org.mitre.openid.connect.request.ConnectOAuth2RequestFactory の継承関係図
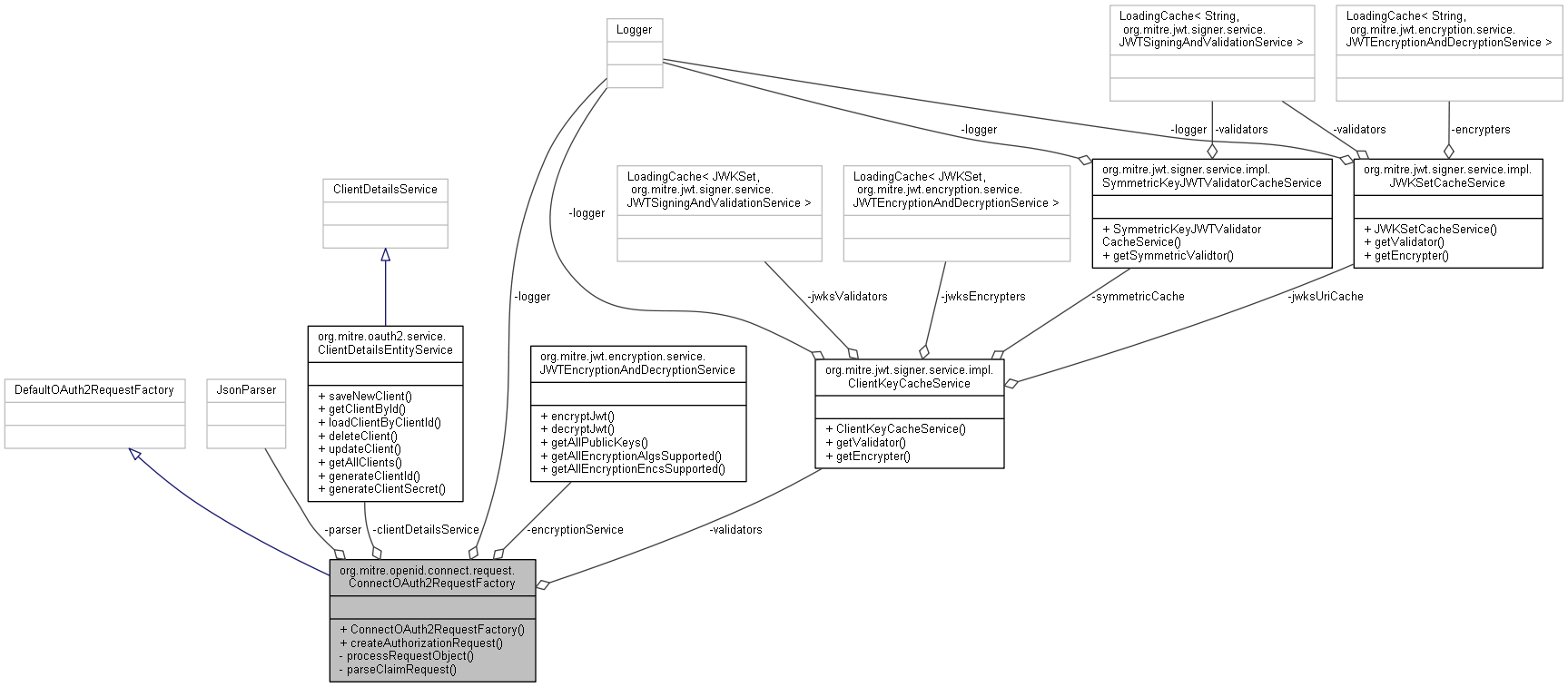
org.mitre.openid.connect.request.ConnectOAuth2RequestFactory 連携図
公開メンバ関数 | |
| ConnectOAuth2RequestFactory (ClientDetailsEntityService clientDetailsService) | |
| AuthorizationRequest | createAuthorizationRequest (Map< String, String > inputParams) |
非公開メンバ関数 | |
| void | processRequestObject (String jwtString, AuthorizationRequest request) |
| JsonObject | parseClaimRequest (String claimRequestString) |
非公開変数類 | |
| ClientDetailsEntityService | clientDetailsService |
| ClientKeyCacheService | validators |
| JWTEncryptionAndDecryptionService | encryptionService |
| JsonParser | parser = new JsonParser() |
静的非公開変数類 | |
| static final Logger | logger = LoggerFactory.getLogger(ConnectOAuth2RequestFactory.class) |
詳解
構築子と解体子
◆ ConnectOAuth2RequestFactory()
|
inline |
Constructor with arguments
- 引数
-
clientDetailsService
ClientDetailsEntityService clientDetailsService
Definition: ConnectOAuth2RequestFactory.java:81
関数詳解
◆ createAuthorizationRequest()
|
inline |
106 AuthorizationRequest request = new AuthorizationRequest(inputParams, Collections.<String, String> emptyMap(),
ClientDetailsEntityService clientDetailsService
Definition: ConnectOAuth2RequestFactory.java:81
Set< String > getScope()
Definition: ClientDetailsEntity.java:439
JsonObject parseClaimRequest(String claimRequestString)
Definition: ConnectOAuth2RequestFactory.java:364
static final Logger logger
Definition: ConnectOAuth2RequestFactory.java:79
void processRequestObject(String jwtString, AuthorizationRequest request)
Definition: ConnectOAuth2RequestFactory.java:182
ClientDetailsEntity loadClientByClientId(String clientId)
◆ parseClaimRequest()
|
inlineprivate |
- 引数
-
claimRequestString
- 戻り値
JsonParser parser
Definition: ConnectOAuth2RequestFactory.java:89
◆ processRequestObject()
|
inlineprivate |
- 引数
-
jwtString request
209 throw new InvalidClientException("Client's registered request object signing algorithm (" + client.getRequestObjectSigningAlg() + ") does not match request object's actual algorithm (" + alg.getName() + ")");
215 throw new InvalidClientException("Unable to create signature validator for client " + client + " and algorithm " + alg);
219 throw new InvalidClientException("Signature did not validate for presented JWT request object.");
237 throw new InvalidClientException("Client is not registered for unsigned request objects (no request_object_signing_alg registered)");
239 throw new InvalidClientException("Client is not registered for unsigned request objects (request_object_signing_alg is " + client.getRequestObjectSigningAlg() +")");
274 * NOTE: Claims inside the request object always take precedence over those in the parameter map.
277 // now that we've got the JWT, and it's been parsed, validated, and/or decrypted, we can process the claims
281 Set<String> responseTypes = OAuth2Utils.parseParameterList(claims.getStringClaim(RESPONSE_TYPE));
284 logger.info("Mismatch between request object and regular parameter for response_type, using request object");
292 logger.info("Mismatch between request object and regular parameter for redirect_uri, using request object");
300 logger.info("Mismatch between request object and regular parameter for state, using request object");
308 logger.info("Mismatch between request object and regular parameter for nonce, using request object");
316 logger.info("Mismatch between request object and regular parameter for display, using request object");
324 logger.info("Mismatch between request object and regular parameter for prompt, using request object");
332 logger.info("Mismatch between request object and regular parameter for scope, using request object");
340 if (claimExtension == null || !claimRequest.equals(parseClaimRequest(claimExtension.toString()))) {
341 logger.info("Mismatch between request object and regular parameter for claims, using request object");
343 // we save the string because the object might not be a Java Serializable, and we can parse it easily enough anyway
350 logger.info("Mistmatch between request object and regular parameter for login_hint, using requst object");
ClientDetailsEntityService clientDetailsService
Definition: ConnectOAuth2RequestFactory.java:81
void decryptJwt(JWEObject jwt)
JsonObject parseClaimRequest(String claimRequestString)
Definition: ConnectOAuth2RequestFactory.java:364
static final Logger logger
Definition: ConnectOAuth2RequestFactory.java:79
ClientKeyCacheService validators
Definition: ConnectOAuth2RequestFactory.java:84
JWTSigningAndValidationService getValidator(ClientDetailsEntity client, JWSAlgorithm alg)
Definition: ClientKeyCacheService.java:77
JWTEncryptionAndDecryptionService encryptionService
Definition: ConnectOAuth2RequestFactory.java:87
ClientDetailsEntity loadClientByClientId(String clientId)
メンバ詳解
◆ clientDetailsService
|
private |
◆ encryptionService
|
private |
◆ logger
|
staticprivate |
Logger for this class
◆ parser
|
private |
◆ validators
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/mitreid-connect/src/openid-connect-server/src/main/java/org/mitre/openid/connect/request/ConnectOAuth2RequestFactory.java
 1.8.13
1.8.13