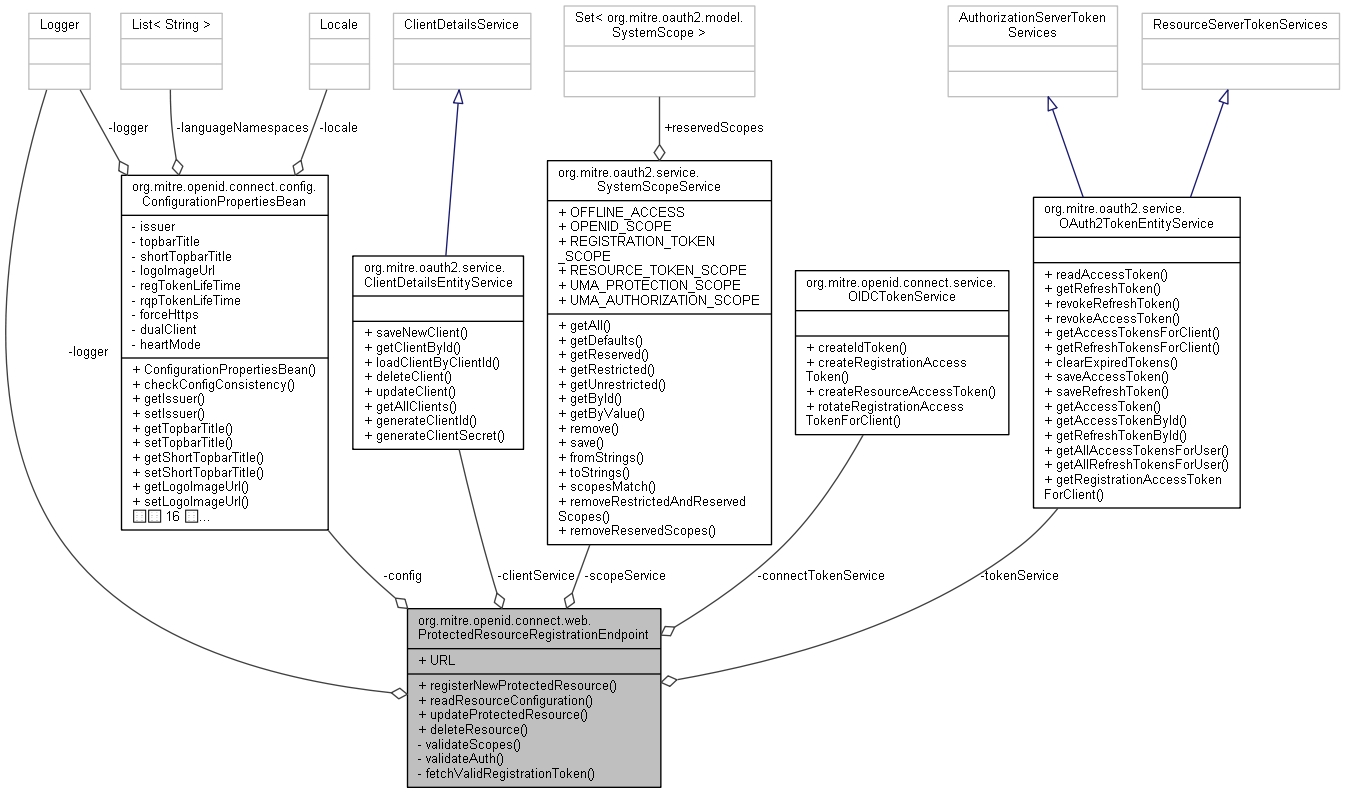
org.mitre.openid.connect.web.ProtectedResourceRegistrationEndpoint 連携図
公開メンバ関数 | |
| String | registerNewProtectedResource (@RequestBody String jsonString, Model m) |
| String | readResourceConfiguration (@PathVariable("id") String clientId, Model m, OAuth2Authentication auth) |
| String | updateProtectedResource (@PathVariable("id") String clientId, @RequestBody String jsonString, Model m, OAuth2Authentication auth) |
| String | deleteResource (@PathVariable("id") String clientId, Model m, OAuth2Authentication auth) |
静的公開変数類 | |
| static final String | URL = "resource" |
非公開メンバ関数 | |
| ClientDetailsEntity | validateScopes (ClientDetailsEntity newClient) throws ValidationException |
| ClientDetailsEntity | validateAuth (ClientDetailsEntity newClient) throws ValidationException |
| OAuth2AccessTokenEntity | fetchValidRegistrationToken (OAuth2Authentication auth, ClientDetailsEntity client) |
非公開変数類 | |
| ClientDetailsEntityService | clientService |
| OAuth2TokenEntityService | tokenService |
| SystemScopeService | scopeService |
| ConfigurationPropertiesBean | config |
| OIDCTokenService | connectTokenService |
静的非公開変数類 | |
| static final Logger | logger = LoggerFactory.getLogger(ProtectedResourceRegistrationEndpoint.class) |
詳解
関数詳解
◆ deleteResource()
|
inline |
Delete the indicated client from the system.
- 引数
-
clientId m auth
- 戻り値
ClientDetailsEntityService clientService
Definition: ProtectedResourceRegistrationEndpoint.java:68
static final Logger logger
Definition: ProtectedResourceRegistrationEndpoint.java:85
void deleteClient(ClientDetailsEntity client)
ClientDetailsEntity loadClientByClientId(String clientId)
◆ fetchValidRegistrationToken()
|
inlineprivate |
OAuth2TokenEntityService tokenService
Definition: ProtectedResourceRegistrationEndpoint.java:71
ConfigurationPropertiesBean config
Definition: ProtectedResourceRegistrationEndpoint.java:77
OAuth2AccessTokenEntity saveAccessToken(OAuth2AccessTokenEntity accessToken)
static final Logger logger
Definition: ProtectedResourceRegistrationEndpoint.java:85
Long getRegTokenLifeTime()
Definition: ConfigurationPropertiesBean.java:153
OAuth2AccessTokenEntity createResourceAccessToken(ClientDetailsEntity client)
OIDCTokenService connectTokenService
Definition: ProtectedResourceRegistrationEndpoint.java:80
OAuth2AccessTokenEntity readAccessToken(String accessTokenValue)
void revokeAccessToken(OAuth2AccessTokenEntity accessToken)
◆ readResourceConfiguration()
|
inline |
Get the meta information for a client.
- 引数
-
clientId m auth
- 戻り値
241 RegisteredClient registered = new RegisteredClient(client, token.getValue(), config.getIssuer() + "resource/" + UriUtils.encodePathSegment(client.getClientId(), "UTF-8"));
ConfigurationPropertiesBean config
Definition: ProtectedResourceRegistrationEndpoint.java:77
OAuth2AccessTokenEntity fetchValidRegistrationToken(OAuth2Authentication auth, ClientDetailsEntity client)
Definition: ProtectedResourceRegistrationEndpoint.java:440
ClientDetailsEntityService clientService
Definition: ProtectedResourceRegistrationEndpoint.java:68
static final Logger logger
Definition: ProtectedResourceRegistrationEndpoint.java:85
ClientDetailsEntity loadClientByClientId(String clientId)
String getIssuer()
Definition: ConfigurationPropertiesBean.java:100
◆ registerNewProtectedResource()
|
inline |
Create a new Client, issue a client ID, and create a registration access token.
- 引数
-
jsonString m p
- 戻り値
175 RegisteredClient registered = new RegisteredClient(savedClient, token.getValue(), config.getIssuer() + "resource/" + UriUtils.encodePathSegment(savedClient.getClientId(), "UTF-8"));
188 m.addAttribute(JsonErrorView.ERROR_MESSAGE, "Unable to save client due to invalid or inconsistent metadata.");
OAuth2TokenEntityService tokenService
Definition: ProtectedResourceRegistrationEndpoint.java:71
ConfigurationPropertiesBean config
Definition: ProtectedResourceRegistrationEndpoint.java:77
OAuth2AccessTokenEntity saveAccessToken(OAuth2AccessTokenEntity accessToken)
ClientDetailsEntity saveNewClient(ClientDetailsEntity client)
ClientDetailsEntity validateAuth(ClientDetailsEntity newClient)
Definition: ProtectedResourceRegistrationEndpoint.java:413
ClientDetailsEntityService clientService
Definition: ProtectedResourceRegistrationEndpoint.java:68
static final Logger logger
Definition: ProtectedResourceRegistrationEndpoint.java:85
OAuth2AccessTokenEntity createResourceAccessToken(ClientDetailsEntity client)
OIDCTokenService connectTokenService
Definition: ProtectedResourceRegistrationEndpoint.java:80
ClientDetailsEntity validateScopes(ClientDetailsEntity newClient)
Definition: ProtectedResourceRegistrationEndpoint.java:203
String getIssuer()
Definition: ConfigurationPropertiesBean.java:100
◆ updateProtectedResource()
|
inline |
Update the metainformation for a given client.
- 引数
-
clientId jsonString m auth
- 戻り値
290 && oldClient.getClientId().equals(auth.getOAuth2Request().getClientId()) // the client passed in the URI matches the one in the auth
291 && oldClient.getClientId().equals(newClient.getClientId()) // the client passed in the body matches the one in the URI
352 RegisteredClient registered = new RegisteredClient(savedClient, token.getValue(), config.getIssuer() + "resource/" + UriUtils.encodePathSegment(savedClient.getClientId(), "UTF-8"));
367 m.addAttribute(JsonErrorView.ERROR_MESSAGE, "Unable to save client due to invalid or inconsistent metadata.");
ConfigurationPropertiesBean config
Definition: ProtectedResourceRegistrationEndpoint.java:77
OAuth2AccessTokenEntity fetchValidRegistrationToken(OAuth2Authentication auth, ClientDetailsEntity client)
Definition: ProtectedResourceRegistrationEndpoint.java:440
void setClientSecret(String clientSecret)
Definition: ClientDetailsEntity.java:425
ClientDetailsEntity validateAuth(ClientDetailsEntity newClient)
Definition: ProtectedResourceRegistrationEndpoint.java:413
ClientDetailsEntityService clientService
Definition: ProtectedResourceRegistrationEndpoint.java:68
static final Logger logger
Definition: ProtectedResourceRegistrationEndpoint.java:85
ClientDetailsEntity updateClient(ClientDetailsEntity oldClient, ClientDetailsEntity newClient)
ClientDetailsEntity loadClientByClientId(String clientId)
ClientDetailsEntity validateScopes(ClientDetailsEntity newClient)
Definition: ProtectedResourceRegistrationEndpoint.java:203
String getIssuer()
Definition: ConfigurationPropertiesBean.java:100
◆ validateAuth()
|
inlineprivate |
428 throw new ValidationException("invalid_client_metadata", "JWK Set URI required when using private key authentication", HttpStatus.BAD_REQUEST);
435 throw new ValidationException("invalid_client_metadata", "Unknown authentication method", HttpStatus.BAD_REQUEST);
ClientDetailsEntityService clientService
Definition: ProtectedResourceRegistrationEndpoint.java:68
ClientDetailsEntity generateClientSecret(ClientDetailsEntity client)
◆ validateScopes()
|
inlineprivate |
208 Set<SystemScope> allowedScopes = scopeService.removeRestrictedAndReservedScopes(requestedScopes);
Set< SystemScope > removeRestrictedAndReservedScopes(Set< SystemScope > scopes)
SystemScopeService scopeService
Definition: ProtectedResourceRegistrationEndpoint.java:74
Set< SystemScope > fromStrings(Set< String > scope)
Set< SystemScope > getDefaults()
Set< String > toStrings(Set< SystemScope > scope)
メンバ詳解
◆ clientService
|
private |
◆ config
|
private |
◆ connectTokenService
|
private |
◆ logger
|
staticprivate |
Logger for this class
◆ scopeService
|
private |
◆ tokenService
|
private |
◆ URL
|
static |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/mitreid-connect/src/openid-connect-server/src/main/java/org/mitre/openid/connect/web/ProtectedResourceRegistrationEndpoint.java
 1.8.13
1.8.13