authentication.
- 引数
-
request The initial authentication request. Contains all the contextual information in order to build an authentication request to the identity provider.
- 戻り値
org.keycloak.social.twitter.TwitterIdentityProviderで実装されています。
◆ performLogin() [2/2]
|
inlineinherited |
◆ preprocessFederatedIdentity() [1/2]
|
inherited |
◆ preprocessFederatedIdentity() [2/2]
|
inlineinherited |
◆ retrieveToken() [1/2]
|
inherited |
Returns a javax.ws.rs.core.Response containing the token previously stored during the authentication process for a specific user.
- 引数
-
identity
- 戻り値
org.keycloak.social.twitter.TwitterIdentityProviderで実装されています。
◆ retrieveToken() [2/2]
|
inlineinherited |
◆ searchEmail()
|
inlineprivate |
◆ supportsExternalExchange()
|
inlineprotected |
◆ updateBrokeredUser() [1/2]
|
inherited |
◆ updateBrokeredUser() [2/2]
|
inlineinherited |
◆ validateExternalTokenThroughUserInfo()
|
inlineprotectedinherited |
メンバ詳解
◆ ACCESS_DENIED
|
staticinherited |
◆ ACCOUNT_LINK_URL
|
staticinherited |
◆ AUTH_URL
|
static |
◆ DEFAULT_SCOPE
|
static |
◆ EMAIL_URL
|
static |
◆ EXTERNAL_IDENTITY_PROVIDER [1/2]
|
inherited |
◆ EXTERNAL_IDENTITY_PROVIDER [2/2]
|
inherited |
◆ FEDERATED_ACCESS_TOKEN [1/2]
|
inherited |
◆ FEDERATED_ACCESS_TOKEN [2/2]
|
inherited |
◆ FEDERATED_REFRESH_TOKEN
|
staticinherited |
◆ FEDERATED_TOKEN_EXPIRATION
|
staticinherited |
◆ logger
|
staticprotectedinherited |
◆ mapper
|
staticprotectedinherited |
◆ OAUTH2_GRANT_TYPE_AUTHORIZATION_CODE
|
staticinherited |
◆ OAUTH2_GRANT_TYPE_REFRESH_TOKEN
|
staticinherited |
◆ OAUTH2_PARAMETER_ACCESS_TOKEN
|
staticinherited |
◆ OAUTH2_PARAMETER_CLIENT_ID
|
staticinherited |
◆ OAUTH2_PARAMETER_CLIENT_SECRET
|
staticinherited |
◆ OAUTH2_PARAMETER_CODE
|
staticinherited |
◆ OAUTH2_PARAMETER_GRANT_TYPE
|
staticinherited |
◆ OAUTH2_PARAMETER_REDIRECT_URI
|
staticinherited |
◆ OAUTH2_PARAMETER_RESPONSE_TYPE
|
staticinherited |
◆ OAUTH2_PARAMETER_SCOPE
|
staticinherited |
◆ OAUTH2_PARAMETER_STATE
|
staticinherited |
◆ PROFILE_URL
|
static |
◆ session
|
protectedinherited |
◆ TOKEN_URL
|
static |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/src/keycloak/src/main/java/org/keycloak/social/github/GitHubIdentityProvider.java
 1.8.13
1.8.13