org.mitre.openid.connect.client.OIDCAuthenticationFilter の継承関係図
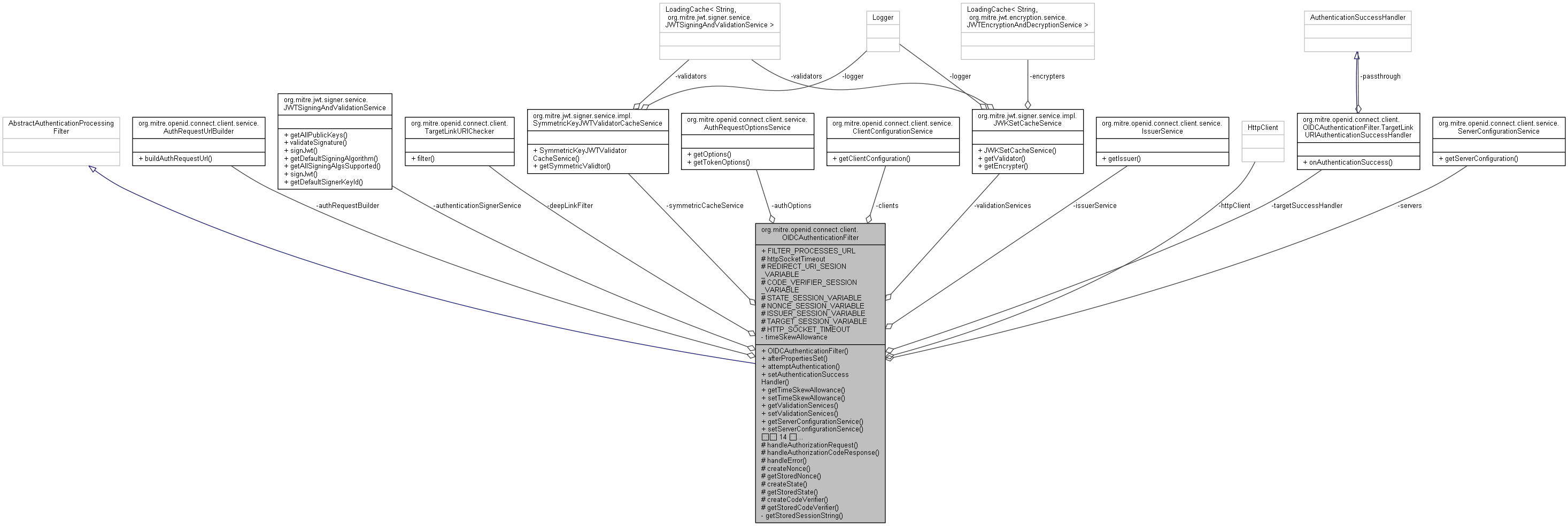
org.mitre.openid.connect.client.OIDCAuthenticationFilter 連携図
クラス | |
| class | TargetLinkURIAuthenticationSuccessHandler |
静的公開変数類 | |
| static final String | FILTER_PROCESSES_URL = "/openid_connect_login" |
限定公開メンバ関数 | |
| void | handleAuthorizationRequest (HttpServletRequest request, HttpServletResponse response) throws IOException |
| Authentication | handleAuthorizationCodeResponse (HttpServletRequest request, HttpServletResponse response) |
| void | handleError (HttpServletRequest request, HttpServletResponse response) throws IOException |
静的限定公開メンバ関数 | |
| static String | createNonce (HttpSession session) |
| static String | getStoredNonce (HttpSession session) |
| static String | createState (HttpSession session) |
| static String | getStoredState (HttpSession session) |
| static String | createCodeVerifier (HttpSession session) |
| static String | getStoredCodeVerifier (HttpSession session) |
限定公開変数類 | |
| int | httpSocketTimeout = HTTP_SOCKET_TIMEOUT |
静的限定公開変数類 | |
| static final String | REDIRECT_URI_SESION_VARIABLE = "redirect_uri" |
| static final String | CODE_VERIFIER_SESSION_VARIABLE = "code_verifier" |
| static final String | STATE_SESSION_VARIABLE = "state" |
| static final String | NONCE_SESSION_VARIABLE = "nonce" |
| static final String | ISSUER_SESSION_VARIABLE = "issuer" |
| static final String | TARGET_SESSION_VARIABLE = "target" |
| static final int | HTTP_SOCKET_TIMEOUT = 30000 |
静的非公開メンバ関数 | |
| static String | getStoredSessionString (HttpSession session, String key) |
詳解
OpenID Connect Authentication Filter class
構築子と解体子
◆ OIDCAuthenticationFilter()
|
inline |
OpenIdConnectAuthenticationFilter constructor
static final String FILTER_PROCESSES_URL
Definition: OIDCAuthenticationFilter.java:106
TargetLinkURIAuthenticationSuccessHandler targetSuccessHandler
Definition: OIDCAuthenticationFilter.java:141
AuthenticationSuccessHandler passthrough
Definition: OIDCAuthenticationFilter.java:750
関数詳解
◆ afterPropertiesSet()
|
inline |
JWKSetCacheService validationServices
Definition: OIDCAuthenticationFilter.java:113
SymmetricKeyJWTValidatorCacheService symmetricCacheService
Definition: OIDCAuthenticationFilter.java:117
◆ attemptAuthentication()
|
inline |
201 return null; // no auth, response redirected to the server's Auth Endpoint (or possibly to the account chooser)
void handleAuthorizationRequest(HttpServletRequest request, HttpServletResponse response)
Definition: OIDCAuthenticationFilter.java:216
void handleError(HttpServletRequest request, HttpServletResponse response)
Definition: OIDCAuthenticationFilter.java:647
Authentication handleAuthorizationCodeResponse(HttpServletRequest request, HttpServletResponse response)
Definition: OIDCAuthenticationFilter.java:310
◆ createCodeVerifier()
|
inlinestaticprotected |
Create a random code challenge and store it in the session
- 引数
-
session
- 戻り値
static final String CODE_VERIFIER_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:99
◆ createNonce()
|
inlinestaticprotected |
Create a cryptographically random nonce and store it in the session
- 引数
-
session
- 戻り値
static final String NONCE_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:101
◆ createState()
|
inlinestaticprotected |
Create a cryptographically random state and store it in the session
- 引数
-
session
- 戻り値
static final String STATE_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:100
◆ getAuthRequestOptionsService()
|
inline |
- 戻り値
- the authOptions
AuthRequestOptionsService authOptions
Definition: OIDCAuthenticationFilter.java:136
◆ getAuthRequestUrlBuilder()
|
inline |
- 戻り値
- the authRequestBuilder
AuthRequestUrlBuilder authRequestBuilder
Definition: OIDCAuthenticationFilter.java:138
◆ getClientConfigurationService()
|
inline |
- 戻り値
- the clients
ClientConfigurationService clients
Definition: OIDCAuthenticationFilter.java:134
◆ getIssuerService()
|
inline |
- 戻り値
- the issuerService
IssuerService issuerService
Definition: OIDCAuthenticationFilter.java:130
◆ getServerConfigurationService()
|
inline |
- 戻り値
- the servers
ServerConfigurationService servers
Definition: OIDCAuthenticationFilter.java:132
◆ getStoredCodeVerifier()
|
inlinestaticprotected |
Retrieve the stored challenge from our session
- 引数
-
session
- 戻り値
static final String CODE_VERIFIER_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:99
static String getStoredSessionString(HttpSession session, String key)
Definition: OIDCAuthenticationFilter.java:662
◆ getStoredNonce()
|
inlinestaticprotected |
Get the nonce we stored in the session
- 引数
-
session
- 戻り値
static final String NONCE_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:101
static String getStoredSessionString(HttpSession session, String key)
Definition: OIDCAuthenticationFilter.java:662
◆ getStoredSessionString()
|
inlinestaticprivate |
◆ getStoredState()
|
inlinestaticprotected |
Get the state we stored in the session
- 引数
-
session
- 戻り値
static final String STATE_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:100
static String getStoredSessionString(HttpSession session, String key)
Definition: OIDCAuthenticationFilter.java:662
◆ getSymmetricCacheService()
|
inline |
SymmetricKeyJWTValidatorCacheService symmetricCacheService
Definition: OIDCAuthenticationFilter.java:117
◆ getTargetLinkURIAuthenticationSuccessHandler()
|
inline |
TargetLinkURIAuthenticationSuccessHandler targetSuccessHandler
Definition: OIDCAuthenticationFilter.java:141
◆ getTimeSkewAllowance()
|
inline |
int timeSkewAllowance
Definition: OIDCAuthenticationFilter.java:109
◆ getValidationServices()
|
inline |
- 戻り値
- the validationServices
JWKSetCacheService validationServices
Definition: OIDCAuthenticationFilter.java:113
◆ handleAuthorizationCodeResponse()
|
inlineprotected |
- 引数
-
request The request from which to extract parameters and perform the authentication
- 戻り値
- The authenticated user token, or null if authentication is incomplete.
320 throw new AuthenticationServiceException("State parameter mismatch on return. Expected " + storedState + " got " + requestState);
356 HttpComponentsClientHttpRequestFactory factory = new HttpComponentsClientHttpRequestFactory(httpClient);
379 if (SECRET_JWT.equals(clientConfig.getTokenEndpointAuthMethod()) || PRIVATE_KEY.equals(clientConfig.getTokenEndpointAuthMethod())) {
405 throw new AuthenticationServiceException("Couldn't find required signer service for use with private key auth.");
446 jsonString = restTemplate.postForObject(serverConfig.getTokenEndpointUri(), form, String.class);
460 throw new AuthenticationServiceException("Token Endpoint did not return a JSON object: " + jsonRoot);
473 throw new AuthenticationServiceException("Unable to obtain Access Token. Token Endpoint returned: " + error);
488 throw new AuthenticationServiceException("Token Endpoint did not return an access_token: " + jsonString);
517 throw new AuthenticationServiceException("Token algorithm " + tokenAlg + " does not match expected algorithm " + clientAlg);
524 throw new AuthenticationServiceException("Unsigned ID tokens can only be used if explicitly configured in client.");
528 throw new AuthenticationServiceException("Unsigned token received, expected signature with " + tokenAlg);
551 throw new AuthenticationServiceException("Unable to find an appropriate signature validator for ID Token.");
559 throw new AuthenticationServiceException("Issuers do not match, expected " + serverConfig.getIssuer() + " got " + idClaims.getIssuer());
569 throw new AuthenticationServiceException("Id Token is expired: " + idClaims.getExpirationTime());
577 throw new AuthenticationServiceException("Id Token not valid untill: " + idClaims.getNotBeforeTime());
588 throw new AuthenticationServiceException("Id Token was issued in the future: " + idClaims.getIssueTime());
596 throw new AuthenticationServiceException("Audience does not match, expected " + clientConfig.getClientId() + " got " + idClaims.getAudience());
611 + "ID Token to the session " + NONCE_SESSION_VARIABLE + " failed. Expected " + storedNonce + " got " + nonce + ".");
615 + "ID Token to the session " + NONCE_SESSION_VARIABLE + " failed. Expected " + storedNonce + " got " + nonce + ".");
618 // construct an PendingOIDCAuthenticationToken and return a Authentication object w/the userId and the idToken
620 PendingOIDCAuthenticationToken token = new PendingOIDCAuthenticationToken(idClaims.getSubject(), idClaims.getIssuer(),
JWKSetCacheService validationServices
Definition: OIDCAuthenticationFilter.java:113
JWSAlgorithm getDefaultSigningAlgorithm()
Map< String, String > getTokenOptions(ServerConfiguration server, RegisteredClient client, HttpServletRequest request)
static String getStoredState(HttpSession session)
Definition: OIDCAuthenticationFilter.java:709
int timeSkewAllowance
Definition: OIDCAuthenticationFilter.java:109
JWTSigningAndValidationService authenticationSignerService
Definition: OIDCAuthenticationFilter.java:121
static final String REDIRECT_URI_SESION_VARIABLE
Definition: OIDCAuthenticationFilter.java:98
ClientConfigurationService clients
Definition: OIDCAuthenticationFilter.java:134
JWTSigningAndValidationService getSymmetricValidtor(ClientDetailsEntity client)
Definition: SymmetricKeyJWTValidatorCacheService.java:72
static final String ISSUER_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:102
ServerConfigurationService servers
Definition: OIDCAuthenticationFilter.java:132
HttpClient httpClient
Definition: OIDCAuthenticationFilter.java:124
RegisteredClient getClientConfiguration(ServerConfiguration issuer)
JWTSigningAndValidationService getValidator(String jwksUri)
Definition: JWKSetCacheService.java:85
static final String NONCE_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:101
static String getStoredSessionString(HttpSession session, String key)
Definition: OIDCAuthenticationFilter.java:662
static String getStoredCodeVerifier(HttpSession session)
Definition: OIDCAuthenticationFilter.java:729
static String getStoredNonce(HttpSession session)
Definition: OIDCAuthenticationFilter.java:688
SymmetricKeyJWTValidatorCacheService symmetricCacheService
Definition: OIDCAuthenticationFilter.java:117
ServerConfiguration getServerConfiguration(String issuer)
AuthRequestOptionsService authOptions
Definition: OIDCAuthenticationFilter.java:136
int httpSocketTimeout
Definition: OIDCAuthenticationFilter.java:144
◆ handleAuthorizationRequest()
|
inlineprotected |
Initiate an Authorization request
- 引数
-
request The request from which to extract parameters and perform the authentication response
- 例外
-
IOException If an input or output exception occurs
245 throw new AuthenticationServiceException("No server configuration found for issuer: " + issuer);
254 throw new AuthenticationServiceException("No client configuration found for issuer: " + issuer);
258 if (clientConfig.getRegisteredRedirectUri() != null && clientConfig.getRegisteredRedirectUri().size() == 1) {
284 String hash = Base64URL.encode(digest.digest(codeVerifier.getBytes(StandardCharsets.US_ASCII))).toString();
295 String authRequest = authRequestBuilder.buildAuthRequestUrl(serverConfig, clientConfig, redirectUri, nonce, state, options, issResp.getLoginHint());
AuthRequestUrlBuilder authRequestBuilder
Definition: OIDCAuthenticationFilter.java:138
IssuerService issuerService
Definition: OIDCAuthenticationFilter.java:130
static final String REDIRECT_URI_SESION_VARIABLE
Definition: OIDCAuthenticationFilter.java:98
ClientConfigurationService clients
Definition: OIDCAuthenticationFilter.java:134
static final String TARGET_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:103
String buildAuthRequestUrl(ServerConfiguration serverConfig, RegisteredClient clientConfig, String redirectUri, String nonce, String state, Map< String, String > options, String loginHint)
static final String ISSUER_SESSION_VARIABLE
Definition: OIDCAuthenticationFilter.java:102
Map< String, String > getOptions(ServerConfiguration server, RegisteredClient client, HttpServletRequest request)
ServerConfigurationService servers
Definition: OIDCAuthenticationFilter.java:132
static String createNonce(HttpSession session)
Definition: OIDCAuthenticationFilter.java:676
IssuerServiceResponse getIssuer(HttpServletRequest request)
RegisteredClient getClientConfiguration(ServerConfiguration issuer)
static String createState(HttpSession session)
Definition: OIDCAuthenticationFilter.java:697
static String createCodeVerifier(HttpSession session)
Definition: OIDCAuthenticationFilter.java:718
ServerConfiguration getServerConfiguration(String issuer)
AuthRequestOptionsService authOptions
Definition: OIDCAuthenticationFilter.java:136
◆ handleError()
|
inlineprotected |
Handle Authorization Endpoint error
- 引数
-
request The request from which to extract parameters and handle the error response The response, needed to do a redirect to display the error
- 例外
-
IOException If an input or output exception occurs
◆ setAuthenticationSuccessHandler()
|
inline |
TargetLinkURIAuthenticationSuccessHandler targetSuccessHandler
Definition: OIDCAuthenticationFilter.java:141
AuthenticationSuccessHandler passthrough
Definition: OIDCAuthenticationFilter.java:750
◆ setAuthRequestOptionsService()
|
inline |
- 引数
-
authOptions the authOptions to set
AuthRequestOptionsService authOptions
Definition: OIDCAuthenticationFilter.java:136
◆ setAuthRequestUrlBuilder()
|
inline |
- 引数
-
authRequestBuilder the authRequestBuilder to set
AuthRequestUrlBuilder authRequestBuilder
Definition: OIDCAuthenticationFilter.java:138
◆ setClientConfigurationService()
|
inline |
- 引数
-
clients the clients to set
ClientConfigurationService clients
Definition: OIDCAuthenticationFilter.java:134
◆ setIssuerService()
|
inline |
- 引数
-
issuerService the issuerService to set
IssuerService issuerService
Definition: OIDCAuthenticationFilter.java:130
◆ setServerConfigurationService()
|
inline |
- 引数
-
servers the servers to set
ServerConfigurationService servers
Definition: OIDCAuthenticationFilter.java:132
◆ setSymmetricCacheService()
|
inline |
SymmetricKeyJWTValidatorCacheService symmetricCacheService
Definition: OIDCAuthenticationFilter.java:117
◆ setTargetLinkURIAuthenticationSuccessHandler()
|
inline |
TargetLinkURIAuthenticationSuccessHandler targetSuccessHandler
Definition: OIDCAuthenticationFilter.java:141
◆ setTargetLinkURIChecker()
|
inline |
TargetLinkURIChecker deepLinkFilter
Definition: OIDCAuthenticationFilter.java:142
◆ setTimeSkewAllowance()
|
inline |
int timeSkewAllowance
Definition: OIDCAuthenticationFilter.java:109
◆ setValidationServices()
|
inline |
- 引数
-
validationServices the validationServices to set
JWKSetCacheService validationServices
Definition: OIDCAuthenticationFilter.java:113
◆ targetLinkURIChecker()
|
inline |
TargetLinkURIChecker deepLinkFilter
Definition: OIDCAuthenticationFilter.java:142
メンバ詳解
◆ authenticationSignerService
|
private |
◆ authOptions
|
private |
◆ authRequestBuilder
|
private |
◆ clients
|
private |
◆ CODE_VERIFIER_SESSION_VARIABLE
|
staticprotected |
◆ deepLinkFilter
|
private |
◆ FILTER_PROCESSES_URL
|
static |
◆ HTTP_SOCKET_TIMEOUT
|
staticprotected |
◆ httpClient
|
private |
◆ httpSocketTimeout
|
protected |
◆ ISSUER_SESSION_VARIABLE
|
staticprotected |
◆ issuerService
|
private |
◆ NONCE_SESSION_VARIABLE
|
staticprotected |
◆ REDIRECT_URI_SESION_VARIABLE
|
staticprotected |
◆ servers
|
private |
◆ STATE_SESSION_VARIABLE
|
staticprotected |
◆ symmetricCacheService
|
private |
◆ TARGET_SESSION_VARIABLE
|
staticprotected |
◆ targetSuccessHandler
|
private |
◆ timeSkewAllowance
|
private |
◆ validationServices
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/mitreid-connect/src/openid-connect-client/src/main/java/org/mitre/openid/connect/client/OIDCAuthenticationFilter.java
 1.8.13
1.8.13