290 LDAPConfig ldapConfig =
new LDAPConfig(model.getConfig());
292 boolean activeDirectory = ldapConfig.isActiveDirectory();
293 UserStorageProvider.EditMode editMode = ldapConfig.getEditMode();
294 String readOnly = String.valueOf(editMode == UserStorageProvider.EditMode.READ_ONLY || editMode == UserStorageProvider.EditMode.UNSYNCED);
295 String usernameLdapAttribute = ldapConfig.getUsernameLdapAttribute();
297 String alwaysReadValueFromLDAP = String.valueOf(editMode== UserStorageProvider.EditMode.READ_ONLY || editMode== UserStorageProvider.EditMode.WRITABLE);
299 ComponentModel mapperModel;
300 mapperModel = KeycloakModelUtils.createComponentModel(
"username", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID, LDAPStorageMapper.class.getName(),
301 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, UserModel.USERNAME,
302 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, usernameLdapAttribute,
303 UserAttributeLDAPStorageMapper.READ_ONLY, readOnly,
304 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP,
"false",
305 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"true");
306 realm.addComponentModel(mapperModel);
309 if (ldapConfig.getRdnLdapAttribute().equalsIgnoreCase(LDAPConstants.CN)) {
311 if (usernameLdapAttribute.equalsIgnoreCase(LDAPConstants.CN)) {
314 mapperModel = KeycloakModelUtils.createComponentModel(
"first name", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
315 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, UserModel.FIRST_NAME,
316 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, LDAPConstants.GIVENNAME,
317 UserAttributeLDAPStorageMapper.READ_ONLY, readOnly,
318 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP, alwaysReadValueFromLDAP,
319 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"true");
320 realm.addComponentModel(mapperModel);
323 if (editMode == UserStorageProvider.EditMode.WRITABLE) {
326 mapperModel = KeycloakModelUtils.createComponentModel(
"first name", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
327 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, UserModel.FIRST_NAME,
328 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, LDAPConstants.GIVENNAME,
329 UserAttributeLDAPStorageMapper.READ_ONLY, readOnly,
330 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP, alwaysReadValueFromLDAP,
331 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"true");
332 realm.addComponentModel(mapperModel);
334 mapperModel = KeycloakModelUtils.createComponentModel(
"username-cn", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
335 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, UserModel.USERNAME,
336 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, LDAPConstants.CN,
337 UserAttributeLDAPStorageMapper.READ_ONLY, readOnly,
338 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP,
"false",
339 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"true");
340 realm.addComponentModel(mapperModel);
344 mapperModel = KeycloakModelUtils.createComponentModel(
"full name", model.getId(), FullNameLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
345 FullNameLDAPStorageMapper.LDAP_FULL_NAME_ATTRIBUTE, LDAPConstants.CN,
346 FullNameLDAPStorageMapper.READ_ONLY, readOnly,
347 FullNameLDAPStorageMapper.WRITE_ONLY,
"false");
348 realm.addComponentModel(mapperModel);
352 mapperModel = KeycloakModelUtils.createComponentModel(
"first name", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
353 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, UserModel.FIRST_NAME,
354 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, LDAPConstants.CN,
355 UserAttributeLDAPStorageMapper.READ_ONLY, readOnly,
356 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP, alwaysReadValueFromLDAP,
357 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"true");
358 realm.addComponentModel(mapperModel);
361 mapperModel = KeycloakModelUtils.createComponentModel(
"last name", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
362 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, UserModel.LAST_NAME,
363 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, LDAPConstants.SN,
364 UserAttributeLDAPStorageMapper.READ_ONLY, readOnly,
365 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP, alwaysReadValueFromLDAP,
366 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"true");
367 realm.addComponentModel(mapperModel);
369 mapperModel = KeycloakModelUtils.createComponentModel(
"email", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
370 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, UserModel.EMAIL,
371 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, LDAPConstants.EMAIL,
372 UserAttributeLDAPStorageMapper.READ_ONLY, readOnly,
373 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP,
"false",
374 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"false");
375 realm.addComponentModel(mapperModel);
377 String createTimestampLdapAttrName = activeDirectory ?
"whenCreated" : LDAPConstants.CREATE_TIMESTAMP;
378 String modifyTimestampLdapAttrName = activeDirectory ?
"whenChanged" : LDAPConstants.MODIFY_TIMESTAMP;
381 mapperModel = KeycloakModelUtils.createComponentModel(
"creation date", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
382 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, LDAPConstants.CREATE_TIMESTAMP,
383 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, createTimestampLdapAttrName,
384 UserAttributeLDAPStorageMapper.READ_ONLY,
"true",
385 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP, alwaysReadValueFromLDAP,
386 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"false");
387 realm.addComponentModel(mapperModel);
390 mapperModel = KeycloakModelUtils.createComponentModel(
"modify date", model.getId(), UserAttributeLDAPStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName(),
391 UserAttributeLDAPStorageMapper.USER_MODEL_ATTRIBUTE, LDAPConstants.MODIFY_TIMESTAMP,
392 UserAttributeLDAPStorageMapper.LDAP_ATTRIBUTE, modifyTimestampLdapAttrName,
393 UserAttributeLDAPStorageMapper.READ_ONLY,
"true",
394 UserAttributeLDAPStorageMapper.ALWAYS_READ_VALUE_FROM_LDAP, alwaysReadValueFromLDAP,
395 UserAttributeLDAPStorageMapper.IS_MANDATORY_IN_LDAP,
"false");
396 realm.addComponentModel(mapperModel);
399 if (activeDirectory) {
400 mapperModel = KeycloakModelUtils.createComponentModel(
"MSAD account controls", model.getId(), MSADUserAccountControlStorageMapperFactory.PROVIDER_ID,LDAPStorageMapper.class.getName());
401 realm.addComponentModel(mapperModel);
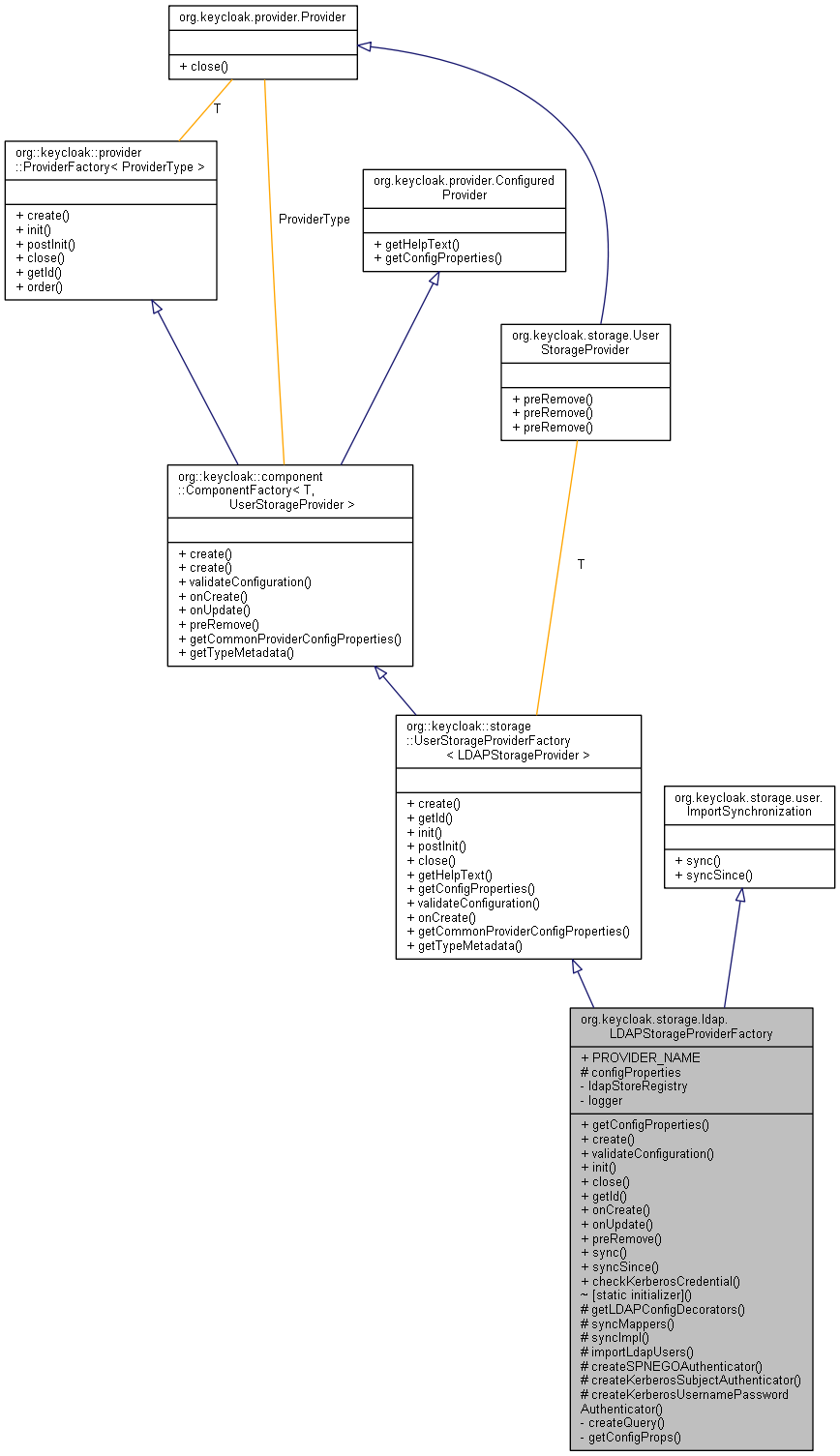
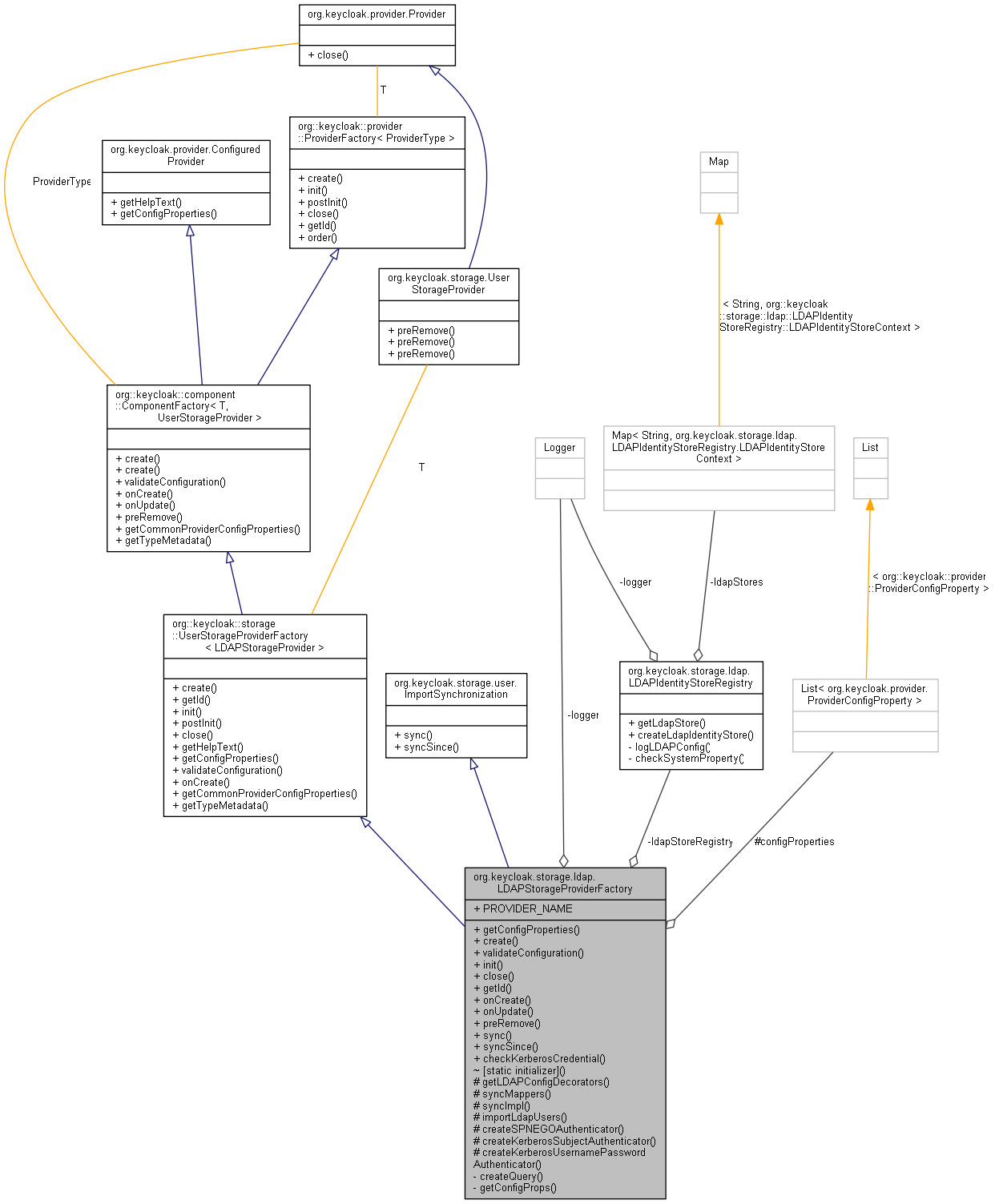
static boolean checkKerberosCredential(KeycloakSession session, RealmModel realm, ComponentModel model)
Definition: LDAPStorageProviderFactory.java:629
 1.8.13
1.8.13