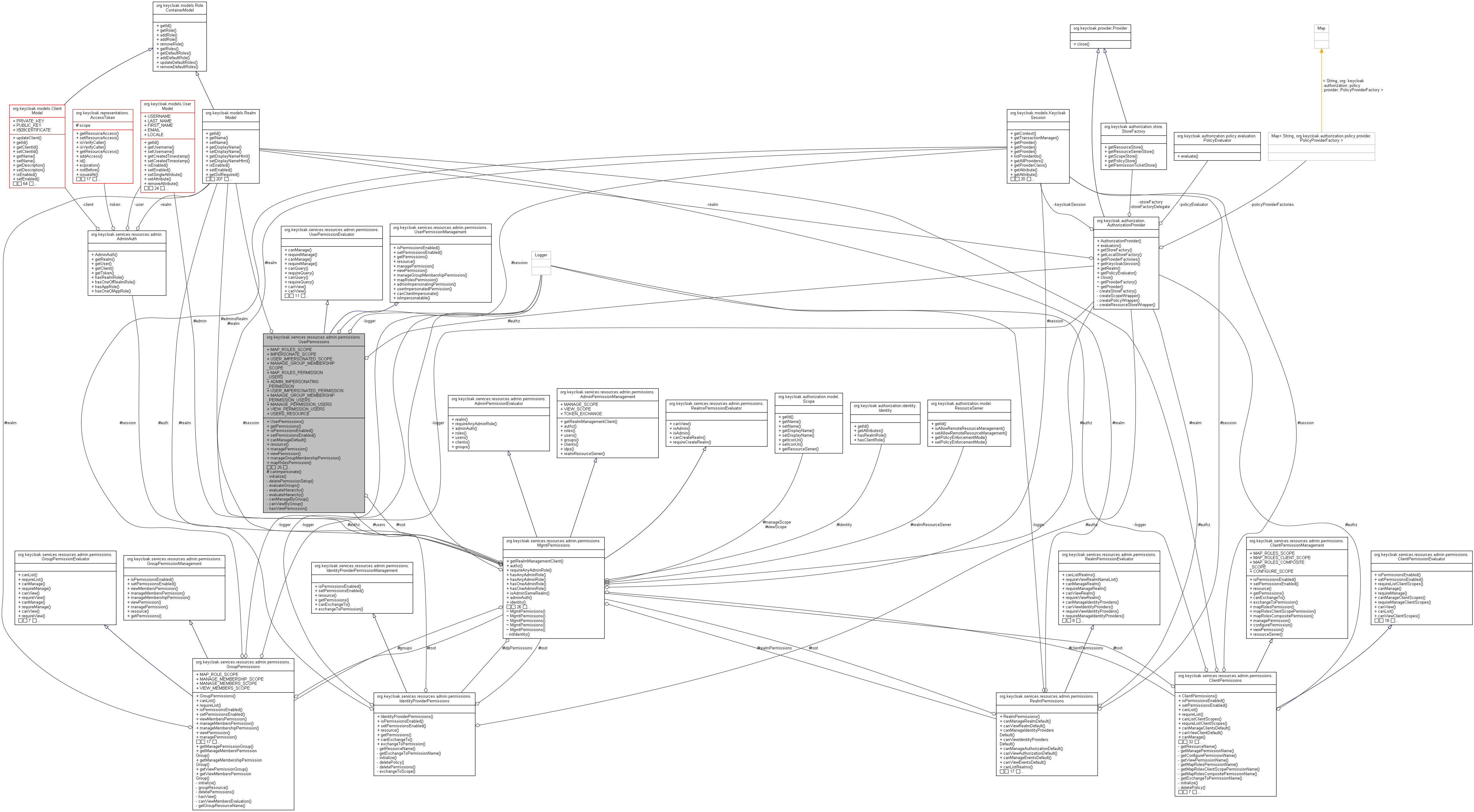
クラス | |
| interface | EvaluateGroup |
静的公開変数類 | |
| static final String | MAP_ROLES_SCOPE ="map-roles" |
| static final String | IMPERSONATE_SCOPE ="impersonate" |
| static final String | USER_IMPERSONATED_SCOPE ="user-impersonated" |
| static final String | MANAGE_GROUP_MEMBERSHIP_SCOPE ="manage-group-membership" |
| static final String | MAP_ROLES_PERMISSION_USERS = "map-roles.permission.users" |
| static final String | ADMIN_IMPERSONATING_PERMISSION = "admin-impersonating.permission.users" |
| static final String | USER_IMPERSONATED_PERMISSION = "user-impersonated.permission.users" |
| static final String | MANAGE_GROUP_MEMBERSHIP_PERMISSION_USERS = "manage-group-membership.permission.users" |
| static final String | MANAGE_PERMISSION_USERS = "manage.permission.users" |
| static final String | VIEW_PERMISSION_USERS = "view.permission.users" |
| static final String | USERS_RESOURCE = "Users" |
限定公開メンバ関数 | |
| boolean | canImpersonate (EvaluationContext context) |
限定公開変数類 | |
| final KeycloakSession | session |
| final RealmModel | realm |
| final AuthorizationProvider | authz |
| final MgmtPermissions | root |
非公開メンバ関数 | |
| void | initialize () |
| void | deletePermissionSetup () |
| boolean | evaluateGroups (UserModel user, EvaluateGroup eval) |
| boolean | evaluateHierarchy (UserModel user, EvaluateGroup eval) |
| boolean | evaluateHierarchy (EvaluateGroup eval, GroupModel group, Set< GroupModel > visited) |
| boolean | canManageByGroup (UserModel user) |
| boolean | canViewByGroup (UserModel user) |
| boolean | hasViewPermission () |
静的非公開変数類 | |
| static final Logger | logger = Logger.getLogger(UserPermissions.class) |
詳解
Manages default policies for all users.
- バージョン
- Revision
- 1
構築子と解体子
◆ UserPermissions()
|
inline |
関数詳解
◆ adminImpersonatingPermission()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ canClientImpersonate()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ canImpersonate() [1/3]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canImpersonate() [2/3]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canImpersonate() [3/3]
|
inlineprotected |
◆ canManage() [1/2]
|
inline |
Is admin allowed to manage all users? In Authz terms, does the admin have the "manage" scope for the Users Authz resource?
This method will follow the old default behavior (does the admin have the manage-users role) if any of these conditions are met.:
- The admin is from the master realm managing a different realm
- If the Authz objects are not set up correctly for the Users resource in Authz
- The "manage" permission for the Users resource has an empty associatedPolicy list.
Otherwise, it will use the Authz policy engine to resolve this answer.
- 戻り値
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canManage() [2/2]
|
inline |
Does current admin have manage permissions for this particular user?
- 引数
-
user
- 戻り値
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canManageByGroup()
|
inlineprivate |
◆ canManageDefault()
|
inline |
◆ canManageGroupMembership()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canMapRoles()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canQuery() [1/2]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canQuery() [2/2]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canView() [1/2]
|
inline |
Is admin allowed to view all users? In Authz terms, does the admin have the "view" scope for the Users Authz resource?
This method will follow the old default behavior (does the admin have the view-users role) if any of these conditions are met.:
- The admin is from the master realm managing a different realm
- If the Authz objects are not set up correctly for the Users resource in Authz
- The "view" permission for the Users resource has an empty associatedPolicy list.
Otherwise, it will use the Authz policy engine to resolve this answer.
- 戻り値
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canView() [2/2]
|
inline |
Does current admin have view permissions for this particular user?
Evaluates in this order. If any true, return true:
- canViewUsers
- canManageUsers
- 引数
-
user
- 戻り値
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ canViewByGroup()
|
inlineprivate |
◆ canViewDefault()
|
inline |
◆ deletePermissionSetup()
|
inlineprivate |
◆ evaluateGroups()
|
inlineprivate |
◆ evaluateHierarchy() [1/2]
|
inlineprivate |
◆ evaluateHierarchy() [2/2]
|
inlineprivate |
◆ getAccess()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ getPermissions()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ hasViewPermission()
|
inlineprivate |
◆ initialize()
|
inlineprivate |
◆ isImpersonatable()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ isPermissionsEnabled()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ manageGroupMembershipPermission()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ managePermission()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ mapRolesPermission()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ requireImpersonate()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ requireManage() [1/2]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ requireManage() [2/2]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ requireManageGroupMembership()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ requireMapRoles()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ requireQuery() [1/2]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ requireQuery() [2/2]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ requireView() [1/2]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ requireView() [2/2]
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionEvaluatorを実装しています。
◆ resource()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ setPermissionsEnabled()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ userImpersonatedPermission()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
◆ viewPermission()
|
inline |
org.keycloak.services.resources.admin.permissions.UserPermissionManagementを実装しています。
メンバ詳解
◆ ADMIN_IMPERSONATING_PERMISSION
|
static |
◆ authz
|
protected |
◆ IMPERSONATE_SCOPE
|
static |
◆ logger
|
staticprivate |
◆ MANAGE_GROUP_MEMBERSHIP_PERMISSION_USERS
|
static |
◆ MANAGE_GROUP_MEMBERSHIP_SCOPE
|
static |
◆ MANAGE_PERMISSION_USERS
|
static |
◆ MAP_ROLES_PERMISSION_USERS
|
static |
◆ MAP_ROLES_SCOPE
|
static |
◆ realm
|
protected |
◆ root
|
protected |
◆ session
|
protected |
◆ USER_IMPERSONATED_PERMISSION
|
static |
◆ USER_IMPERSONATED_SCOPE
|
static |
◆ USERS_RESOURCE
|
static |
◆ VIEW_PERMISSION_USERS
|
static |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/src/keycloak/src/main/java/org/keycloak/services/resources/admin/permissions/UserPermissions.java
 1.8.13
1.8.13