org.keycloak.authorization.admin.PolicyService の継承関係図

org.keycloak.authorization.admin.PolicyService 連携図
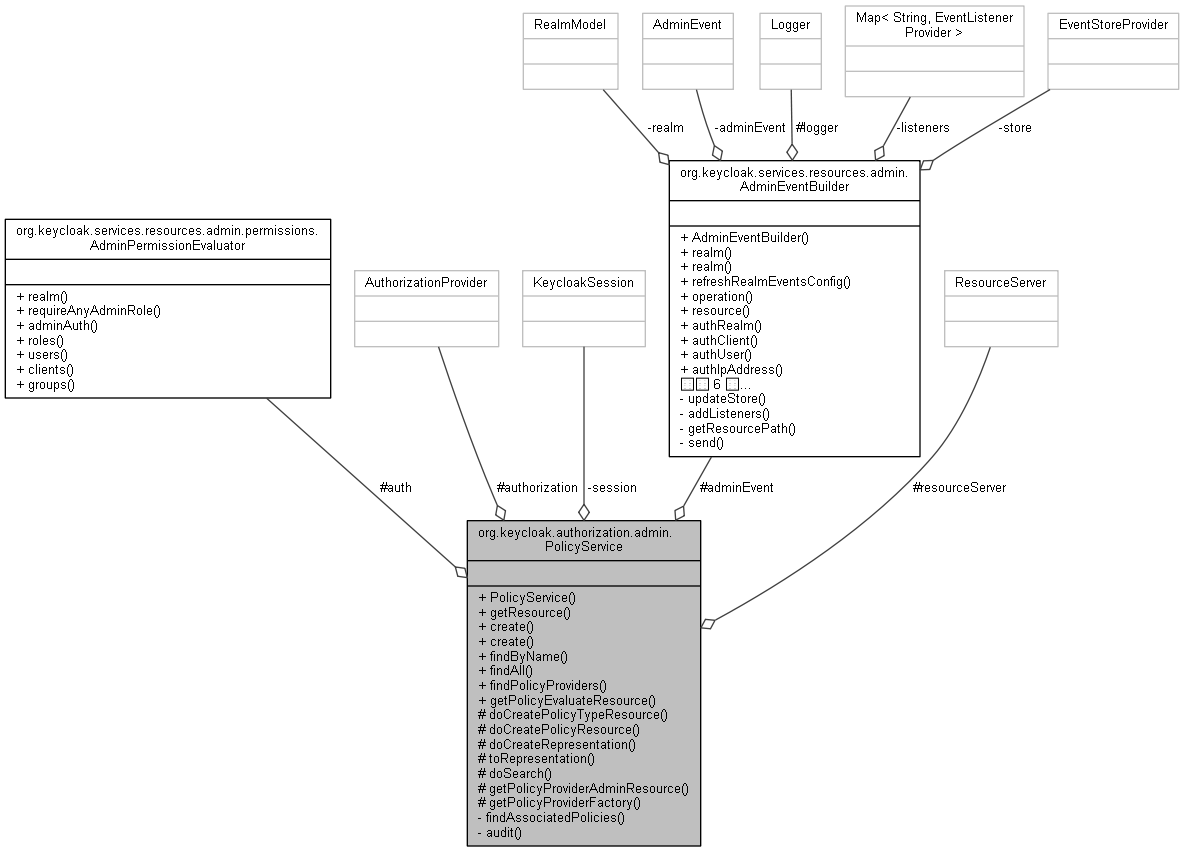
公開メンバ関数 | |
| PolicyService (ResourceServer resourceServer, AuthorizationProvider authorization, AdminPermissionEvaluator auth, AdminEventBuilder adminEvent) | |
| Object | getResource (@PathParam("type") String type) |
| Response | create (String payload) |
| Policy | create (AbstractPolicyRepresentation representation) |
| Response | findByName (@QueryParam("name") String name) |
| Response | findAll (@QueryParam("policyId") String id, @QueryParam("name") String name, @QueryParam("type") String type, @QueryParam("resource") String resource, @QueryParam("scope") String scope, @QueryParam("permission") Boolean permission, @QueryParam("owner") String owner, @QueryParam("first") Integer firstResult, @QueryParam("max") Integer maxResult) |
| Response | findPolicyProviders () |
| PolicyEvaluationService | getPolicyEvaluateResource () |
限定公開メンバ関数 | |
| PolicyTypeService | doCreatePolicyTypeResource (String type) |
| Object | doCreatePolicyResource (Policy policy) |
| AbstractPolicyRepresentation | doCreateRepresentation (String payload) |
| AbstractPolicyRepresentation | toRepresentation (Policy model, AuthorizationProvider authorization) |
| List< Object > | doSearch (Integer firstResult, Integer maxResult, Map< String, String[]> filters) |
| PolicyProviderAdminService | getPolicyProviderAdminResource (String policyType) |
| PolicyProviderFactory | getPolicyProviderFactory (String policyType) |
限定公開変数類 | |
| final ResourceServer | resourceServer |
| final AuthorizationProvider | authorization |
| final AdminPermissionEvaluator | auth |
| final AdminEventBuilder | adminEvent |
非公開メンバ関数 | |
| void | findAssociatedPolicies (Policy policy, List< Policy > policies) |
| void | audit (AbstractPolicyRepresentation resource, String id, OperationType operation) |
非公開変数類 | |
| KeycloakSession | session |
詳解
構築子と解体子
◆ PolicyService()
|
inline |
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final AdminPermissionEvaluator auth
Definition: PolicyService.java:79
final ResourceServer resourceServer
Definition: PolicyService.java:77
AdminEventBuilder resource(ResourceType resourceType)
Definition: AdminEventBuilder.java:118
final AdminEventBuilder adminEvent
Definition: PolicyService.java:80
関数詳解
◆ audit()
|
inlineprivate |
334 adminEvent.operation(operation).resourcePath(session.getContext().getUri(), id).representation(resource).success();
336 adminEvent.operation(operation).resourcePath(session.getContext().getUri()).representation(resource).success();
final AuthorizationProvider authorization
Definition: PolicyService.java:78
AdminEventBuilder operation(OperationType operationType)
Definition: AdminEventBuilder.java:113
void success()
Definition: AdminEventBuilder.java:226
KeycloakSession session
Definition: PolicyService.java:76
AdminEventBuilder resourcePath(String... pathElements)
Definition: AdminEventBuilder.java:171
final AdminEventBuilder adminEvent
Definition: PolicyService.java:80
◆ create() [1/2]
|
inline |
final AdminPermissionEvaluator auth
Definition: PolicyService.java:79
Response create(String payload)
Definition: PolicyService.java:114
void requireManageAuthorization()
void audit(AbstractPolicyRepresentation resource, String id, OperationType operation)
Definition: PolicyService.java:331
AbstractPolicyRepresentation doCreateRepresentation(String payload)
Definition: PolicyService.java:129
RealmPermissionEvaluator realm()
◆ create() [2/2]
|
inline |
◆ doCreatePolicyResource()
|
inlineprotected |
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final AdminPermissionEvaluator auth
Definition: PolicyService.java:79
final ResourceServer resourceServer
Definition: PolicyService.java:77
final AdminEventBuilder adminEvent
Definition: PolicyService.java:80
◆ doCreatePolicyTypeResource()
|
inlineprotected |
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final AdminPermissionEvaluator auth
Definition: PolicyService.java:79
final ResourceServer resourceServer
Definition: PolicyService.java:77
final AdminEventBuilder adminEvent
Definition: PolicyService.java:80
◆ doCreateRepresentation()
|
inlineprotected |
◆ doSearch()
|
inlineprotected |
273 return policyStore.findByResourceServer(filters, resourceServer.getId(), firstResult != null ? firstResult : -1, maxResult != null ? maxResult : Constants.DEFAULT_MAX_RESULTS).stream()
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final ResourceServer resourceServer
Definition: PolicyService.java:77
AbstractPolicyRepresentation toRepresentation(Policy model, AuthorizationProvider authorization)
Definition: PolicyService.java:267
◆ findAll()
|
inline |
225 Set<String> resources = resourceStore.findByResourceServer(resourceFilters, resourceServer.getId(), -1, 1).stream().map(Resource::getId).collect(Collectors.toSet());
246 Set<String> scopes = scopeStore.findByResourceServer(scopeFilters, resourceServer.getId(), -1, 1).stream().map(Scope::getId).collect(Collectors.toSet());
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final AdminPermissionEvaluator auth
Definition: PolicyService.java:79
final ResourceServer resourceServer
Definition: PolicyService.java:77
void requireViewAuthorization()
RealmPermissionEvaluator realm()
List< Object > doSearch(Integer firstResult, Integer maxResult, Map< String, String[]> filters)
Definition: PolicyService.java:271
◆ findAssociatedPolicies()
|
inlineprivate |
void findAssociatedPolicies(Policy policy, List< Policy > policies)
Definition: PolicyService.java:324
◆ findByName()
|
inline |
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final AdminPermissionEvaluator auth
Definition: PolicyService.java:79
final ResourceServer resourceServer
Definition: PolicyService.java:77
void requireViewAuthorization()
RealmPermissionEvaluator realm()
AbstractPolicyRepresentation toRepresentation(Policy model, AuthorizationProvider authorization)
Definition: PolicyService.java:267
◆ findPolicyProviders()
|
inline |
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final AdminPermissionEvaluator auth
Definition: PolicyService.java:79
void requireViewAuthorization()
RealmPermissionEvaluator realm()
◆ getPolicyEvaluateResource()
|
inline |
309 PolicyEvaluationService resource = new PolicyEvaluationService(this.resourceServer, this.authorization, this.auth);
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final AdminPermissionEvaluator auth
Definition: PolicyService.java:79
final ResourceServer resourceServer
Definition: PolicyService.java:77
void requireViewAuthorization()
RealmPermissionEvaluator realm()
◆ getPolicyProviderAdminResource()
|
inlineprotected |
PolicyProviderFactory getPolicyProviderFactory(String policyType)
Definition: PolicyService.java:320
final AuthorizationProvider authorization
Definition: PolicyService.java:78
final ResourceServer resourceServer
Definition: PolicyService.java:77
◆ getPolicyProviderFactory()
|
inlineprotected |
final AuthorizationProvider authorization
Definition: PolicyService.java:78
◆ getResource()
|
inline |
97 Policy policy = authorization.getStoreFactory().getPolicyStore().findById(type, resourceServer.getId());
PolicyProviderFactory getPolicyProviderFactory(String policyType)
Definition: PolicyService.java:320
final AuthorizationProvider authorization
Definition: PolicyService.java:78
Object doCreatePolicyResource(Policy policy)
Definition: PolicyService.java:106
final ResourceServer resourceServer
Definition: PolicyService.java:77
PolicyTypeService doCreatePolicyTypeResource(String type)
Definition: PolicyService.java:102
◆ toRepresentation()
|
inlineprotected |
final AuthorizationProvider authorization
Definition: PolicyService.java:78
メンバ詳解
◆ adminEvent
|
protected |
◆ auth
|
protected |
◆ authorization
|
protected |
◆ resourceServer
|
protected |
◆ session
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/rest-service/src/services/src/main/java/org/keycloak/authorization/admin/PolicyService.java
 1.8.13
1.8.13