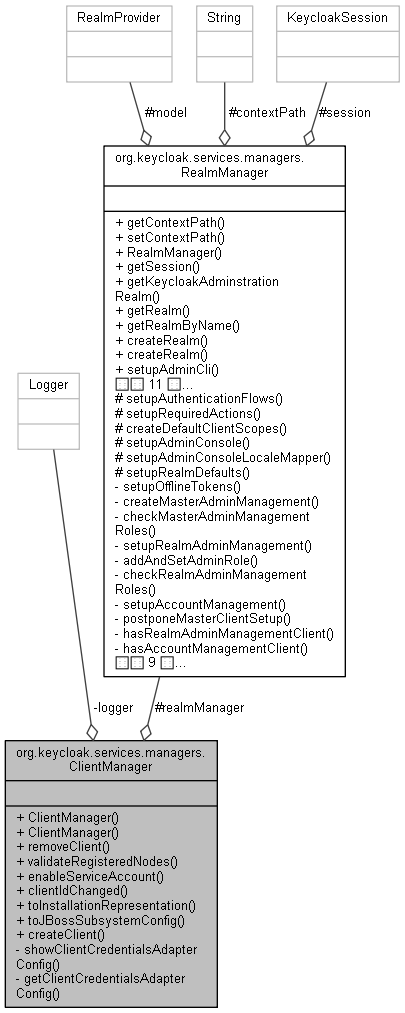
org.keycloak.services.managers.ClientManager 連携図
クラス | |
| class | InstallationAdapterConfig |
公開メンバ関数 | |
| ClientManager (RealmManager realmManager) | |
| ClientManager () | |
| boolean | removeClient (RealmModel realm, ClientModel client) |
| Set< String > | validateRegisteredNodes (ClientModel client) |
| void | enableServiceAccount (ClientModel client) |
| void | clientIdChanged (ClientModel client, String newClientId) |
| InstallationAdapterConfig | toInstallationRepresentation (RealmModel realmModel, ClientModel clientModel, URI baseUri) |
| String | toJBossSubsystemConfig (RealmModel realmModel, ClientModel clientModel, URI baseUri) |
静的公開メンバ関数 | |
| static ClientModel | createClient (KeycloakSession session, RealmModel realm, ClientRepresentation rep, boolean addDefaultRoles) |
限定公開変数類 | |
| RealmManager | realmManager |
非公開メンバ関数 | |
| boolean | showClientCredentialsAdapterConfig (ClientModel client) |
| Map< String, Object > | getClientCredentialsAdapterConfig (ClientModel client) |
静的非公開変数類 | |
| static final Logger | logger = Logger.getLogger(ClientManager.class) |
詳解
- バージョン
- Revision
- 1
構築子と解体子
◆ ClientManager() [1/2]
|
inline |
RealmManager realmManager
Definition: ClientManager.java:59
◆ ClientManager() [2/2]
関数詳解
◆ clientIdChanged()
|
inline |
static final Logger logger
Definition: ClientManager.java:57
RealmManager realmManager
Definition: ClientManager.java:59
KeycloakSession getSession()
Definition: RealmManager.java:85
◆ createClient()
|
inlinestatic |
Should not be called from an import. This really expects that the client is created from the admin console.
- 引数
-
session realm rep addDefaultRoles
- 戻り値
◆ enableServiceAccount()
|
inline |
165 UserModel user = realmManager.getSession().userLocalStorage().addUser(client.getRealm(), username);
172 if (client.getProtocolMapperByName(OIDCLoginProtocol.LOGIN_PROTOCOL, ServiceAccountConstants.CLIENT_ID_PROTOCOL_MAPPER) == null) {
173 logger.debugf("Creating service account protocol mapper '%s' for client '%s'", ServiceAccountConstants.CLIENT_ID_PROTOCOL_MAPPER, client.getClientId());
174 ProtocolMapperModel protocolMapper = UserSessionNoteMapper.createClaimMapper(ServiceAccountConstants.CLIENT_ID_PROTOCOL_MAPPER,
182 if (client.getProtocolMapperByName(OIDCLoginProtocol.LOGIN_PROTOCOL, ServiceAccountConstants.CLIENT_HOST_PROTOCOL_MAPPER) == null) {
183 logger.debugf("Creating service account protocol mapper '%s' for client '%s'", ServiceAccountConstants.CLIENT_HOST_PROTOCOL_MAPPER, client.getClientId());
184 ProtocolMapperModel protocolMapper = UserSessionNoteMapper.createClaimMapper(ServiceAccountConstants.CLIENT_HOST_PROTOCOL_MAPPER,
191 if (client.getProtocolMapperByName(OIDCLoginProtocol.LOGIN_PROTOCOL, ServiceAccountConstants.CLIENT_ADDRESS_PROTOCOL_MAPPER) == null) {
192 logger.debugf("Creating service account protocol mapper '%s' for client '%s'", ServiceAccountConstants.CLIENT_ADDRESS_PROTOCOL_MAPPER, client.getClientId());
193 ProtocolMapperModel protocolMapper = UserSessionNoteMapper.createClaimMapper(ServiceAccountConstants.CLIENT_ADDRESS_PROTOCOL_MAPPER,
static final Logger logger
Definition: ClientManager.java:57
RealmManager realmManager
Definition: ClientManager.java:59
KeycloakSession getSession()
Definition: RealmManager.java:85
◆ getClientCredentialsAdapterConfig()
|
inlineprivate |
362 ClientAuthenticatorFactory authenticator = (ClientAuthenticatorFactory) realmManager.getSession().getKeycloakSessionFactory().getProviderFactory(ClientAuthenticator.class, clientAuthenticator);
RealmManager realmManager
Definition: ClientManager.java:59
KeycloakSession getSession()
Definition: RealmManager.java:85
◆ removeClient()
|
inline |
103 UserSessionPersisterProvider sessionsPersister = realmManager.getSession().getProvider(UserSessionPersisterProvider.class);
108 AuthenticationSessionProvider authSessions = realmManager.getSession().authenticationSessions();
RealmManager realmManager
Definition: ClientManager.java:59
KeycloakSession getSession()
Definition: RealmManager.java:85
◆ showClientCredentialsAdapterConfig()
|
inlineprivate |
◆ toInstallationRepresentation()
|
inline |
boolean showClientCredentialsAdapterConfig(ClientModel client)
Definition: ClientManager.java:348
Map< String, Object > getClientCredentialsAdapterConfig(ClientModel client)
Definition: ClientManager.java:360
◆ toJBossSubsystemConfig()
|
inline |
320 buffer.append(" <ssl-required>").append(realmModel.getSslRequired().name()).append("</ssl-required>\n");
333 buffer.append(" <" + credEntry.getKey() + ">" + credEntry.getValue().toString() + "</" + credEntry.getKey() + ">\n");
boolean showClientCredentialsAdapterConfig(ClientModel client)
Definition: ClientManager.java:348
Map< String, Object > getClientCredentialsAdapterConfig(ClientModel client)
Definition: ClientManager.java:360
◆ validateRegisteredNodes()
|
inline |
メンバ詳解
◆ logger
|
staticprivate |
◆ realmManager
|
protected |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/rest-service/src/services/src/main/java/org/keycloak/services/managers/ClientManager.java
 1.8.13
1.8.13