org.mitre.openid.connect.assertion.JWTBearerAuthenticationProvider の継承関係図
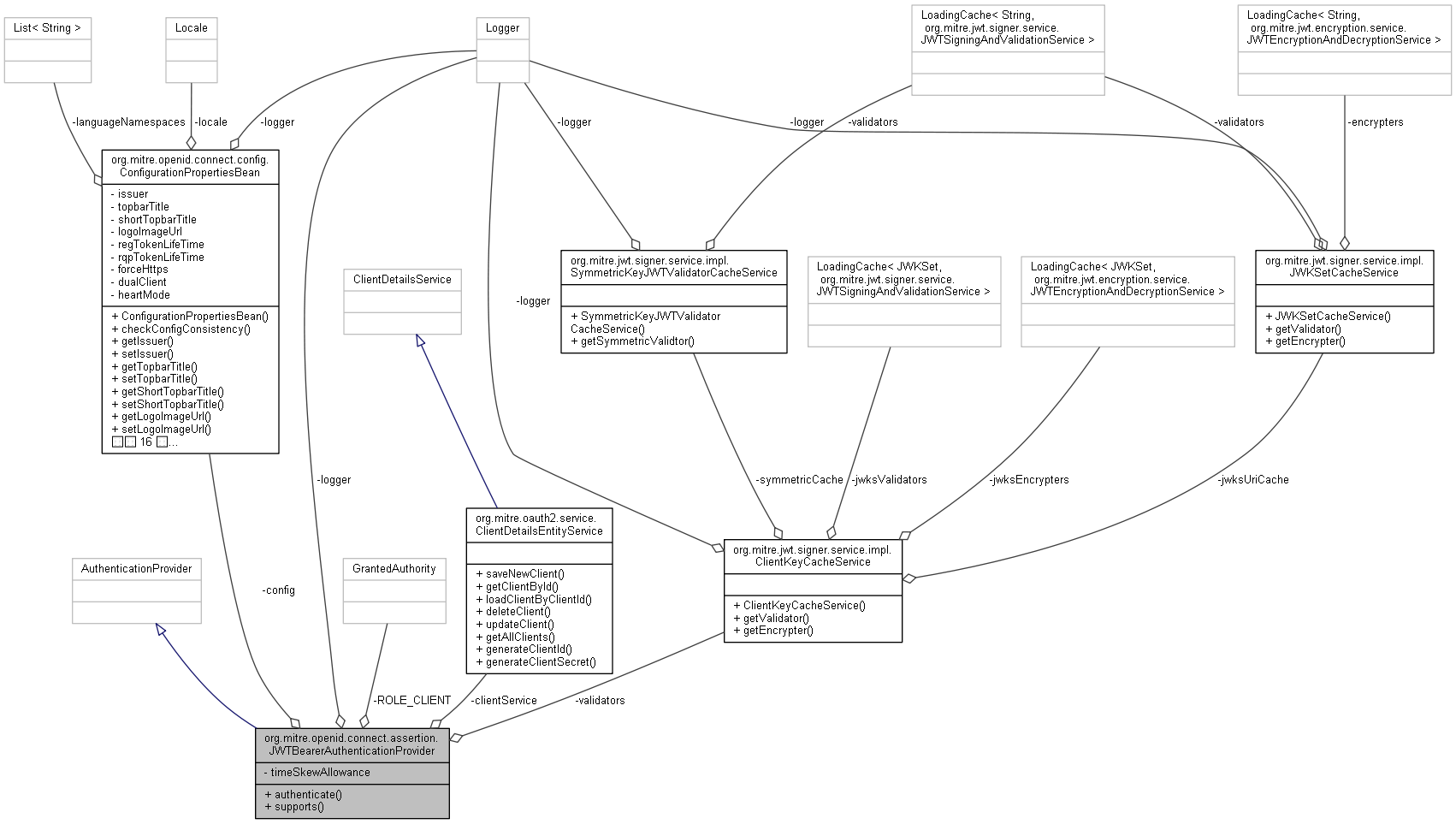
org.mitre.openid.connect.assertion.JWTBearerAuthenticationProvider 連携図
公開メンバ関数 | |
| Authentication | authenticate (Authentication authentication) throws AuthenticationException |
| boolean | supports (Class<?> authentication) |
非公開変数類 | |
| ClientKeyCacheService | validators |
| int | timeSkewAllowance = 300 |
| ClientDetailsEntityService | clientService |
| ConfigurationPropertiesBean | config |
静的非公開変数類 | |
| static final Logger | logger = LoggerFactory.getLogger(JWTBearerAuthenticationProvider.class) |
| static final GrantedAuthority | ROLE_CLIENT = new SimpleGrantedAuthority("ROLE_CLIENT") |
詳解
関数詳解
◆ authenticate()
|
inline |
Try to validate the client credentials by parsing and validating the JWT.
85 JWTBearerAssertionAuthenticationToken jwtAuth = (JWTBearerAssertionAuthenticationToken)authentication;
102 throw new InvalidClientException("Client's registered request object signing algorithm (" + client.getRequestObjectSigningAlg() + ") does not match request object's actual algorithm (" + alg.getName() + ")");
111 throw new AuthenticationServiceException("Client does not support this authentication method.");
129 if (config.isHeartMode() && !client.getTokenEndpointAuthMethod().equals(AuthMethod.PRIVATE_KEY)) {
136 throw new AuthenticationServiceException("Unable to create signature validator for client " + client + " and algorithm " + alg);
140 throw new AuthenticationServiceException("Signature did not validate for presented JWT authentication.");
143 throw new AuthenticationServiceException("Unable to create signature validator for method " + client.getTokenEndpointAuthMethod() + " and algorithm " + alg);
151 throw new AuthenticationServiceException("Issuers do not match, expected " + client.getClientId() + " got " + jwtClaims.getIssuer());
156 throw new AuthenticationServiceException("Assertion Token does not have required expiration claim");
161 throw new AuthenticationServiceException("Assertion Token is expired: " + jwtClaims.getExpirationTime());
169 throw new AuthenticationServiceException("Assertion Token not valid untill: " + jwtClaims.getNotBeforeTime());
178 throw new AuthenticationServiceException("Assertion Token was issued in the future: " + jwtClaims.getIssueTime());
185 } else if (!(jwtClaims.getAudience().contains(config.getIssuer()) || jwtClaims.getAudience().contains(config.getIssuer() + "token"))) {
186 throw new AuthenticationServiceException("Audience does not match, expected " + config.getIssuer() + " or " + (config.getIssuer() + "token") + " got " + jwtClaims.getAudience());
ConfigurationPropertiesBean config
Definition: JWTBearerAuthenticationProvider.java:77
static final Logger logger
Definition: JWTBearerAuthenticationProvider.java:60
JWTSigningAndValidationService getValidator(ClientDetailsEntity client, JWSAlgorithm alg)
Definition: ClientKeyCacheService.java:77
ClientKeyCacheService validators
Definition: JWTBearerAuthenticationProvider.java:66
static final GrantedAuthority ROLE_CLIENT
Definition: JWTBearerAuthenticationProvider.java:62
ClientDetailsEntityService clientService
Definition: JWTBearerAuthenticationProvider.java:73
ClientDetailsEntity loadClientByClientId(String clientId)
String getIssuer()
Definition: ConfigurationPropertiesBean.java:100
boolean isHeartMode()
Definition: ConfigurationPropertiesBean.java:250
int timeSkewAllowance
Definition: JWTBearerAuthenticationProvider.java:69
◆ supports()
|
inline |
We support JWTBearerAssertionAuthenticationTokens only.
メンバ詳解
◆ clientService
|
private |
◆ config
|
private |
◆ logger
|
staticprivate |
Logger for this class
◆ ROLE_CLIENT
|
staticprivate |
◆ timeSkewAllowance
|
private |
◆ validators
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/mitreid-connect/src/openid-connect-server/src/main/java/org/mitre/openid/connect/assertion/JWTBearerAuthenticationProvider.java
 1.8.13
1.8.13