
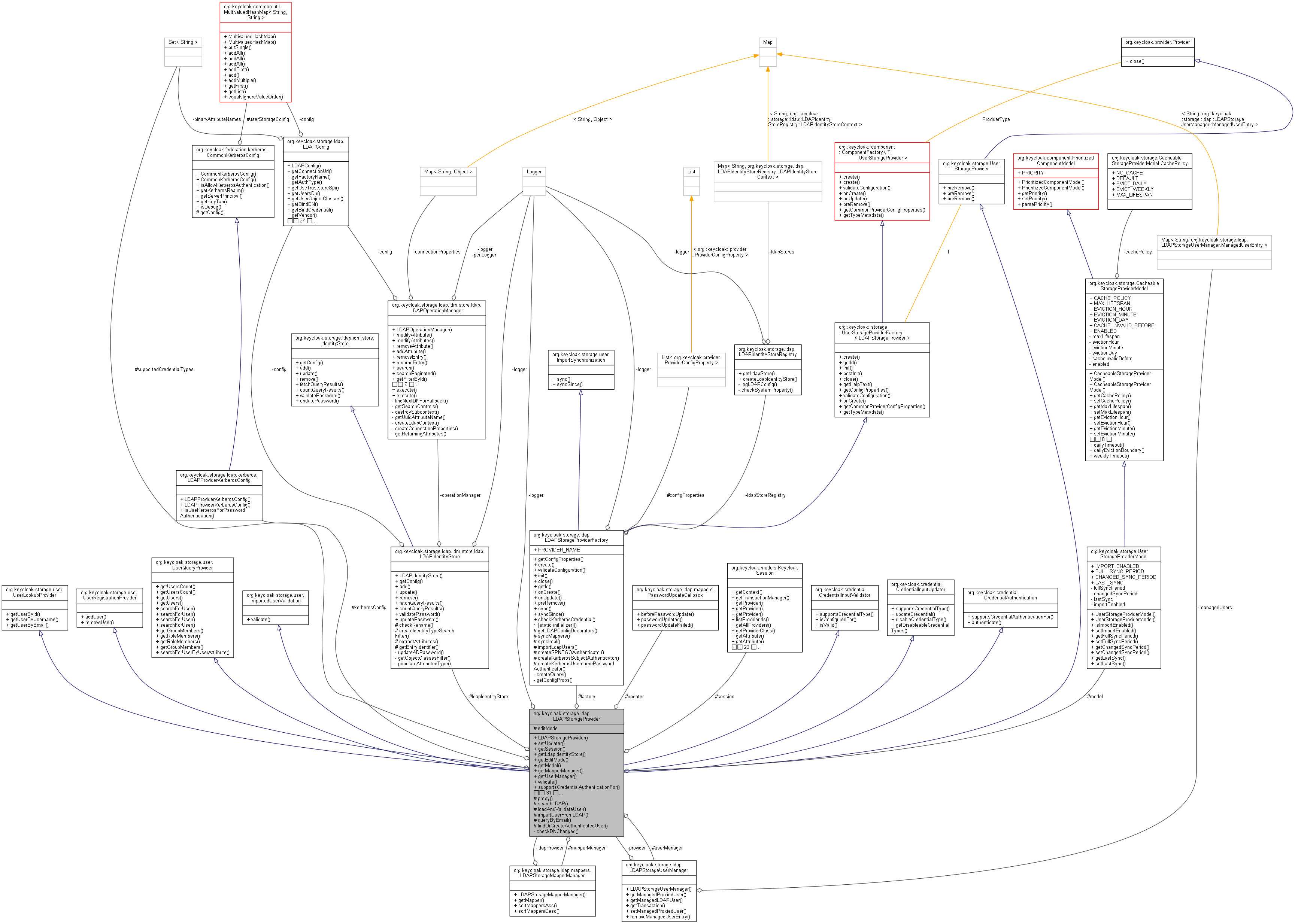
限定公開メンバ関数 | |
| UserModel | proxy (RealmModel realm, UserModel local, LDAPObject ldapObject) |
| List< LDAPObject > | searchLDAP (RealmModel realm, Map< String, String > attributes, int maxResults) |
| LDAPObject | loadAndValidateUser (RealmModel realm, UserModel local) |
| UserModel | importUserFromLDAP (KeycloakSession session, RealmModel realm, LDAPObject ldapUser) |
| LDAPObject | queryByEmail (RealmModel realm, String email) |
| UserModel | findOrCreateAuthenticatedUser (RealmModel realm, String username) |
非公開メンバ関数 | |
| void | checkDNChanged (RealmModel realm, UserModel local, LDAPObject ldapObject) |
静的非公開変数類 | |
| static final Logger | logger = Logger.getLogger(LDAPStorageProvider.class) |
詳解
- バージョン
- Revision
- 1
構築子と解体子
◆ LDAPStorageProvider()
|
inline |
関数詳解
◆ addUser()
|
inline |
org.keycloak.storage.user.UserRegistrationProviderを実装しています。
◆ authenticate()
|
inline |
org.keycloak.credential.CredentialAuthenticationを実装しています。
◆ checkDNChanged()
|
inlineprivate |
◆ close()
|
inline |
org.keycloak.provider.Providerを実装しています。
◆ disableCredentialType()
|
inline |
◆ findOrCreateAuthenticatedUser()
|
inlineprotected |
Called after successful kerberos authentication
- 引数
-
realm realm username username without realm prefix
- 戻り値
- finded or newly created user
◆ getDisableableCredentialTypes()
|
inline |
◆ getEditMode()
|
inline |
◆ getGroupMembers() [1/2]
|
inline |
org.keycloak.storage.user.UserQueryProviderを実装しています。
◆ getGroupMembers() [2/2]
|
inline |
org.keycloak.storage.user.UserQueryProviderを実装しています。
◆ getLdapIdentityStore()
|
inline |
◆ getMapperManager()
|
inline |
◆ getModel()
|
inline |
◆ getRoleMembers() [1/2]
|
inlineinherited |
Get users that belong to a specific role.
- 引数
-
realm role
- 戻り値
org.keycloak.models.jpa.JpaUserProvider, org.keycloak.models.cache.infinispan.UserCacheSession, org.keycloak.storage.UserStorageManagerで実装されています。
◆ getRoleMembers() [2/2]
|
inlineinherited |
Search for users that have a specific role with a specific roleId.
- 引数
-
firstResult maxResults role
- 戻り値
org.keycloak.models.jpa.JpaUserProvider, org.keycloak.storage.UserStorageManager, org.keycloak.models.cache.infinispan.UserCacheSessionで実装されています。
◆ getSession()
|
inline |
◆ getSupportedCredentialTypes()
|
inline |
◆ getUserByEmail()
|
inline |
org.keycloak.storage.user.UserLookupProviderを実装しています。
◆ getUserById()
|
inline |
org.keycloak.storage.user.UserLookupProviderを実装しています。
◆ getUserByUsername()
|
inline |
org.keycloak.storage.user.UserLookupProviderを実装しています。
◆ getUserManager()
|
inline |
◆ getUsers() [1/2]
|
inline |
◆ getUsers() [2/2]
|
inline |
◆ getUsersCount() [1/2]
|
inlineinherited |
Returns the number of users.
- 引数
-
realm the realm includeServiceAccount if true, the number of users will also include service accounts. Otherwise, only the number of users.
- 戻り値
- the number of users
org.keycloak.models.jpa.JpaUserProvider, org.keycloak.models.cache.infinispan.UserCacheSession, org.keycloak.storage.UserStorageManagerで実装されています。
◆ getUsersCount() [2/2]
|
inline |
◆ importUserFromLDAP()
|
inlineprotected |
◆ isConfiguredFor()
|
inline |
org.keycloak.credential.CredentialInputValidatorを実装しています。
◆ isValid()
|
inline |
org.keycloak.credential.CredentialInputValidatorを実装しています。
◆ loadAndValidateUser()
|
inlineprotected |
- 引数
-
local
- 戻り値
- ldapUser corresponding to local user or null if user is no longer in LDAP
◆ loadLDAPUserByUsername()
|
inline |
◆ loadUsersByUsernames()
|
inline |
◆ preRemove() [1/3]
|
inline |
◆ preRemove() [2/3]
|
inline |
◆ preRemove() [3/3]
|
inline |
◆ proxy()
|
inlineprotected |
◆ queryByEmail()
|
inlineprotected |
◆ removeUser()
|
inline |
org.keycloak.storage.user.UserRegistrationProviderを実装しています。
◆ searchForUser() [1/4]
|
inline |
org.keycloak.storage.user.UserQueryProviderを実装しています。
◆ searchForUser() [2/4]
|
inline |
org.keycloak.storage.user.UserQueryProviderを実装しています。
◆ searchForUser() [3/4]
|
inline |
org.keycloak.storage.user.UserQueryProviderを実装しています。
◆ searchForUser() [4/4]
|
inline |
org.keycloak.storage.user.UserQueryProviderを実装しています。
◆ searchForUserByUserAttribute()
|
inline |
org.keycloak.storage.user.UserQueryProviderを実装しています。
◆ searchLDAP()
|
inlineprotected |
◆ setUpdater()
|
inline |
◆ supportsCredentialAuthenticationFor()
|
inline |
org.keycloak.credential.CredentialAuthenticationを実装しています。
◆ supportsCredentialType()
|
inline |
org.keycloak.credential.CredentialInputUpdaterを実装しています。
◆ synchronizeRegistrations()
|
inline |
◆ updateCredential()
|
inline |
org.keycloak.credential.CredentialInputUpdaterを実装しています。
◆ validate()
|
inline |
org.keycloak.storage.user.ImportedUserValidationを実装しています。
◆ validPassword()
|
inline |
メンバ詳解
◆ editMode
|
protected |
◆ factory
|
protected |
◆ kerberosConfig
|
protected |
◆ ldapIdentityStore
|
protected |
◆ logger
|
staticprivate |
◆ mapperManager
|
protected |
◆ model
|
protected |
◆ session
|
protected |
◆ supportedCredentialTypes
|
protected |
◆ updater
|
protected |
◆ userManager
|
protected |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/src/keycloak/src/main/java/org/keycloak/storage/ldap/LDAPStorageProvider.java
 1.8.13
1.8.13