org.keycloak.protocol.oidc.endpoints.AuthorizationEndpoint の継承関係図
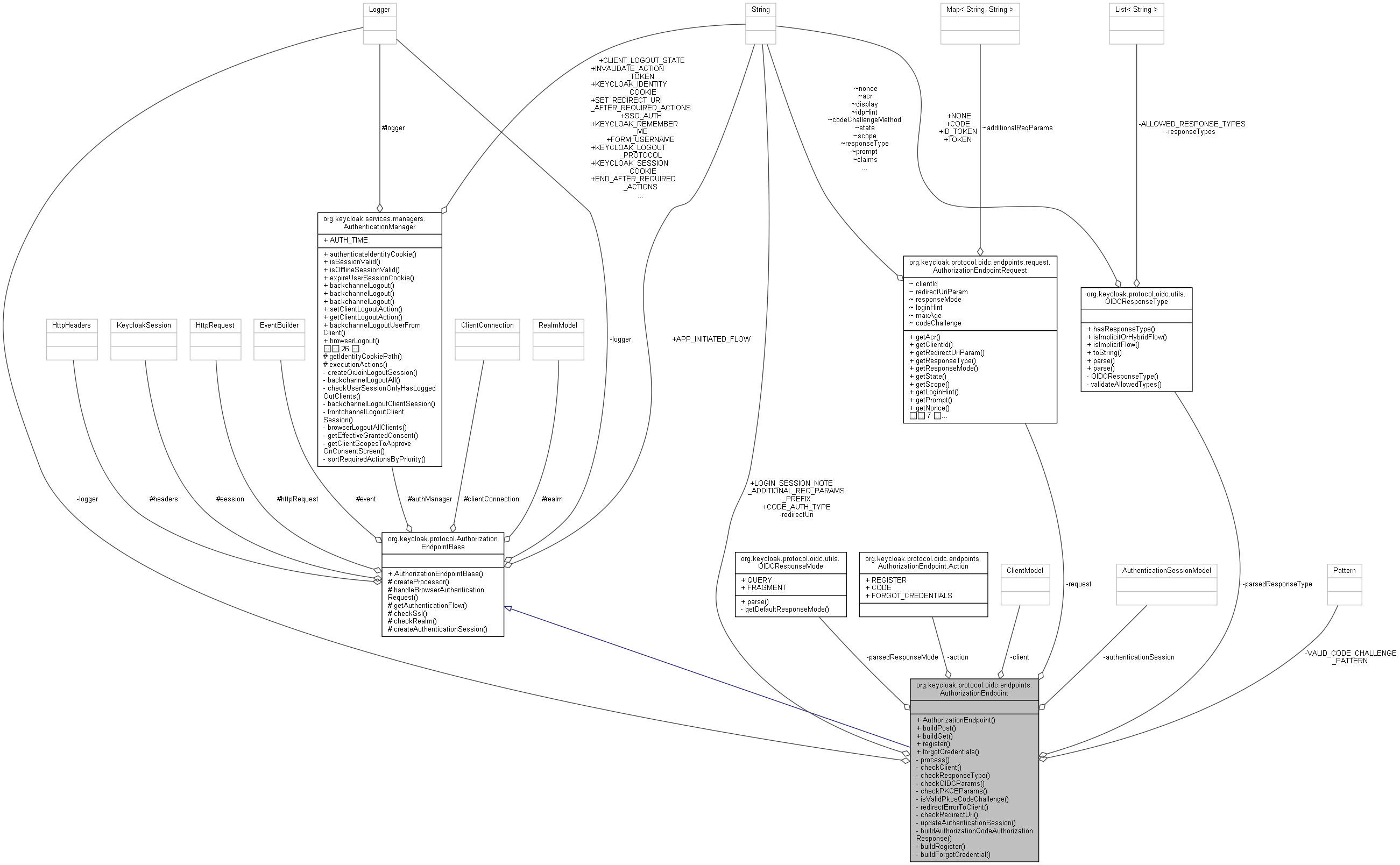
org.keycloak.protocol.oidc.endpoints.AuthorizationEndpoint 連携図
クラス | |
| enum | Action |
公開メンバ関数 | |
| AuthorizationEndpoint (RealmModel realm, EventBuilder event) | |
| Response | buildPost () |
| Response | buildGet () |
| AuthorizationEndpoint | register () |
| AuthorizationEndpoint | forgotCredentials () |
静的公開変数類 | |
| static final String | CODE_AUTH_TYPE = "code" |
| static final String | LOGIN_SESSION_NOTE_ADDITIONAL_REQ_PARAMS_PREFIX = "client_request_param_" |
| static final String | APP_INITIATED_FLOW = "APP_INITIATED_FLOW" |
限定公開メンバ関数 | |
| AuthenticationProcessor | createProcessor (AuthenticationSessionModel authSession, String flowId, String flowPath) |
| Response | handleBrowserAuthenticationRequest (AuthenticationSessionModel authSession, LoginProtocol protocol, boolean isPassive, boolean redirectToAuthentication) |
| AuthenticationFlowModel | getAuthenticationFlow (AuthenticationSessionModel authSession) |
| void | checkSsl () |
| void | checkRealm () |
| AuthenticationSessionModel | createAuthenticationSession (ClientModel client, String requestState) |
限定公開変数類 | |
| RealmModel | realm |
| EventBuilder | event |
| AuthenticationManager | authManager |
| HttpHeaders | headers |
| HttpRequest | httpRequest |
| KeycloakSession | session |
| ClientConnection | clientConnection |
非公開メンバ関数 | |
| Response | process (MultivaluedMap< String, String > params) |
| void | checkClient (String clientId) |
| Response | checkResponseType () |
| Response | checkOIDCParams () |
| Response | checkPKCEParams () |
| boolean | isValidPkceCodeChallenge (String codeChallenge) |
| Response | redirectErrorToClient (OIDCResponseMode responseMode, String error, String errorDescription) |
| void | checkRedirectUri () |
| void | updateAuthenticationSession () |
| Response | buildAuthorizationCodeAuthorizationResponse () |
| Response | buildRegister () |
| Response | buildForgotCredential () |
非公開変数類 | |
| ClientModel | client |
| AuthenticationSessionModel | authenticationSession |
| Action | action |
| OIDCResponseType | parsedResponseType |
| OIDCResponseMode | parsedResponseMode |
| AuthorizationEndpointRequest | request |
| String | redirectUri |
静的非公開変数類 | |
| static final Logger | logger = Logger.getLogger(AuthorizationEndpoint.class) |
| static final Pattern | VALID_CODE_CHALLENGE_PATTERN = Pattern.compile("^[0-9a-zA-Z\\-\\.~_]+$") |
詳解
クラス詳解
◆ org::keycloak::protocol::oidc::endpoints::AuthorizationEndpoint::Action
| enum org::keycloak::protocol::oidc::endpoints::AuthorizationEndpoint::Action |
org.keycloak.protocol.oidc.endpoints.AuthorizationEndpoint.Action 連携図
| 列挙値 | CODE | FORGOT_CREDENTIALS | REGISTER |
|---|
構築子と解体子
◆ AuthorizationEndpoint()
|
inline |
EventBuilder event
Definition: AuthorizationEndpointBase.java:61
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
関数詳解
◆ buildAuthorizationCodeAuthorizationResponse()
|
inlineprivate |
409 return handleBrowserAuthenticationRequest(authenticationSession, new OIDCLoginProtocol(session, realm, session.getContext().getUri(), headers, event), TokenUtil.hasPrompt(request.getPrompt(), OIDCLoginProtocol.PROMPT_VALUE_NONE), false);
AuthorizationEndpointRequest request
Definition: AuthorizationEndpoint.java:90
Response handleBrowserAuthenticationRequest(AuthenticationSessionModel authSession, LoginProtocol protocol, boolean isPassive, boolean redirectToAuthentication)
Definition: AuthorizationEndpointBase.java:105
static final String CODE_AUTH_TYPE
Definition: AuthorizationEndpoint.java:66
String getPrompt()
Definition: AuthorizationEndpointRequest.java:81
HttpHeaders headers
Definition: AuthorizationEndpointBase.java:65
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
EventBuilder event
Definition: AuthorizationEndpointBase.java:61
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
◆ buildForgotCredential()
|
inlineprivate |
430 AuthenticationProcessor processor = createProcessor(authenticationSession, flowId, LoginActionsService.RESET_CREDENTIALS_PATH);
431 authenticationSession.setClientNote(APP_INITIATED_FLOW, LoginActionsService.RESET_CREDENTIALS_PATH);
static void expireIdentityCookie(RealmModel realm, UriInfo uriInfo, ClientConnection connection)
Definition: AuthenticationManager.java:636
static final String APP_INITIATED_FLOW
Definition: AuthorizationEndpointBase.java:58
ClientConnection clientConnection
Definition: AuthorizationEndpointBase.java:71
AuthenticationManager authManager
Definition: AuthorizationEndpointBase.java:62
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
AuthenticationProcessor createProcessor(AuthenticationSessionModel authSession, String flowId, String flowPath)
Definition: AuthorizationEndpointBase.java:78
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
◆ buildGet()
|
inline |
static final Logger logger
Definition: AuthorizationEndpoint.java:64
Response process(MultivaluedMap< String, String > params)
Definition: AuthorizationEndpoint.java:111
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
◆ buildPost()
|
inline |
HttpRequest httpRequest
Definition: AuthorizationEndpointBase.java:67
static final Logger logger
Definition: AuthorizationEndpoint.java:64
Response process(MultivaluedMap< String, String > params)
Definition: AuthorizationEndpoint.java:111
◆ buildRegister()
|
inlineprivate |
418 AuthenticationProcessor processor = createProcessor(authenticationSession, flowId, LoginActionsService.REGISTRATION_PATH);
static void expireIdentityCookie(RealmModel realm, UriInfo uriInfo, ClientConnection connection)
Definition: AuthenticationManager.java:636
static final String APP_INITIATED_FLOW
Definition: AuthorizationEndpointBase.java:58
ClientConnection clientConnection
Definition: AuthorizationEndpointBase.java:71
AuthenticationManager authManager
Definition: AuthorizationEndpointBase.java:62
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
AuthenticationProcessor createProcessor(AuthenticationSessionModel authSession, String flowId, String flowPath)
Definition: AuthorizationEndpointBase.java:78
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
◆ checkClient()
|
inlineprivate |
183 throw new ErrorPageException(session, authenticationSession, Response.Status.BAD_REQUEST, Messages.MISSING_PARAMETER, OIDCLoginProtocol.CLIENT_ID_PARAM);
191 throw new ErrorPageException(session, authenticationSession, Response.Status.BAD_REQUEST, Messages.CLIENT_NOT_FOUND);
196 throw new ErrorPageException(session, authenticationSession, Response.Status.BAD_REQUEST, Messages.CLIENT_DISABLED);
201 throw new ErrorPageException(session, authenticationSession, Response.Status.FORBIDDEN, Messages.BEARER_ONLY);
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
ClientModel client
Definition: AuthorizationEndpoint.java:83
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
◆ checkOIDCParams()
|
inlineprivate |
265 // If request is not OIDC request, but pure OAuth2 request and response_type is just 'token', then 'nonce' is not mandatory
274 return redirectErrorToClient(parsedResponseMode, OAuthErrorException.INVALID_REQUEST, "Missing parameter: nonce");
AuthorizationEndpointRequest request
Definition: AuthorizationEndpoint.java:90
OIDCResponseMode parsedResponseMode
Definition: AuthorizationEndpoint.java:88
String toString()
Definition: OIDCResponseType.java:106
OIDCResponseType parsedResponseType
Definition: AuthorizationEndpoint.java:87
boolean isImplicitOrHybridFlow()
Definition: OIDCResponseType.java:96
Response redirectErrorToClient(OIDCResponseMode responseMode, String error, String errorDescription)
Definition: AuthorizationEndpoint.java:339
String getScope()
Definition: AuthorizationEndpointRequest.java:73
String getNonce()
Definition: AuthorizationEndpointRequest.java:85
◆ checkPKCEParams()
|
inlineprivate |
293 return redirectErrorToClient(parsedResponseMode, OAuthErrorException.INVALID_REQUEST, "Missing parameter: code_challenge");
305 if (!codeChallengeMethod.equals(OIDCLoginProtocol.PKCE_METHOD_S256) && !codeChallengeMethod.equals(OIDCLoginProtocol.PKCE_METHOD_PLAIN)) {
306 logger.infof("PKCE supporting Client with invalid code challenge method not specified in PKCE, codeChallengeMethod = %s", codeChallengeMethod);
308 return redirectErrorToClient(parsedResponseMode, OAuthErrorException.INVALID_REQUEST, "Invalid parameter: code_challenge_method");
317 logger.infof("PKCE supporting Client with invalid code challenge specified in PKCE, codeChallenge = %s", codeChallenge);
319 return redirectErrorToClient(parsedResponseMode, OAuthErrorException.INVALID_REQUEST, "Invalid parameter: code_challenge");
AuthorizationEndpointRequest request
Definition: AuthorizationEndpoint.java:90
OIDCResponseMode parsedResponseMode
Definition: AuthorizationEndpoint.java:88
OIDCResponseType parsedResponseType
Definition: AuthorizationEndpoint.java:87
boolean isImplicitFlow()
Definition: OIDCResponseType.java:100
static final Logger logger
Definition: AuthorizationEndpoint.java:64
boolean isValidPkceCodeChallenge(String codeChallenge)
Definition: AuthorizationEndpoint.java:326
String getCodeChallenge()
Definition: AuthorizationEndpointRequest.java:106
String getCodeChallengeMethod()
Definition: AuthorizationEndpointRequest.java:111
Response redirectErrorToClient(OIDCResponseMode responseMode, String error, String errorDescription)
Definition: AuthorizationEndpoint.java:339
◆ checkRealm()
|
inlineprotectedinherited |
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
◆ checkRedirectUri()
|
inlineprivate |
361 redirectUri = RedirectUtils.verifyRedirectUri(session.getContext().getUri(), redirectUriParam, realm, client, isOIDCRequest);
364 throw new ErrorPageException(session, authenticationSession, Response.Status.BAD_REQUEST, Messages.INVALID_PARAMETER, OIDCLoginProtocol.REDIRECT_URI_PARAM);
AuthorizationEndpointRequest request
Definition: AuthorizationEndpoint.java:90
String getRedirectUriParam()
Definition: AuthorizationEndpointRequest.java:57
String redirectUri
Definition: AuthorizationEndpoint.java:91
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
String getScope()
Definition: AuthorizationEndpointRequest.java:73
ClientModel client
Definition: AuthorizationEndpoint.java:83
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
◆ checkResponseType()
|
inlineprivate |
213 return redirectErrorToClient(OIDCResponseMode.QUERY, OAuthErrorException.INVALID_REQUEST, "Missing parameter: response_type");
226 return redirectErrorToClient(OIDCResponseMode.QUERY, OAuthErrorException.UNSUPPORTED_RESPONSE_TYPE, null);
235 return redirectErrorToClient(OIDCResponseMode.QUERY, OAuthErrorException.INVALID_REQUEST, "Invalid parameter: response_mode");
241 if (parsedResponseType.isImplicitOrHybridFlow() && parsedResponseMode == OIDCResponseMode.QUERY) {
244 return redirectErrorToClient(OIDCResponseMode.QUERY, OAuthErrorException.INVALID_REQUEST, "Response_mode 'query' not allowed for implicit or hybrid flow");
247 if ((parsedResponseType.hasResponseType(OIDCResponseType.CODE) || parsedResponseType.hasResponseType(OIDCResponseType.NONE)) && !client.isStandardFlowEnabled()) {
250 return redirectErrorToClient(parsedResponseMode, OAuthErrorException.UNSUPPORTED_RESPONSE_TYPE, "Client is not allowed to initiate browser login with given response_type. Standard flow is disabled for the client.");
256 return redirectErrorToClient(parsedResponseMode, OAuthErrorException.UNSUPPORTED_RESPONSE_TYPE, "Client is not allowed to initiate browser login with given response_type. Implicit flow is disabled for the client.");
AuthorizationEndpointRequest request
Definition: AuthorizationEndpoint.java:90
OIDCResponseMode parsedResponseMode
Definition: AuthorizationEndpoint.java:88
String getResponseType()
Definition: AuthorizationEndpointRequest.java:61
String getResponseMode()
Definition: AuthorizationEndpointRequest.java:65
OIDCResponseType parsedResponseType
Definition: AuthorizationEndpoint.java:87
static OIDCResponseMode parse(String responseMode, OIDCResponseType responseType)
Definition: OIDCResponseMode.java:27
static final Logger logger
Definition: AuthorizationEndpoint.java:64
static OIDCResponseType parse(String responseTypeParam)
Definition: OIDCResponseType.java:46
CODE
Definition: AuthorizationEndpoint.java:80
boolean isImplicitOrHybridFlow()
Definition: OIDCResponseType.java:96
Response redirectErrorToClient(OIDCResponseMode responseMode, String error, String errorDescription)
Definition: AuthorizationEndpoint.java:339
ClientModel client
Definition: AuthorizationEndpoint.java:83
boolean hasResponseType(String responseType)
Definition: OIDCResponseType.java:91
Action action
Definition: AuthorizationEndpoint.java:86
◆ checkSsl()
|
inlineprotectedinherited |
153 if (!session.getContext().getUri().getBaseUri().getScheme().equals("https") && realm.getSslRequired().isRequired(clientConnection)) {
ClientConnection clientConnection
Definition: AuthorizationEndpointBase.java:71
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
◆ createAuthenticationSession()
|
inlineprotectedinherited |
168 RootAuthenticationSessionModel rootAuthSession = manager.getCurrentRootAuthenticationSession(realm);
175 logger.debugf("Sent request to authz endpoint. Root authentication session with ID '%s' exists. Client is '%s' . Created new authentication session with tab ID: %s",
179 UserSessionModel userSession = userSessionCrossDCManager.getUserSessionIfExistsRemotely(manager, realm);
183 rootAuthSession = session.authenticationSessions().createRootAuthenticationSession(userSessionId, realm);
185 logger.debugf("Sent request to authz endpoint. We don't have root authentication session with ID '%s' but we have userSession." +
186 "Re-created root authentication session with same ID. Client is: %s . New authentication session tab ID: %s", userSessionId, client.getClientId(), authSession.getTabId());
190 logger.debugf("Sent request to authz endpoint. Created new root authentication session with ID '%s' . Client: %s . New authentication session tab ID: %s",
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
static final Logger logger
Definition: AuthorizationEndpointBase.java:56
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
◆ createProcessor()
|
inlineprotectedinherited |
HttpRequest httpRequest
Definition: AuthorizationEndpointBase.java:67
ClientConnection clientConnection
Definition: AuthorizationEndpointBase.java:71
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
EventBuilder event
Definition: AuthorizationEndpointBase.java:61
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
◆ forgotCredentials()
|
inline |
174 throw new ErrorPageException(session, authenticationSession, Response.Status.BAD_REQUEST, Messages.RESET_CREDENTIAL_NOT_ALLOWED);
FORGOT_CREDENTIALS
Definition: AuthorizationEndpoint.java:80
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
Action action
Definition: AuthorizationEndpoint.java:86
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
◆ getAuthenticationFlow()
|
inlineprotectedinherited |
◆ handleBrowserAuthenticationRequest()
|
inlineprotectedinherited |
Common method to handle browser authentication request in protocols unified way.
- 引数
-
authSession for current request protocol handler for protocol used to initiate login isPassive set to true if login should be passive (without login screen shown) redirectToAuthentication if true redirect to flow url. If initial call to protocol is a POST, you probably want to do this. This is so we can disable the back button on browser
- 戻り値
- response to be returned to the browser
108 AuthenticationProcessor processor = createProcessor(authSession, flowId, LoginActionsService.AUTHENTICATE_PATH);
137 RestartLoginCookie.setRestartCookie(session, realm, clientConnection, session.getContext().getUri(), authSession);
ClientConnection clientConnection
Definition: AuthorizationEndpointBase.java:71
AuthenticationFlowModel getAuthenticationFlow(AuthenticationSessionModel authSession)
Definition: AuthorizationEndpointBase.java:148
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
AuthenticationProcessor createProcessor(AuthenticationSessionModel authSession, String flowId, String flowPath)
Definition: AuthorizationEndpointBase.java:78
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
◆ isValidPkceCodeChallenge()
|
inlineprivate |
328 logger.debugf("PKCE codeChallenge length under lower limit , codeChallenge = %s", codeChallenge);
332 logger.debugf("PKCE codeChallenge length over upper limit , codeChallenge = %s", codeChallenge);
static final Logger logger
Definition: AuthorizationEndpoint.java:64
static final Pattern VALID_CODE_CHALLENGE_PATTERN
Definition: AuthorizationEndpoint.java:77
◆ process()
|
inlineprivate |
118 request = AuthorizationEndpointRequestParserProcessor.parseRequest(event, session, client, params);
AuthorizationEndpointRequest request
Definition: AuthorizationEndpoint.java:90
Response buildRegister()
Definition: AuthorizationEndpoint.java:412
AuthenticationSessionModel createAuthenticationSession(ClientModel client, String requestState)
Definition: AuthorizationEndpointBase.java:166
void checkRealm()
Definition: AuthorizationEndpointBase.java:159
String getState()
Definition: AuthorizationEndpointRequest.java:69
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
void checkClient(String clientId)
Definition: AuthorizationEndpoint.java:180
Response buildAuthorizationCodeAuthorizationResponse()
Definition: AuthorizationEndpoint.java:405
Response buildForgotCredential()
Definition: AuthorizationEndpoint.java:424
Response checkResponseType()
Definition: AuthorizationEndpoint.java:207
Response checkPKCEParams()
Definition: AuthorizationEndpoint.java:281
String getScope()
Definition: AuthorizationEndpointRequest.java:73
void checkRedirectUri()
Definition: AuthorizationEndpoint.java:354
ClientModel client
Definition: AuthorizationEndpoint.java:83
void checkSsl()
Definition: AuthorizationEndpointBase.java:152
Response checkOIDCParams()
Definition: AuthorizationEndpoint.java:264
EventBuilder event
Definition: AuthorizationEndpointBase.java:61
void updateAuthenticationSession()
Definition: AuthorizationEndpoint.java:369
Action action
Definition: AuthorizationEndpoint.java:86
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
◆ redirectErrorToClient()
|
inlineprivate |
340 OIDCRedirectUriBuilder errorResponseBuilder = OIDCRedirectUriBuilder.fromUri(redirectUri, responseMode)
AuthorizationEndpointRequest request
Definition: AuthorizationEndpoint.java:90
String redirectUri
Definition: AuthorizationEndpoint.java:91
String getState()
Definition: AuthorizationEndpointRequest.java:69
◆ register()
|
inline |
163 throw new ErrorPageException(session, authenticationSession, Response.Status.BAD_REQUEST, Messages.REGISTRATION_NOT_ALLOWED);
REGISTER
Definition: AuthorizationEndpoint.java:80
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
Action action
Definition: AuthorizationEndpoint.java:86
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
◆ updateAuthenticationSession()
|
inlineprivate |
373 authenticationSession.setClientNote(OIDCLoginProtocol.RESPONSE_TYPE_PARAM, request.getResponseType());
374 authenticationSession.setClientNote(OIDCLoginProtocol.REDIRECT_URI_PARAM, request.getRedirectUriParam());
375 authenticationSession.setClientNote(OIDCLoginProtocol.ISSUER, Urls.realmIssuer(session.getContext().getUri().getBaseUri(), realm.getName()));
377 if (request.getState() != null) authenticationSession.setClientNote(OIDCLoginProtocol.STATE_PARAM, request.getState());
378 if (request.getNonce() != null) authenticationSession.setClientNote(OIDCLoginProtocol.NONCE_PARAM, request.getNonce());
379 if (request.getMaxAge() != null) authenticationSession.setClientNote(OIDCLoginProtocol.MAX_AGE_PARAM, String.valueOf(request.getMaxAge()));
380 if (request.getScope() != null) authenticationSession.setClientNote(OIDCLoginProtocol.SCOPE_PARAM, request.getScope());
381 if (request.getLoginHint() != null) authenticationSession.setClientNote(OIDCLoginProtocol.LOGIN_HINT_PARAM, request.getLoginHint());
382 if (request.getPrompt() != null) authenticationSession.setClientNote(OIDCLoginProtocol.PROMPT_PARAM, request.getPrompt());
383 if (request.getIdpHint() != null) authenticationSession.setClientNote(AdapterConstants.KC_IDP_HINT, request.getIdpHint());
384 if (request.getResponseMode() != null) authenticationSession.setClientNote(OIDCLoginProtocol.RESPONSE_MODE_PARAM, request.getResponseMode());
385 if (request.getClaims()!= null) authenticationSession.setClientNote(OIDCLoginProtocol.CLAIMS_PARAM, request.getClaims());
386 if (request.getAcr() != null) authenticationSession.setClientNote(OIDCLoginProtocol.ACR_PARAM, request.getAcr());
387 if (request.getDisplay() != null) authenticationSession.setAuthNote(OAuth2Constants.DISPLAY, request.getDisplay());
390 if (request.getCodeChallenge() != null) authenticationSession.setClientNote(OIDCLoginProtocol.CODE_CHALLENGE_PARAM, request.getCodeChallenge());
392 authenticationSession.setClientNote(OIDCLoginProtocol.CODE_CHALLENGE_METHOD_PARAM, request.getCodeChallengeMethod());
394 authenticationSession.setClientNote(OIDCLoginProtocol.CODE_CHALLENGE_METHOD_PARAM, OIDCLoginProtocol.PKCE_METHOD_PLAIN);
399 authenticationSession.setClientNote(LOGIN_SESSION_NOTE_ADDITIONAL_REQ_PARAMS_PREFIX + paramName, request.getAdditionalReqParams().get(paramName));
AuthorizationEndpointRequest request
Definition: AuthorizationEndpoint.java:90
String getRedirectUriParam()
Definition: AuthorizationEndpointRequest.java:57
String getClaims()
Definition: AuthorizationEndpointRequest.java:97
String getAcr()
Definition: AuthorizationEndpointRequest.java:49
String getResponseType()
Definition: AuthorizationEndpointRequest.java:61
Map< String, String > getAdditionalReqParams()
Definition: AuthorizationEndpointRequest.java:101
String getResponseMode()
Definition: AuthorizationEndpointRequest.java:65
String getPrompt()
Definition: AuthorizationEndpointRequest.java:81
String getLoginHint()
Definition: AuthorizationEndpointRequest.java:77
Integer getMaxAge()
Definition: AuthorizationEndpointRequest.java:89
String getIdpHint()
Definition: AuthorizationEndpointRequest.java:93
String getCodeChallenge()
Definition: AuthorizationEndpointRequest.java:106
String redirectUri
Definition: AuthorizationEndpoint.java:91
String getCodeChallengeMethod()
Definition: AuthorizationEndpointRequest.java:111
String getState()
Definition: AuthorizationEndpointRequest.java:69
static final String LOGIN_SESSION_NOTE_ADDITIONAL_REQ_PARAMS_PREFIX
Definition: AuthorizationEndpoint.java:74
String getDisplay()
Definition: AuthorizationEndpointRequest.java:115
KeycloakSession session
Definition: AuthorizationEndpointBase.java:69
String getScope()
Definition: AuthorizationEndpointRequest.java:73
String getNonce()
Definition: AuthorizationEndpointRequest.java:85
RealmModel realm
Definition: AuthorizationEndpointBase.java:60
AuthenticationSessionModel authenticationSession
Definition: AuthorizationEndpoint.java:84
メンバ詳解
◆ action
|
private |
◆ APP_INITIATED_FLOW
|
staticinherited |
◆ authenticationSession
|
private |
◆ authManager
|
protectedinherited |
◆ client
|
private |
◆ clientConnection
|
protectedinherited |
◆ CODE_AUTH_TYPE
|
static |
◆ event
|
protectedinherited |
◆ headers
|
protectedinherited |
◆ httpRequest
|
protectedinherited |
◆ logger
|
staticprivate |
◆ LOGIN_SESSION_NOTE_ADDITIONAL_REQ_PARAMS_PREFIX
|
static |
Prefix used to store additional HTTP GET params from original client request into AuthenticationSessionModel note to be available later in Authenticators, RequiredActions etc. Prefix is used to prevent collisions with internally used notes.
- 参照
- AuthenticationSessionModel::getClientNote(String)
◆ parsedResponseMode
|
private |
◆ parsedResponseType
|
private |
◆ realm
|
protectedinherited |
◆ redirectUri
|
private |
◆ request
|
private |
◆ session
|
protectedinherited |
◆ VALID_CODE_CHALLENGE_PATTERN
|
staticprivate |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/rest-service/src/services/src/main/java/org/keycloak/protocol/oidc/endpoints/AuthorizationEndpoint.java
 1.8.13
1.8.13