97 if (manageScope == null) {
98 manageScope =
authz.getStoreFactory().getScopeStore().create(AdminPermissionManagement.MANAGE_SCOPE, server);
101 if (viewScope == null) {
102 viewScope =
authz.getStoreFactory().getScopeStore().create(AdminPermissionManagement.VIEW_SCOPE, server);
105 if (mapRoleScope == null) {
114 Resource
resource =
authz.getStoreFactory().getResourceStore().findByName(resourceName, server.getId());
115 if (resource == null) {
116 resource =
authz.getStoreFactory().getResourceStore().create(resourceName, server, server.getId());
117 resource.setType(
"Client");
118 Set<Scope> scopeset =
new HashSet<>();
119 scopeset.add(configureScope);
120 scopeset.add(manageScope);
121 scopeset.add(viewScope);
122 scopeset.add(mapRoleScope);
123 scopeset.add(mapRoleClientScope);
124 scopeset.add(mapRoleCompositeScope);
125 scopeset.add(exchangeToScope);
126 resource.updateScopes(scopeset);
129 Policy
managePermission =
authz.getStoreFactory().getPolicyStore().findByName(managePermissionName, server.getId());
130 if (managePermission == null) {
131 Helper.addEmptyScopePermission(
authz, server, managePermissionName, resource, manageScope);
134 Policy
configurePermission =
authz.getStoreFactory().getPolicyStore().findByName(configurePermissionName, server.getId());
135 if (configurePermission == null) {
136 Helper.addEmptyScopePermission(
authz, server, configurePermissionName, resource, configureScope);
139 Policy
viewPermission =
authz.getStoreFactory().getPolicyStore().findByName(viewPermissionName, server.getId());
140 if (viewPermission == null) {
141 Helper.addEmptyScopePermission(
authz, server, viewPermissionName, resource, viewScope);
144 Policy mapRolePermission =
authz.getStoreFactory().getPolicyStore().findByName(mapRolePermissionName, server.getId());
145 if (mapRolePermission == null) {
146 Helper.addEmptyScopePermission(
authz, server, mapRolePermissionName, resource, mapRoleScope);
149 Policy mapRoleClientScopePermission =
authz.getStoreFactory().getPolicyStore().findByName(mapRoleClientScopePermissionName, server.getId());
150 if (mapRoleClientScopePermission == null) {
151 Helper.addEmptyScopePermission(
authz, server, mapRoleClientScopePermissionName, resource, mapRoleClientScope);
154 Policy mapRoleCompositePermission =
authz.getStoreFactory().getPolicyStore().findByName(mapRoleCompositePermissionName, server.getId());
155 if (mapRoleCompositePermission == null) {
156 Helper.addEmptyScopePermission(
authz, server, mapRoleCompositePermissionName, resource, mapRoleCompositeScope);
159 Policy
exchangeToPermission =
authz.getStoreFactory().getPolicyStore().findByName(exchangeToPermissionName, server.getId());
160 if (exchangeToPermission == null) {
161 Helper.addEmptyScopePermission(
authz, server, exchangeToPermissionName, resource, exchangeToScope);
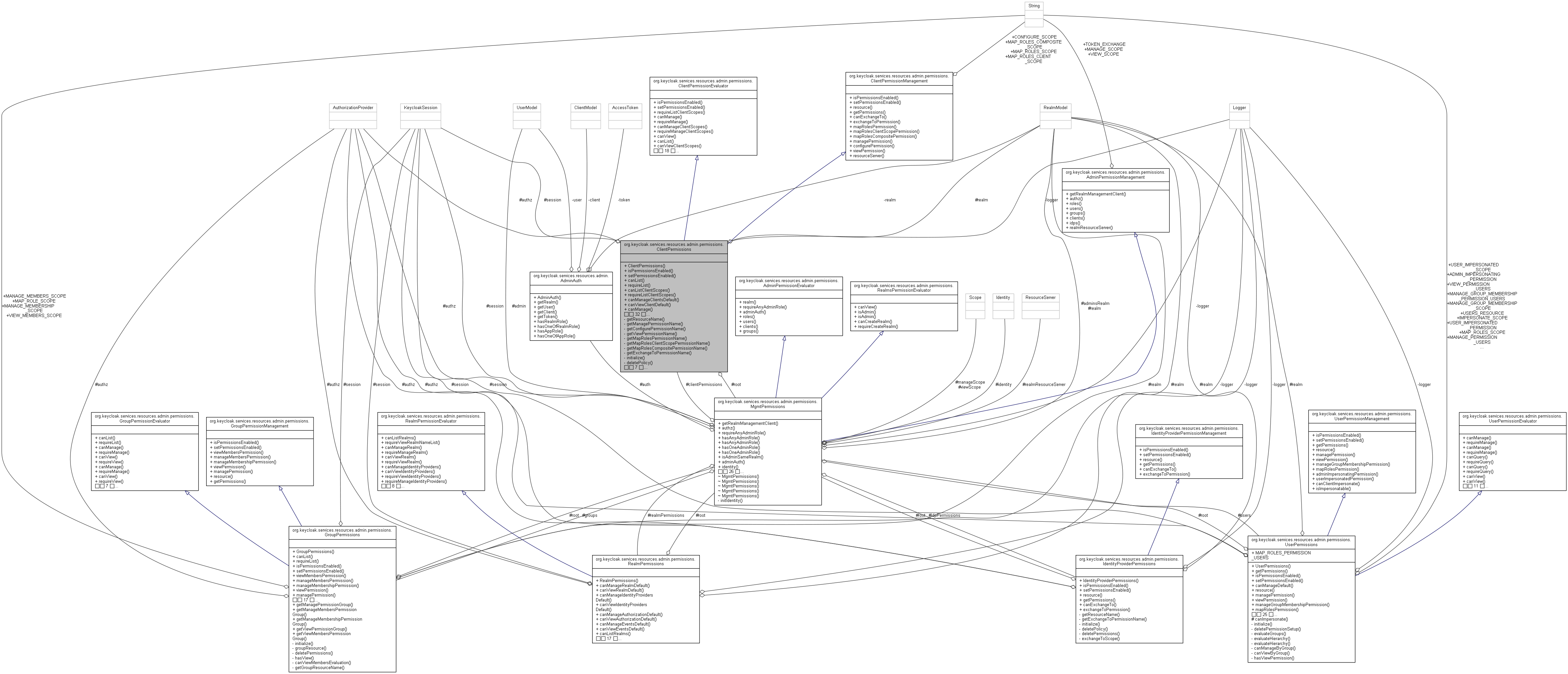
Policy managePermission(ClientModel client)
Definition: ClientPermissions.java:564
String getMapRolesPermissionName(ClientModel client)
Definition: ClientPermissions.java:80
static final String MAP_ROLES_CLIENT_SCOPE
Definition: ClientPermissionManagement.java:32
static final String MAP_ROLES_SCOPE
Definition: ClientPermissionManagement.java:31
Scope viewScope(ResourceServer server)
Definition: ClientPermissions.java:218
Scope initializeScope(String name, ResourceServer server)
Definition: MgmtPermissions.java:287
final AuthorizationProvider authz
Definition: ClientPermissions.java:57
Scope manageScope(ResourceServer server)
Definition: ClientPermissions.java:206
ResourceServer findOrCreateResourceServer(ClientModel client)
Definition: MgmtPermissions.java:240
String getResourceName(ClientModel client)
Definition: ClientPermissions.java:67
String getViewPermissionName(ClientModel client)
Definition: ClientPermissions.java:77
Policy viewPermission(ClientModel client)
Definition: ClientPermissions.java:578
String getExchangeToPermissionName(ClientModel client)
Definition: ClientPermissions.java:90
static final String MAP_ROLES_COMPOSITE_SCOPE
Definition: ClientPermissionManagement.java:33
Policy exchangeToPermission(ClientModel client)
Definition: ClientPermissions.java:536
String getMapRolesCompositePermissionName(ClientModel client)
Definition: ClientPermissions.java:86
Scope exchangeToScope(ResourceServer server)
Definition: ClientPermissions.java:210
Policy configurePermission(ClientModel client)
Definition: ClientPermissions.java:571
Resource resource(ClientModel client)
Definition: ClientPermissions.java:279
String getMapRolesClientScopePermissionName(ClientModel client)
Definition: ClientPermissions.java:83
String getManagePermissionName(ClientModel client)
Definition: ClientPermissions.java:71
Scope mapRolesScope(ResourceServer server)
Definition: ClientPermissions.java:221
final MgmtPermissions root
Definition: ClientPermissions.java:58
static final String CONFIGURE_SCOPE
Definition: ClientPermissionManagement.java:34
Scope configureScope(ResourceServer server)
Definition: ClientPermissions.java:214
String getConfigurePermissionName(ClientModel client)
Definition: ClientPermissions.java:74

 1.8.13
1.8.13