org.mitre.openid.connect.web.DynamicClientRegistrationEndpoint 連携図
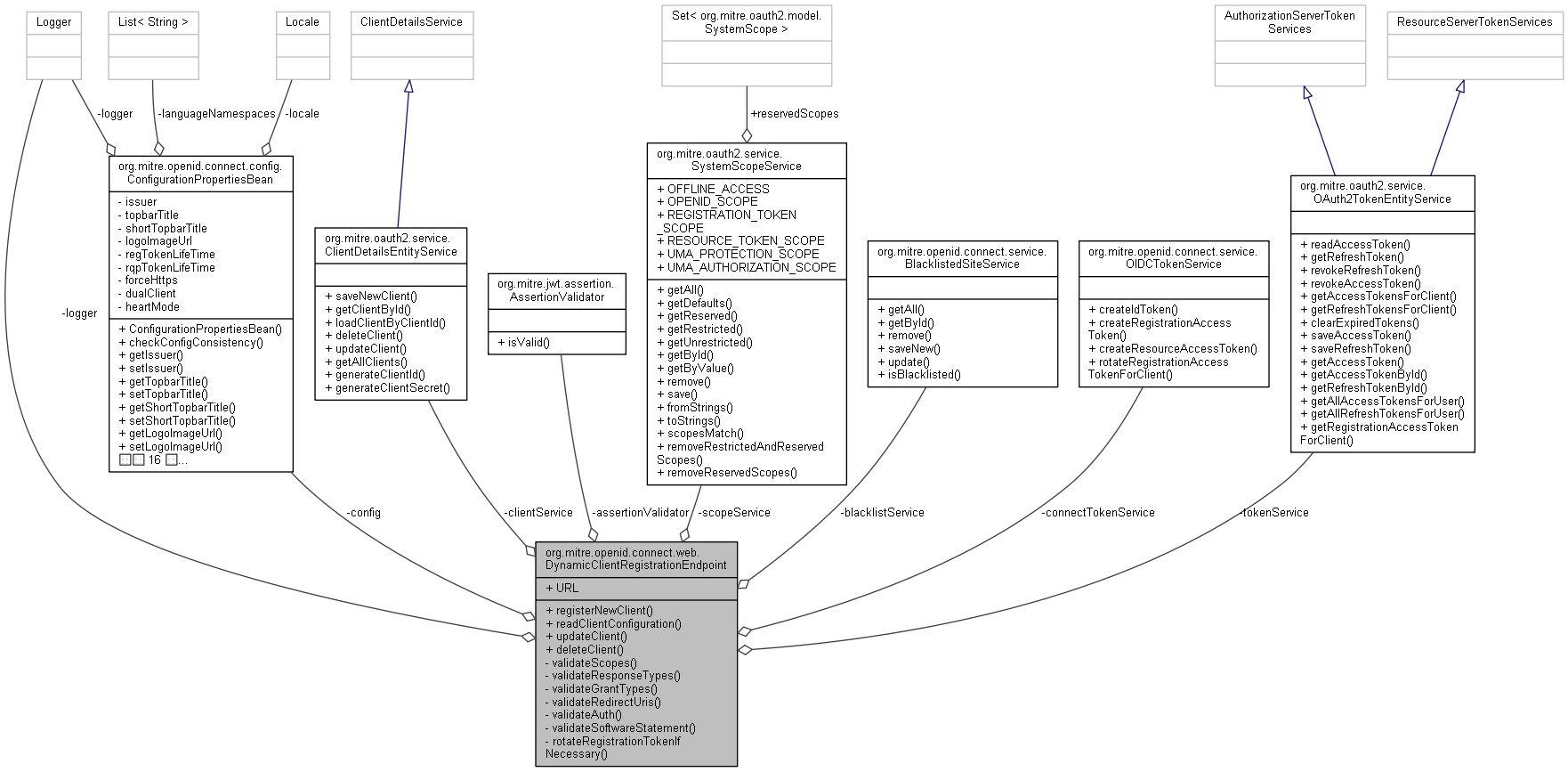
公開メンバ関数 | |
| String | registerNewClient (@RequestBody String jsonString, Model m) |
| String | readClientConfiguration (@PathVariable("id") String clientId, Model m, OAuth2Authentication auth) |
| String | updateClient (@PathVariable("id") String clientId, @RequestBody String jsonString, Model m, OAuth2Authentication auth) |
| String | deleteClient (@PathVariable("id") String clientId, Model m, OAuth2Authentication auth) |
静的公開変数類 | |
| static final String | URL = "register" |
非公開メンバ関数 | |
| ClientDetailsEntity | validateScopes (ClientDetailsEntity newClient) throws ValidationException |
| ClientDetailsEntity | validateResponseTypes (ClientDetailsEntity newClient) throws ValidationException |
| ClientDetailsEntity | validateGrantTypes (ClientDetailsEntity newClient) throws ValidationException |
| ClientDetailsEntity | validateRedirectUris (ClientDetailsEntity newClient) throws ValidationException |
| ClientDetailsEntity | validateAuth (ClientDetailsEntity newClient) throws ValidationException |
| ClientDetailsEntity | validateSoftwareStatement (ClientDetailsEntity newClient) throws ValidationException |
| OAuth2AccessTokenEntity | rotateRegistrationTokenIfNecessary (OAuth2Authentication auth, ClientDetailsEntity client) |
静的非公開変数類 | |
| static final Logger | logger = LoggerFactory.getLogger(DynamicClientRegistrationEndpoint.class) |
詳解
関数詳解
◆ deleteClient()
|
inline |
Delete the indicated client from the system.
- 引数
-
clientId m auth
- 戻り値
static final Logger logger
Definition: DynamicClientRegistrationEndpoint.java:144
void deleteClient(ClientDetailsEntity client)
ClientDetailsEntity loadClientByClientId(String clientId)
ClientDetailsEntityService clientService
Definition: DynamicClientRegistrationEndpoint.java:120
◆ readClientConfiguration()
|
inline |
Get the meta information for a client.
- 引数
-
clientId m auth
- 戻り値
289 RegisteredClient registered = new RegisteredClient(client, token.getValue(), config.getIssuer() + "register/" + UriUtils.encodePathSegment(client.getClientId(), "UTF-8"));
OAuth2AccessTokenEntity rotateRegistrationTokenIfNecessary(OAuth2Authentication auth, ClientDetailsEntity client)
Definition: DynamicClientRegistrationEndpoint.java:756
ConfigurationPropertiesBean config
Definition: DynamicClientRegistrationEndpoint.java:132
static final Logger logger
Definition: DynamicClientRegistrationEndpoint.java:144
ClientDetailsEntity loadClientByClientId(String clientId)
String getIssuer()
Definition: ConfigurationPropertiesBean.java:100
ClientDetailsEntityService clientService
Definition: DynamicClientRegistrationEndpoint.java:120
◆ registerNewClient()
|
inline |
Create a new Client, issue a client ID, and create a registration access token.
- 引数
-
jsonString m p
- 戻り値
180 newClient = validateSoftwareStatement(newClient); // need to handle the software statement first because it might override requested values
210 newClient.setAccessTokenValiditySeconds((int)TimeUnit.HOURS.toSeconds(1)); // access tokens good for 1hr
211 newClient.setIdTokenValiditySeconds((int)TimeUnit.MINUTES.toSeconds(5)); // id tokens good for 5min
212 newClient.setRefreshTokenValiditySeconds((int)TimeUnit.HOURS.toSeconds(24)); // refresh tokens good for 24hr
214 newClient.setAccessTokenValiditySeconds((int)TimeUnit.MINUTES.toSeconds(15)); // access tokens good for 15min
215 newClient.setIdTokenValiditySeconds((int)TimeUnit.MINUTES.toSeconds(5)); // id tokens good for 5min
218 newClient.setAccessTokenValiditySeconds((int)TimeUnit.HOURS.toSeconds(6)); // access tokens good for 6hr
223 newClient.setAccessTokenValiditySeconds((int)TimeUnit.HOURS.toSeconds(1)); // access tokens good for 1hr
224 newClient.setIdTokenValiditySeconds((int)TimeUnit.MINUTES.toSeconds(10)); // id tokens good for 10min
244 RegisteredClient registered = new RegisteredClient(savedClient, token.getValue(), config.getIssuer() + "register/" + UriUtils.encodePathSegment(savedClient.getClientId(), "UTF-8"));
257 m.addAttribute(JsonErrorView.ERROR_MESSAGE, "Unable to save client due to invalid or inconsistent metadata.");
OAuth2AccessTokenEntity saveAccessToken(OAuth2AccessTokenEntity accessToken)
ClientDetailsEntity saveNewClient(ClientDetailsEntity client)
ConfigurationPropertiesBean config
Definition: DynamicClientRegistrationEndpoint.java:132
static final Logger logger
Definition: DynamicClientRegistrationEndpoint.java:144
ClientDetailsEntity validateGrantTypes(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:462
ClientDetailsEntity validateSoftwareStatement(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:614
void setAccessTokenValiditySeconds(Integer accessTokenValiditySeconds)
Definition: ClientDetailsEntity.java:511
ClientDetailsEntity validateScopes(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:438
ClientDetailsEntity validateRedirectUris(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:557
OAuth2TokenEntityService tokenService
Definition: DynamicClientRegistrationEndpoint.java:123
ClientDetailsEntity validateResponseTypes(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:455
OAuth2AccessTokenEntity createRegistrationAccessToken(ClientDetailsEntity client)
ClientDetailsEntity generateClientSecret(ClientDetailsEntity client)
ClientDetailsEntity validateAuth(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:581
OIDCTokenService connectTokenService
Definition: DynamicClientRegistrationEndpoint.java:135
String getIssuer()
Definition: ConfigurationPropertiesBean.java:100
boolean isHeartMode()
Definition: ConfigurationPropertiesBean.java:250
ClientDetailsEntityService clientService
Definition: DynamicClientRegistrationEndpoint.java:120
◆ rotateRegistrationTokenIfNecessary()
|
inlineprivate |
OAuth2AccessTokenEntity saveAccessToken(OAuth2AccessTokenEntity accessToken)
ConfigurationPropertiesBean config
Definition: DynamicClientRegistrationEndpoint.java:132
static final Logger logger
Definition: DynamicClientRegistrationEndpoint.java:144
Long getRegTokenLifeTime()
Definition: ConfigurationPropertiesBean.java:153
OAuth2TokenEntityService tokenService
Definition: DynamicClientRegistrationEndpoint.java:123
OAuth2AccessTokenEntity createRegistrationAccessToken(ClientDetailsEntity client)
OAuth2AccessTokenEntity readAccessToken(String accessTokenValue)
OIDCTokenService connectTokenService
Definition: DynamicClientRegistrationEndpoint.java:135
void revokeAccessToken(OAuth2AccessTokenEntity accessToken)
◆ updateClient()
|
inline |
Update the metainformation for a given client.
- 引数
-
clientId jsonString m auth
- 戻り値
338 && oldClient.getClientId().equals(auth.getOAuth2Request().getClientId()) // the client passed in the URI matches the one in the auth
339 && oldClient.getClientId().equals(newClient.getClientId()) // the client passed in the body matches the one in the URI
350 newClient.setAllowIntrospection(false); // dynamically registered clients can't do introspection -- use the resource registration instead
358 newClient = validateSoftwareStatement(newClient); // need to handle the software statement first because it might override requested values
378 RegisteredClient registered = new RegisteredClient(savedClient, token.getValue(), config.getIssuer() + "register/" + UriUtils.encodePathSegment(savedClient.getClientId(), "UTF-8"));
393 m.addAttribute(JsonErrorView.ERROR_MESSAGE, "Unable to save client due to invalid or inconsistent metadata.");
OAuth2AccessTokenEntity rotateRegistrationTokenIfNecessary(OAuth2Authentication auth, ClientDetailsEntity client)
Definition: DynamicClientRegistrationEndpoint.java:756
void setClientSecret(String clientSecret)
Definition: ClientDetailsEntity.java:425
ConfigurationPropertiesBean config
Definition: DynamicClientRegistrationEndpoint.java:132
static final Logger logger
Definition: DynamicClientRegistrationEndpoint.java:144
ClientDetailsEntity validateGrantTypes(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:462
ClientDetailsEntity updateClient(ClientDetailsEntity oldClient, ClientDetailsEntity newClient)
ClientDetailsEntity validateSoftwareStatement(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:614
ClientDetailsEntity validateScopes(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:438
ClientDetailsEntity validateRedirectUris(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:557
ClientDetailsEntity validateResponseTypes(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:455
ClientDetailsEntity validateAuth(ClientDetailsEntity newClient)
Definition: DynamicClientRegistrationEndpoint.java:581
ClientDetailsEntity loadClientByClientId(String clientId)
String getIssuer()
Definition: ConfigurationPropertiesBean.java:100
ClientDetailsEntityService clientService
Definition: DynamicClientRegistrationEndpoint.java:120
◆ validateAuth()
|
inlineprivate |
596 throw new ValidationException("invalid_client_metadata", "JWK Set URI required when using private key authentication", HttpStatus.BAD_REQUEST);
603 throw new ValidationException("invalid_client_metadata", "Unknown authentication method", HttpStatus.BAD_REQUEST);
ClientDetailsEntity generateClientSecret(ClientDetailsEntity client)
ClientDetailsEntityService clientService
Definition: DynamicClientRegistrationEndpoint.java:120
◆ validateGrantTypes()
|
inlineprivate |
466 newClient.setGrantTypes(Sets.newHashSet("authorization_code", "refresh_token")); // allow authorization code and refresh token grant types by default
468 newClient.setGrantTypes(Sets.newHashSet("authorization_code")); // allow authorization code grant type by default
488 throw new ValidationException("invalid_client_metadata", "The password grant type is not allowed in dynamic registration on this server.", HttpStatus.BAD_REQUEST);
498 throw new ValidationException("invalid_client_metadata", "Incompatible grant types requested: " + newClient.getGrantTypes(), HttpStatus.BAD_REQUEST);
503 throw new ValidationException("invalid_client_metadata", "Incompatible response types requested: " + newClient.getGrantTypes() + " / " + newClient.getResponseTypes(), HttpStatus.BAD_REQUEST);
515 throw new ValidationException("invalid_client_metadata", "Incompatible grant types requested: " + newClient.getGrantTypes(), HttpStatus.BAD_REQUEST);
520 throw new ValidationException("invalid_client_metadata", "Incompatible response types requested: " + newClient.getGrantTypes() + " / " + newClient.getResponseTypes(), HttpStatus.BAD_REQUEST);
534 (newClient.getGrantTypes().contains("authorization_code") || newClient.getGrantTypes().contains("implicit"))) {
536 throw new ValidationException("invalid_client_metadata", "Incompatible grant types requested: " + newClient.getGrantTypes(), HttpStatus.BAD_REQUEST);
541 throw new ValidationException("invalid_client_metadata", "Incompatible response types requested: " + newClient.getGrantTypes() + " / " + newClient.getResponseTypes(), HttpStatus.BAD_REQUEST);
552 throw new ValidationException("invalid_client_metadata", "Clients must register at least one grant type.", HttpStatus.BAD_REQUEST);
boolean isDualClient()
Definition: ConfigurationPropertiesBean.java:217
ConfigurationPropertiesBean config
Definition: DynamicClientRegistrationEndpoint.java:132
◆ validateRedirectUris()
|
inlineprivate |
559 if (newClient.getGrantTypes().contains("authorization_code") || newClient.getGrantTypes().contains("implicit")) {
562 throw new ValidationException("invalid_redirect_uri", "Clients using a redirect-based grant type must register at least one redirect URI.", HttpStatus.BAD_REQUEST);
568 throw new ValidationException("invalid_redirect_uri", "Redirect URI is not allowed: " + uri, HttpStatus.BAD_REQUEST);
573 throw new ValidationException("invalid_redirect_uri", "Redirect URI can not have a fragment", HttpStatus.BAD_REQUEST);
BlacklistedSiteService blacklistService
Definition: DynamicClientRegistrationEndpoint.java:129
boolean isBlacklisted(String uri)
◆ validateResponseTypes()
|
inlineprivate |
◆ validateScopes()
|
inlineprivate |
443 Set<SystemScope> allowedScopes = scopeService.removeRestrictedAndReservedScopes(requestedScopes);
SystemScopeService scopeService
Definition: DynamicClientRegistrationEndpoint.java:126
Set< SystemScope > removeRestrictedAndReservedScopes(Set< SystemScope > scopes)
Set< SystemScope > fromStrings(Set< String > scope)
Set< SystemScope > getDefaults()
Set< String > toStrings(Set< SystemScope > scope)
◆ validateSoftwareStatement()
|
inlineprivate |
- 引数
-
newClient
- 戻り値
- 例外
-
ValidationException
625 throw new ValidationException("invalid_client_metadata", "Software statement can't include another software statement", HttpStatus.BAD_REQUEST);
630 throw new ValidationException("invalid_client_metadata", "Software statement can't include a client secret expiration time", HttpStatus.BAD_REQUEST);
632 throw new ValidationException("invalid_client_metadata", "Software statement can't include a client ID issuance time", HttpStatus.BAD_REQUEST);
634 throw new ValidationException("invalid_client_metadata", "Software statement can't include a client configuration endpoint", HttpStatus.BAD_REQUEST);
636 throw new ValidationException("invalid_client_metadata", "Software statement can't include a client registration access token", HttpStatus.BAD_REQUEST);
659 newClient.setIdTokenEncryptedResponseEnc(EncryptionMethod.parse(claimSet.getStringClaim(claim)));
668 newClient.setUserInfoEncryptedResponseEnc(EncryptionMethod.parse(claimSet.getStringClaim(claim)));
728 throw new ValidationException("invalid_client_metadata", "Software statement can't contain client secret", HttpStatus.BAD_REQUEST);
730 throw new ValidationException("invalid_client_metadata", "Software statement can't contain client ID", HttpStatus.BAD_REQUEST);
733 logger.warn("Software statement contained unknown field: " + claim + " with value " + claimSet.getClaim(claim));
740 throw new ValidationException("invalid_client_metadata", "Software statement claims didn't parse", HttpStatus.BAD_REQUEST);
743 throw new ValidationException("invalid_client_metadata", "Software statement rejected by validator", HttpStatus.BAD_REQUEST);
static final Logger logger
Definition: DynamicClientRegistrationEndpoint.java:144
boolean isValid(JWT assertion)
AssertionValidator assertionValidator
Definition: DynamicClientRegistrationEndpoint.java:139
メンバ詳解
◆ assertionValidator
|
private |
◆ blacklistService
|
private |
◆ clientService
|
private |
◆ config
|
private |
◆ connectTokenService
|
private |
◆ logger
|
staticprivate |
Logger for this class
◆ scopeService
|
private |
◆ tokenService
|
private |
◆ URL
|
static |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/mitreid-connect/src/openid-connect-server/src/main/java/org/mitre/openid/connect/web/DynamicClientRegistrationEndpoint.java
 1.8.13
1.8.13