185 if (authentication != null && authentication.getOAuth2Request() != null) {
187 OAuth2Request request = authentication.getOAuth2Request();
191 if (client == null) {
192 throw new InvalidClientException(
"Client not found: " + request.getClientId());
197 if (request.getExtensions().containsKey(CODE_CHALLENGE)) {
198 String challenge = (String) request.getExtensions().get(CODE_CHALLENGE);
199 PKCEAlgorithm alg = PKCEAlgorithm.parse((String) request.getExtensions().get(CODE_CHALLENGE_METHOD));
201 String verifier = request.getRequestParameters().get(CODE_VERIFIER);
203 if (alg.equals(PKCEAlgorithm.plain)) {
205 if (!challenge.equals(verifier)) {
206 throw new InvalidRequestException(
"Code challenge and verifier do not match");
208 }
else if (alg.equals(PKCEAlgorithm.S256)) {
211 MessageDigest digest = MessageDigest.getInstance(
"SHA-256");
212 String hash = Base64URL.encode(digest.digest(verifier.getBytes(StandardCharsets.US_ASCII))).toString();
213 if (!challenge.equals(hash)) {
214 throw new InvalidRequestException(
"Code challenge and verifier do not match");
216 }
catch (NoSuchAlgorithmException e) {
217 logger.error(
"Unknown algorithm for PKCE digest", e);
224 OAuth2AccessTokenEntity token =
new OAuth2AccessTokenEntity();
227 token.setClient(client);
240 if (client.getAccessTokenValiditySeconds() != null && client.getAccessTokenValiditySeconds() > 0) {
241 Date expiration =
new Date(System.currentTimeMillis() + (client.getAccessTokenValiditySeconds() * 1000L));
242 token.setExpiration(expiration);
246 AuthenticationHolderEntity authHolder =
new AuthenticationHolderEntity();
247 authHolder.setAuthentication(authentication);
250 token.setAuthenticationHolder(authHolder);
253 if (client.isAllowRefresh() && token.getScope().contains(SystemScopeService.OFFLINE_ACCESS)) {
256 token.setRefreshToken(savedRefreshToken);
260 OAuth2Request originalAuthRequest = authHolder.getAuthentication().getOAuth2Request();
262 if (originalAuthRequest.getExtensions() != null && originalAuthRequest.getExtensions().containsKey(
"approved_site")) {
264 Long apId = Long.parseLong((String) originalAuthRequest.getExtensions().get(
"approved_site"));
267 token.setApprovedSite(ap);
270 OAuth2AccessTokenEntity enhancedToken = (OAuth2AccessTokenEntity)
tokenEnhancer.enhance(token, authentication);
274 if (savedToken.getRefreshToken() != null) {
281 throw new AuthenticationCredentialsNotFoundException(
"No authentication credentials found");
OAuth2AccessTokenEntity saveAccessToken(OAuth2AccessTokenEntity accessToken)
Definition: DefaultOAuth2ProviderTokenService.java:550
OAuth2RefreshTokenEntity createRefreshToken(ClientDetailsEntity client, AuthenticationHolderEntity authHolder)
Definition: DefaultOAuth2ProviderTokenService.java:285
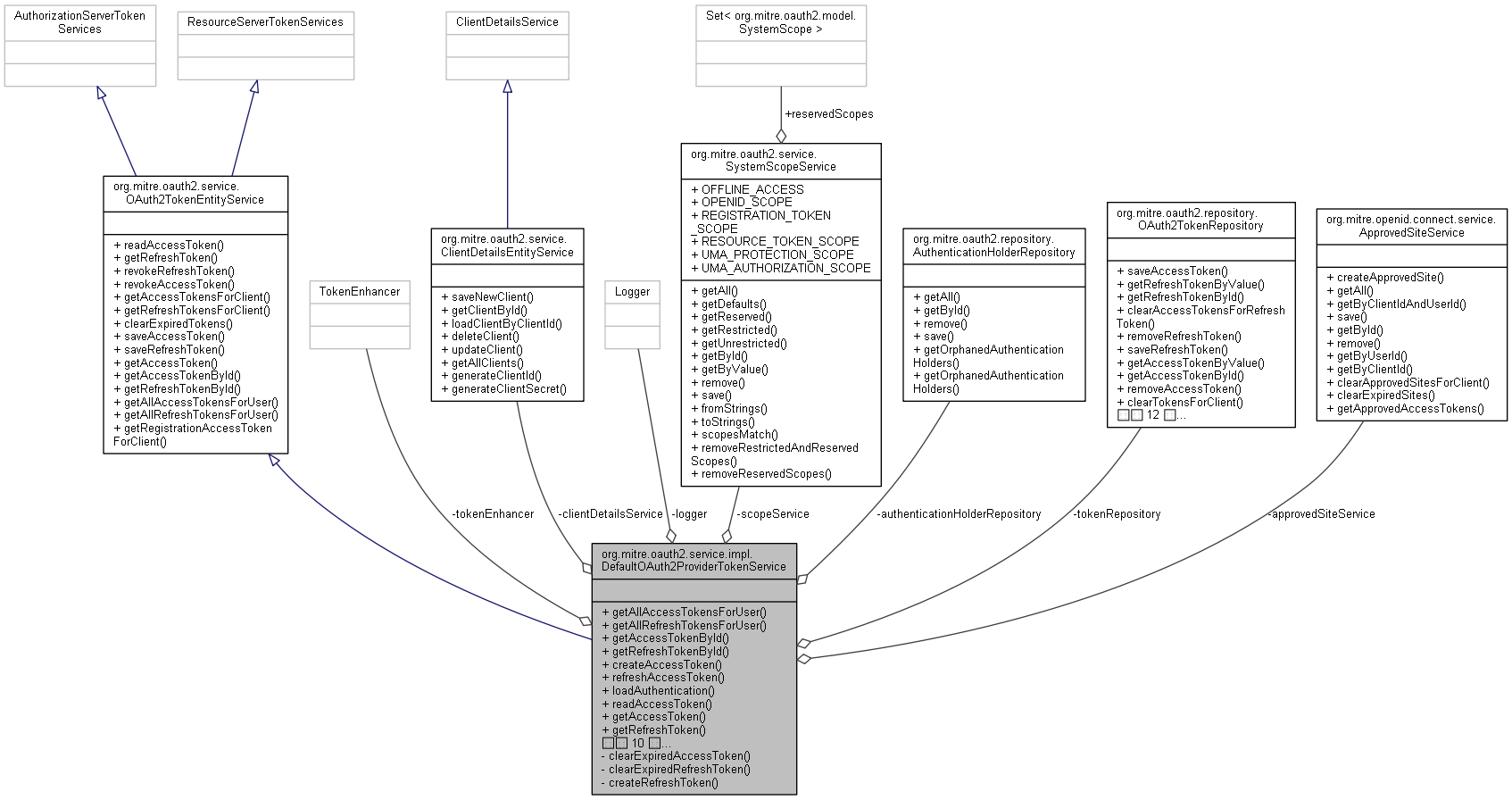
AuthenticationHolderRepository authenticationHolderRepository
Definition: DefaultOAuth2ProviderTokenService.java:91
OAuth2RefreshTokenEntity saveRefreshToken(OAuth2RefreshTokenEntity refreshToken)
Set< SystemScope > removeReservedScopes(Set< SystemScope > scopes)
ClientDetailsEntityService clientDetailsService
Definition: DefaultOAuth2ProviderTokenService.java:94
ApprovedSite getById(Long id)
OAuth2TokenRepository tokenRepository
Definition: DefaultOAuth2ProviderTokenService.java:88
AuthenticationHolderEntity save(AuthenticationHolderEntity a)
Set< SystemScope > fromStrings(Set< String > scope)
TokenEnhancer tokenEnhancer
Definition: DefaultOAuth2ProviderTokenService.java:97
static final Logger logger
Definition: DefaultOAuth2ProviderTokenService.java:85
SystemScopeService scopeService
Definition: DefaultOAuth2ProviderTokenService.java:100
ApprovedSiteService approvedSiteService
Definition: DefaultOAuth2ProviderTokenService.java:103
Set< String > toStrings(Set< SystemScope > scope)
ClientDetailsEntity loadClientByClientId(String clientId)
 1.8.13
1.8.13