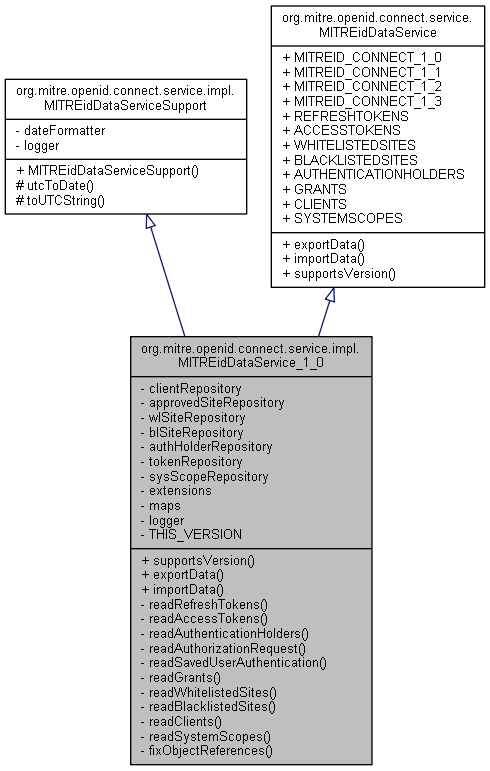
org.mitre.openid.connect.service.impl.MITREidDataService_1_0 の継承関係図
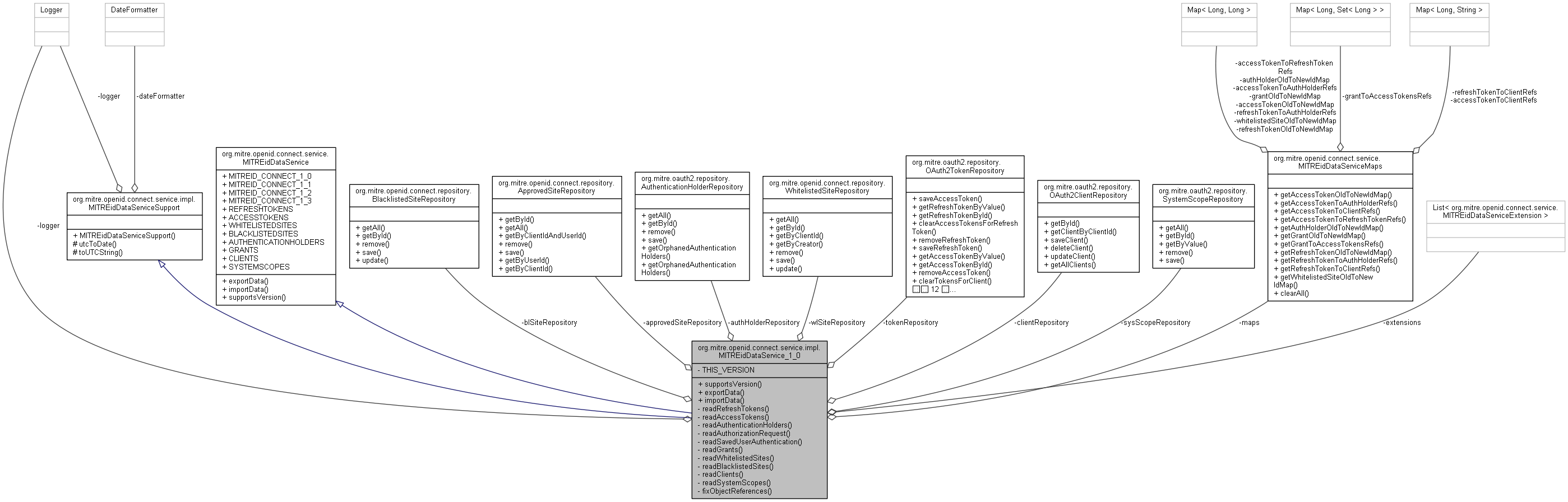
org.mitre.openid.connect.service.impl.MITREidDataService_1_0 連携図
公開メンバ関数 | |
| boolean | supportsVersion (String version) |
| void | exportData (JsonWriter writer) throws IOException |
| void | importData (JsonReader reader) throws IOException |
静的公開変数類 | |
| static final String | MITREID_CONNECT_1_0 = "mitreid-connect-1.0" |
| static final String | MITREID_CONNECT_1_1 = "mitreid-connect-1.1" |
| static final String | MITREID_CONNECT_1_2 = "mitreid-connect-1.2" |
| static final String | MITREID_CONNECT_1_3 = "mitreid-connect-1.3" |
| static final String | REFRESHTOKENS = "refreshTokens" |
| static final String | ACCESSTOKENS = "accessTokens" |
| static final String | WHITELISTEDSITES = "whitelistedSites" |
| static final String | BLACKLISTEDSITES = "blacklistedSites" |
| static final String | AUTHENTICATIONHOLDERS = "authenticationHolders" |
| static final String | GRANTS = "grants" |
| static final String | CLIENTS = "clients" |
| static final String | SYSTEMSCOPES = "systemScopes" |
限定公開メンバ関数 | |
| Date | utcToDate (String value) |
| String | toUTCString (Date value) |
非公開メンバ関数 | |
| void | readRefreshTokens (JsonReader reader) throws IOException |
| void | readAccessTokens (JsonReader reader) throws IOException |
| void | readAuthenticationHolders (JsonReader reader) throws IOException |
| OAuth2Request | readAuthorizationRequest (JsonReader reader) throws IOException |
| SavedUserAuthentication | readSavedUserAuthentication (JsonReader reader) throws IOException |
| void | readGrants (JsonReader reader) throws IOException |
| void | readWhitelistedSites (JsonReader reader) throws IOException |
| void | readBlacklistedSites (JsonReader reader) throws IOException |
| void | readClients (JsonReader reader) throws IOException |
| void | readSystemScopes (JsonReader reader) throws IOException |
| void | fixObjectReferences () |
静的非公開変数類 | |
| static final Logger | logger = LoggerFactory.getLogger(MITREidDataService_1_0.class) |
| static final String | THIS_VERSION = MITREID_CONNECT_1_0 |
詳解
Data service to import MITREid 1.0 configuration.
関数詳解
◆ exportData()
|
inline |
◆ fixObjectReferences()
|
inlineprivate |
MITREidDataServiceMaps maps
Definition: MITREidDataService_1_0.java:107
OAuth2AccessTokenEntity saveAccessToken(OAuth2AccessTokenEntity token)
Map< Long, Long > getAccessTokenToAuthHolderRefs()
Definition: MITREidDataServiceMaps.java:49
Map< Long, String > getRefreshTokenToClientRefs()
Definition: MITREidDataServiceMaps.java:97
Map< Long, Long > getGrantOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:73
ClientDetailsEntity getClientByClientId(String clientId)
void setApprovedSite(ApprovedSite approvedSite)
Definition: OAuth2AccessTokenEntity.java:318
Map< Long, Long > getAccessTokenToRefreshTokenRefs()
Definition: MITREidDataServiceMaps.java:61
void setClient(ClientDetailsEntity client)
Definition: OAuth2AccessTokenEntity.java:184
OAuth2AccessTokenEntity getAccessTokenById(Long id)
OAuth2TokenRepository tokenRepository
Definition: MITREidDataService_1_0.java:101
ApprovedSite save(ApprovedSite approvedSite)
ApprovedSiteRepository approvedSiteRepository
Definition: MITREidDataService_1_0.java:93
Map< Long, String > getAccessTokenToClientRefs()
Definition: MITREidDataServiceMaps.java:55
OAuth2RefreshTokenEntity saveRefreshToken(OAuth2RefreshTokenEntity refreshToken)
void setAuthenticationHolder(AuthenticationHolderEntity authenticationHolder)
Definition: OAuth2AccessTokenEntity.java:168
OAuth2ClientRepository clientRepository
Definition: MITREidDataService_1_0.java:91
Map< Long, Long > getRefreshTokenToAuthHolderRefs()
Definition: MITREidDataServiceMaps.java:91
Map< Long, Set< Long > > getGrantToAccessTokensRefs()
Definition: MITREidDataServiceMaps.java:79
ApprovedSite getById(Long id)
AuthenticationHolderRepository authHolderRepository
Definition: MITREidDataService_1_0.java:99
AuthenticationHolderEntity getById(Long id)
Map< Long, Long > getAuthHolderOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:67
void setRefreshToken(OAuth2RefreshTokenEntity refreshToken)
Definition: OAuth2AccessTokenEntity.java:227
Map< Long, Long > getAccessTokenOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:43
void setAuthenticationHolder(AuthenticationHolderEntity authenticationHolder)
Definition: OAuth2RefreshTokenEntity.java:120
Map< Long, Long > getRefreshTokenOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:85
OAuth2RefreshTokenEntity getRefreshTokenById(Long Id)
void setClient(ClientDetailsEntity client)
Definition: OAuth2RefreshTokenEntity.java:169
◆ importData()
|
inline |
org.mitre.openid.connect.service.MITREidDataServiceを実装しています。
MITREidDataServiceMaps maps
Definition: MITREidDataService_1_0.java:107
static final String THIS_VERSION
Definition: MITREidDataService_1_0.java:109
void readAuthenticationHolders(JsonReader reader)
Definition: MITREidDataService_1_0.java:327
void readWhitelistedSites(JsonReader reader)
Definition: MITREidDataService_1_0.java:579
void readClients(JsonReader reader)
Definition: MITREidDataService_1_0.java:660
static final Logger logger
Definition: MITREidDataService_1_0.java:89
void readBlacklistedSites(JsonReader reader)
Definition: MITREidDataService_1_0.java:623
static final String AUTHENTICATIONHOLDERS
Definition: MITREidDataService.java:44
static final String GRANTS
Definition: MITREidDataService.java:45
static final String WHITELISTEDSITES
Definition: MITREidDataService.java:42
static final String SYSTEMSCOPES
Definition: MITREidDataService.java:47
void readAccessTokens(JsonReader reader)
Definition: MITREidDataService_1_0.java:258
void readGrants(JsonReader reader)
Definition: MITREidDataService_1_0.java:512
void readSystemScopes(JsonReader reader)
Definition: MITREidDataService_1_0.java:802
static final String CLIENTS
Definition: MITREidDataService.java:46
void readRefreshTokens(JsonReader reader)
Definition: MITREidDataService_1_0.java:197
static final String REFRESHTOKENS
Definition: MITREidDataService.java:40
static final String BLACKLISTEDSITES
Definition: MITREidDataService.java:43
void clearAll()
Definition: MITREidDataServiceMaps.java:107
List< MITREidDataServiceExtension > extensions
Definition: MITREidDataService_1_0.java:105
static final String ACCESSTOKENS
Definition: MITREidDataService.java:41
void fixObjectReferences()
Definition: MITREidDataService_1_0.java:844
◆ readAccessTokens()
|
inlineprivate |
- 引数
-
reader
- 例外
-
IOException
- 引数
-
reader
- 例外
-
IOException
MITREidDataServiceMaps maps
Definition: MITREidDataService_1_0.java:107
OAuth2AccessTokenEntity saveAccessToken(OAuth2AccessTokenEntity token)
Map< Long, Long > getAccessTokenToAuthHolderRefs()
Definition: MITREidDataServiceMaps.java:49
Map< Long, Long > getAccessTokenToRefreshTokenRefs()
Definition: MITREidDataServiceMaps.java:61
OAuth2TokenRepository tokenRepository
Definition: MITREidDataService_1_0.java:101
static final Logger logger
Definition: MITREidDataService_1_0.java:89
Map< Long, String > getAccessTokenToClientRefs()
Definition: MITREidDataServiceMaps.java:55
Date utcToDate(String value)
Definition: MITREidDataServiceSupport.java:39
Map< Long, Long > getAccessTokenOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:43
Long getId()
Definition: OAuth2AccessTokenEntity.java:134
◆ readAuthenticationHolders()
|
inlineprivate |
- 引数
-
reader
- 例外
-
IOException
MITREidDataServiceMaps maps
Definition: MITREidDataService_1_0.java:107
static final Logger logger
Definition: MITREidDataService_1_0.java:89
AuthenticationHolderEntity save(AuthenticationHolderEntity a)
AuthenticationHolderRepository authHolderRepository
Definition: MITREidDataService_1_0.java:99
Map< Long, Long > getAuthHolderOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:67
SavedUserAuthentication readSavedUserAuthentication(JsonReader reader)
Definition: MITREidDataService_1_0.java:466
OAuth2Request readAuthorizationRequest(JsonReader reader)
Definition: MITREidDataService_1_0.java:402
Long getId()
Definition: AuthenticationHolderEntity.java:95
◆ readAuthorizationRequest()
|
inlineprivate |
◆ readBlacklistedSites()
|
inlineprivate |
- 引数
-
reader
- 例外
-
IOException
static final Logger logger
Definition: MITREidDataService_1_0.java:89
BlacklistedSiteRepository blSiteRepository
Definition: MITREidDataService_1_0.java:97
BlacklistedSite save(BlacklistedSite blacklistedSite)
◆ readClients()
|
inlineprivate |
- 引数
-
reader
- 例外
-
IOException
ClientDetailsEntity saveClient(ClientDetailsEntity client)
static final Logger logger
Definition: MITREidDataService_1_0.java:89
OAuth2ClientRepository clientRepository
Definition: MITREidDataService_1_0.java:91
◆ readGrants()
|
inlineprivate |
- 引数
-
reader
- 例外
-
IOException
MITREidDataServiceMaps maps
Definition: MITREidDataService_1_0.java:107
Map< Long, Long > getGrantOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:73
ApprovedSite save(ApprovedSite approvedSite)
ApprovedSiteRepository approvedSiteRepository
Definition: MITREidDataService_1_0.java:93
static final Logger logger
Definition: MITREidDataService_1_0.java:89
Map< Long, Set< Long > > getGrantToAccessTokensRefs()
Definition: MITREidDataServiceMaps.java:79
Date utcToDate(String value)
Definition: MITREidDataServiceSupport.java:39
◆ readRefreshTokens()
|
inlineprivate |
- 引数
-
reader
- 例外
-
IOException
- 引数
-
reader
- 例外
-
IOException
MITREidDataServiceMaps maps
Definition: MITREidDataService_1_0.java:107
Long getId()
Definition: OAuth2RefreshTokenEntity.java:94
Map< Long, String > getRefreshTokenToClientRefs()
Definition: MITREidDataServiceMaps.java:97
OAuth2TokenRepository tokenRepository
Definition: MITREidDataService_1_0.java:101
static final Logger logger
Definition: MITREidDataService_1_0.java:89
OAuth2RefreshTokenEntity saveRefreshToken(OAuth2RefreshTokenEntity refreshToken)
Map< Long, Long > getRefreshTokenToAuthHolderRefs()
Definition: MITREidDataServiceMaps.java:91
Date utcToDate(String value)
Definition: MITREidDataServiceSupport.java:39
Map< Long, Long > getRefreshTokenOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:85
◆ readSavedUserAuthentication()
|
inlineprivate |
- 引数
-
reader
- 戻り値
- 例外
-
IOException
static final Logger logger
Definition: MITREidDataService_1_0.java:89
◆ readSystemScopes()
|
inlineprivate |
Read the list of system scopes from the reader and insert them into the scope repository.
- 引数
-
reader
- 例外
-
IOException
SystemScope save(SystemScope scope)
SystemScopeRepository sysScopeRepository
Definition: MITREidDataService_1_0.java:103
static final Logger logger
Definition: MITREidDataService_1_0.java:89
◆ readWhitelistedSites()
|
inlineprivate |
- 引数
-
reader
- 例外
-
IOException
WhitelistedSiteRepository wlSiteRepository
Definition: MITREidDataService_1_0.java:95
MITREidDataServiceMaps maps
Definition: MITREidDataService_1_0.java:107
Map< Long, Long > getWhitelistedSiteOldToNewIdMap()
Definition: MITREidDataServiceMaps.java:103
static final Logger logger
Definition: MITREidDataService_1_0.java:89
WhitelistedSite save(WhitelistedSite whiteListedSite)
◆ supportsVersion()
|
inline |
org.mitre.openid.connect.service.MITREidDataServiceを実装しています。
static final String THIS_VERSION
Definition: MITREidDataService_1_0.java:109
◆ toUTCString()
|
inlineprotectedinherited |
final DateFormatter dateFormatter
Definition: MITREidDataServiceSupport.java:28
◆ utcToDate()
|
inlineprotectedinherited |
static final Logger logger
Definition: MITREidDataServiceSupport.java:32
final DateFormatter dateFormatter
Definition: MITREidDataServiceSupport.java:28
メンバ詳解
◆ ACCESSTOKENS
|
staticinherited |
◆ approvedSiteRepository
|
private |
◆ AUTHENTICATIONHOLDERS
|
staticinherited |
◆ authHolderRepository
|
private |
◆ BLACKLISTEDSITES
|
staticinherited |
◆ blSiteRepository
|
private |
◆ clientRepository
|
private |
◆ CLIENTS
|
staticinherited |
◆ extensions
|
private |
◆ GRANTS
|
staticinherited |
◆ logger
|
staticprivate |
Logger for this class
◆ maps
|
private |
◆ MITREID_CONNECT_1_0
|
staticinherited |
Data member for 1.X configurations
◆ MITREID_CONNECT_1_1
|
staticinherited |
◆ MITREID_CONNECT_1_2
|
staticinherited |
◆ MITREID_CONNECT_1_3
|
staticinherited |
◆ REFRESHTOKENS
|
staticinherited |
◆ sysScopeRepository
|
private |
◆ SYSTEMSCOPES
|
staticinherited |
◆ THIS_VERSION
|
staticprivate |
◆ tokenRepository
|
private |
◆ WHITELISTEDSITES
|
staticinherited |
◆ wlSiteRepository
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/mitreid-connect/src/openid-connect-server/src/main/java/org/mitre/openid/connect/service/impl/MITREidDataService_1_0.java
 1.8.13
1.8.13