org.keycloak.protocol.oidc.endpoints.TokenEndpoint 連携図
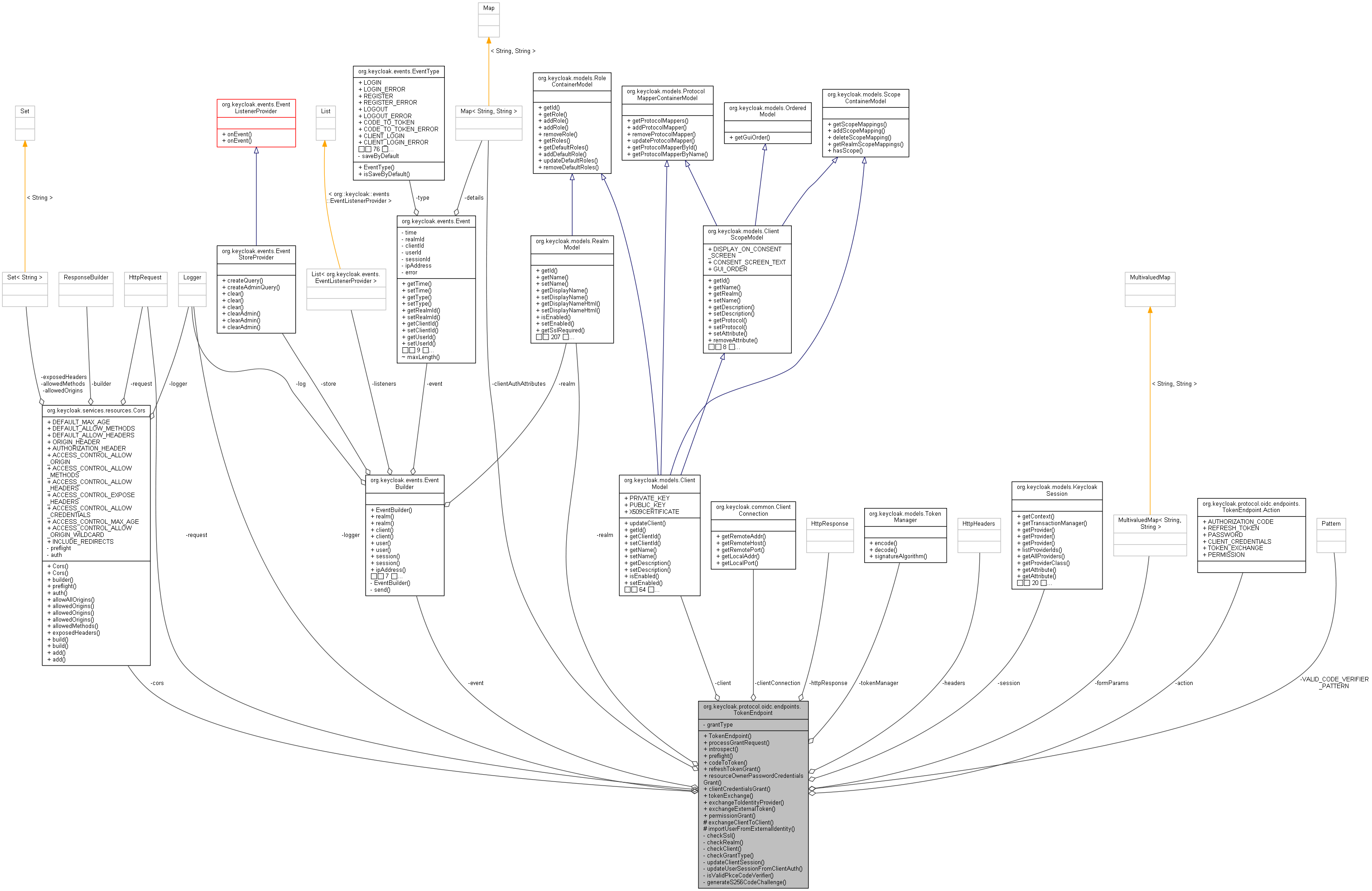
クラス | |
| enum | Action |
公開メンバ関数 | |
| TokenEndpoint (TokenManager tokenManager, RealmModel realm, EventBuilder event) | |
| Response | processGrantRequest () |
| Object | introspect () |
| Response | preflight () |
| Response | codeToToken () |
| Response | refreshTokenGrant () |
| Response | resourceOwnerPasswordCredentialsGrant () |
| Response | clientCredentialsGrant () |
| Response | tokenExchange () |
| Response | exchangeToIdentityProvider (UserModel targetUser, UserSessionModel targetUserSession, String requestedIssuer) |
| Response | exchangeExternalToken (String issuer, String subjectToken) |
| Response | permissionGrant () |
限定公開メンバ関数 | |
| Response | exchangeClientToClient (UserModel targetUser, UserSessionModel targetUserSession) |
| UserModel | importUserFromExternalIdentity (BrokeredIdentityContext context) |
非公開メンバ関数 | |
| void | checkSsl () |
| void | checkRealm () |
| void | checkClient () |
| void | checkGrantType () |
| void | updateClientSession (AuthenticatedClientSessionModel clientSession) |
| void | updateUserSessionFromClientAuth (UserSessionModel userSession) |
| boolean | isValidPkceCodeVerifier (String codeVerifier) |
| String | generateS256CodeChallenge (String codeVerifier) throws Exception |
非公開変数類 | |
| MultivaluedMap< String, String > | formParams |
| ClientModel | client |
| Map< String, String > | clientAuthAttributes |
| KeycloakSession | session |
| HttpRequest | request |
| HttpResponse | httpResponse |
| HttpHeaders | headers |
| ClientConnection | clientConnection |
| final TokenManager | tokenManager |
| final RealmModel | realm |
| final EventBuilder | event |
| Action | action |
| String | grantType |
| Cors | cors |
静的非公開変数類 | |
| static final Logger | logger = Logger.getLogger(TokenEndpoint.class) |
| static final Pattern | VALID_CODE_VERIFIER_PATTERN = Pattern.compile("^[0-9a-zA-Z\\-\\.~_]+$") |
詳解
クラス詳解
◆ org::keycloak::protocol::oidc::endpoints::TokenEndpoint::Action
| enum org::keycloak::protocol::oidc::endpoints::TokenEndpoint::Action |
org.keycloak.protocol.oidc.endpoints.TokenEndpoint.Action 連携図
| 列挙値 | AUTHORIZATION_CODE | CLIENT_CREDENTIALS | PASSWORD | PERMISSION | REFRESH_TOKEN | TOKEN_EXCHANGE |
|---|
構築子と解体子
◆ TokenEndpoint()
|
inline |
final EventBuilder event
Definition: TokenEndpoint.java:144
final TokenManager tokenManager
Definition: TokenEndpoint.java:142
final RealmModel realm
Definition: TokenEndpoint.java:143
関数詳解
◆ checkClient()
|
inlineprivate |
228 AuthorizeClientUtil.ClientAuthResult clientAuth = AuthorizeClientUtil.authorizeClient(session, event);
235 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_CLIENT, "Bearer-only not allowed", Response.Status.BAD_REQUEST);
final EventBuilder event
Definition: TokenEndpoint.java:144
KeycloakContext getContext()
Set< String > allowedOrigins
Definition: Cors.java:62
ClientModel client
Definition: TokenEndpoint.java:117
KeycloakUriInfo getUri()
Map< String, String > clientAuthAttributes
Definition: TokenEndpoint.java:118
boolean isBearerOnly()
KeycloakSession session
Definition: TokenEndpoint.java:128
◆ checkGrantType()
|
inlineprivate |
243 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_REQUEST, "Missing form parameter: " + OIDCLoginProtocol.GRANT_TYPE_PARAM, Response.Status.BAD_REQUEST);
265 throw new CorsErrorResponseException(cors, Errors.INVALID_REQUEST, "Invalid " + OIDCLoginProtocol.GRANT_TYPE_PARAM, Response.Status.BAD_REQUEST);
String grantType
Definition: TokenEndpoint.java:148
CLIENT_CREDENTIALS
Definition: TokenEndpoint.java:121
Action action
Definition: TokenEndpoint.java:146
PASSWORD
Definition: TokenEndpoint.java:121
REFRESH_TOKEN
Definition: TokenEndpoint.java:121
AUTHORIZATION_CODE
Definition: TokenEndpoint.java:121
TOKEN_EXCHANGE
Definition: TokenEndpoint.java:121
PERMISSION
Definition: TokenEndpoint.java:121
◆ checkRealm()
|
inlineprivate |
223 throw new CorsErrorResponseException(cors.allowAllOrigins(), "access_denied", "Realm not enabled", Response.Status.FORBIDDEN);
boolean isEnabled()
final RealmModel realm
Definition: TokenEndpoint.java:143
◆ checkSsl()
|
inlineprivate |
216 if (!session.getContext().getUri().getBaseUri().getScheme().equals("https") && realm.getSslRequired().isRequired(clientConnection)) {
217 throw new CorsErrorResponseException(cors.allowAllOrigins(), OAuthErrorException.INVALID_REQUEST, "HTTPS required", Response.Status.FORBIDDEN);
KeycloakContext getContext()
SslRequired getSslRequired()
final RealmModel realm
Definition: TokenEndpoint.java:143
KeycloakUriInfo getUri()
boolean isRequired(ClientConnection connection)
Definition: SslRequired.java:34
KeycloakSession session
Definition: TokenEndpoint.java:128
ClientConnection clientConnection
Definition: TokenEndpoint.java:140
◆ clientCredentialsGrant()
|
inline |
588 throw new CorsErrorResponseException(cors, OAuthErrorException.UNAUTHORIZED_CLIENT, "Bearer-only client not allowed to retrieve service account", Response.Status.UNAUTHORIZED);
592 throw new CorsErrorResponseException(cors, OAuthErrorException.UNAUTHORIZED_CLIENT, "Public client not allowed to retrieve service account", Response.Status.UNAUTHORIZED);
596 throw new CorsErrorResponseException(cors, OAuthErrorException.UNAUTHORIZED_CLIENT, "Client not enabled to retrieve service account", Response.Status.UNAUTHORIZED);
601 if (clientUser == null || client.getProtocolMapperByName(OIDCLoginProtocol.LOGIN_PROTOCOL, ServiceAccountConstants.CLIENT_ID_PROTOCOL_MAPPER) == null) {
603 logger.debugf("Service account user for client '%s' not found or default protocol mapper for service account not found. Creating now", client.getClientId());
614 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_REQUEST, "User '" + clientUsername + "' disabled", Response.Status.UNAUTHORIZED);
619 RootAuthenticationSessionModel rootAuthSession = new AuthenticationSessionManager(session).createAuthenticationSession(realm, false);
624 authSession.setClientNote(OIDCLoginProtocol.ISSUER, Urls.realmIssuer(session.getContext().getUri().getBaseUri(), realm.getName()));
627 UserSessionModel userSession = session.sessions().createUserSession(authSession.getParentSession().getId(), realm, clientUser, clientUsername,
632 ClientSessionContext clientSessionCtx = TokenManager.attachAuthenticationSession(session, userSession, authSession);
641 TokenManager.AccessTokenResponseBuilder responseBuilder = tokenManager.responseBuilder(realm, client, event, session, userSession, clientSessionCtx)
final EventBuilder event
Definition: TokenEndpoint.java:144
String getUsername()
KeycloakContext getContext()
boolean isServiceAccountsEnabled()
String getRemoteAddr()
UserSessionModel createUserSession(RealmModel realm, UserModel user, String loginUsername, String ipAddress, String authMethod, boolean rememberMe, String brokerSessionId, String brokerUserId)
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
ProtocolMapperModel getProtocolMapperByName(String protocol, String name)
ClientModel client
Definition: TokenEndpoint.java:117
final TokenManager tokenManager
Definition: TokenEndpoint.java:142
final RealmModel realm
Definition: TokenEndpoint.java:143
KeycloakUriInfo getUri()
void setNote(String name, String value)
static final Logger logger
Definition: TokenEndpoint.java:115
String getName()
String getClientId()
UserSessionProvider sessions()
boolean isBearerOnly()
KeycloakSession session
Definition: TokenEndpoint.java:128
UserModel getServiceAccount(ClientModel client)
ClientConnection clientConnection
Definition: TokenEndpoint.java:140
void updateUserSessionFromClientAuth(UserSessionModel userSession)
Definition: TokenEndpoint.java:510
boolean isPublicClient()
String getRemoteHost()
UserProvider users()
◆ codeToToken()
|
inline |
275 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_REQUEST, "Missing parameter: " + OAuth2Constants.CODE, Response.Status.BAD_REQUEST);
278 ClientSessionCode.ParseResult<AuthenticatedClientSessionModel> parseResult = ClientSessionCode.parseResult(code, null, session, realm, client, event, AuthenticatedClientSessionModel.class);
289 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Code not valid", Response.Status.BAD_REQUEST);
296 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Code is expired", Response.Status.BAD_REQUEST);
303 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "User session not found", Response.Status.BAD_REQUEST);
310 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "User not found", Response.Status.BAD_REQUEST);
317 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "User disabled", Response.Status.BAD_REQUEST);
324 if (redirectUriParam != null && redirectUriParam.contains("session_state=") && !redirectUri.contains("session_state=")) {
332 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Incorrect redirect_uri", Response.Status.BAD_REQUEST);
337 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Auth error", Response.Status.BAD_REQUEST);
342 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Client not allowed to exchange code", Response.Status.BAD_REQUEST);
347 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Session not active", Response.Status.BAD_REQUEST);
353 String codeChallengeMethod = clientSession.getNote(OIDCLoginProtocol.CODE_CHALLENGE_METHOD_PARAM);
363 logger.warnf("PKCE code verifier not specified, authUserId = %s, authUsername = %s", authUserId, authUsername);
365 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "PKCE code verifier not specified", Response.Status.BAD_REQUEST);
369 // based on whether code_challenge has been stored at corresponding authorization code request previously
374 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "PKCE invalid code verifier", Response.Status.BAD_REQUEST);
382 if (codeChallengeMethod != null && codeChallengeMethod.equals(OAuth2Constants.PKCE_METHOD_S256)) {
392 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "PKCE code verification failed, not supported algorithm specified", Response.Status.BAD_REQUEST);
395 logger.warnf("PKCE verification failed. authUserId = %s, authUsername = %s", authUserId, authUsername);
397 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "PKCE verification failed", Response.Status.BAD_REQUEST);
399 logger.debugf("PKCE verification success. codeVerifierEncoded = %s, codeChallenge = %s", codeVerifierEncoded, codeChallenge);
408 // (but in code-to-token request, it could just theoretically happen that they are not available)
413 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_SCOPE, "Client no longer has requested consent from user", Response.Status.BAD_REQUEST);
416 ClientSessionContext clientSessionCtx = DefaultClientSessionContext.fromClientSessionAndClientScopes(clientSession, clientScopes);
418 AccessToken token = tokenManager.createClientAccessToken(session, realm, client, user, userSession, clientSessionCtx);
420 TokenManager.AccessTokenResponseBuilder responseBuilder = tokenManager.responseBuilder(realm, client, event, session, userSession, clientSessionCtx)
427 AccessToken.CertConf certConf = MtlsHoKTokenUtil.bindTokenWithClientCertificate(request, session);
433 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_REQUEST, "Client Certification missing for MTLS HoK Token Binding", Response.Status.BAD_REQUEST);
final EventBuilder event
Definition: TokenEndpoint.java:144
boolean isStandardFlowEnabled()
boolean isValidPkceCodeVerifier(String codeVerifier)
Definition: TokenEndpoint.java:1144
void updateClientSession(AuthenticatedClientSessionModel clientSession)
Definition: TokenEndpoint.java:484
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
HttpRequest request
Definition: TokenEndpoint.java:131
ClientModel client
Definition: TokenEndpoint.java:117
final TokenManager tokenManager
Definition: TokenEndpoint.java:142
final RealmModel realm
Definition: TokenEndpoint.java:143
static final Logger logger
Definition: TokenEndpoint.java:115
String getClientId()
KeycloakSession session
Definition: TokenEndpoint.java:128
String generateS256CodeChallenge(String codeVerifier)
Definition: TokenEndpoint.java:1158
void updateUserSessionFromClientAuth(UserSessionModel userSession)
Definition: TokenEndpoint.java:510
◆ exchangeClientToClient()
|
inlineprotected |
805 } else if (!requestedTokenType.equals(OAuth2Constants.ACCESS_TOKEN_TYPE) && !requestedTokenType.equals(OAuth2Constants.REFRESH_TOKEN_TYPE)) {
808 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_REQUEST, "requested_token_type unsupported", Response.Status.BAD_REQUEST);
818 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_CLIENT, "Audience not found", Response.Status.BAD_REQUEST);
827 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_CLIENT, "Client requires user consent", Response.Status.BAD_REQUEST);
830 if (!targetClient.equals(client) && !AdminPermissions.management(session, realm).clients().canExchangeTo(client, targetClient)) {
833 throw new CorsErrorResponseException(cors, OAuthErrorException.ACCESS_DENIED, "Client not allowed to exchange", Response.Status.FORBIDDEN);
838 RootAuthenticationSessionModel rootAuthSession = new AuthenticationSessionManager(session).createAuthenticationSession(realm, false);
839 AuthenticationSessionModel authSession = rootAuthSession.createAuthenticationSession(targetClient);
843 authSession.setClientNote(OIDCLoginProtocol.ISSUER, Urls.realmIssuer(session.getContext().getUri().getBaseUri(), realm.getName()));
849 ClientSessionContext clientSessionCtx = TokenManager.attachAuthenticationSession(this.session, targetUserSession, authSession);
853 TokenManager.AccessTokenResponseBuilder responseBuilder = tokenManager.responseBuilder(realm, targetClient, event, this.session, targetUserSession, clientSessionCtx)
ClientModel getClientByClientId(String clientId)
final EventBuilder event
Definition: TokenEndpoint.java:144
KeycloakContext getContext()
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
ClientModel client
Definition: TokenEndpoint.java:117
final TokenManager tokenManager
Definition: TokenEndpoint.java:142
final RealmModel realm
Definition: TokenEndpoint.java:143
KeycloakUriInfo getUri()
String getName()
String getClientId()
KeycloakSession session
Definition: TokenEndpoint.java:128
void updateUserSessionFromClientAuth(UserSessionModel userSession)
Definition: TokenEndpoint.java:510
◆ exchangeExternalToken()
|
inline |
880 IdentityProviderFactory factory = IdentityBrokerService.getIdentityProviderFactory(session, idpModel);
895 throw new CorsErrorResponseException(cors, Errors.INVALID_ISSUER, "Invalid " + OAuth2Constants.SUBJECT_ISSUER + " parameter", Response.Status.BAD_REQUEST);
897 if (!AdminPermissions.management(session, realm).idps().canExchangeTo(client, externalIdpModel)) {
900 throw new CorsErrorResponseException(cors, OAuthErrorException.ACCESS_DENIED, "Client not allowed to exchange", Response.Status.FORBIDDEN);
905 throw new CorsErrorResponseException(cors, Errors.INVALID_ISSUER, "Invalid " + OAuth2Constants.SUBJECT_ISSUER + " parameter", Response.Status.BAD_REQUEST);
910 UserSessionModel userSession = session.sessions().createUserSession(realm, user, user.getUsername(), clientConnection.getRemoteAddr(), "external-exchange", false, null, null);
913 // this must exist so that we can obtain access token from user session if idp's store tokens is off
final EventBuilder event
Definition: TokenEndpoint.java:144
String getRemoteAddr()
UserSessionModel createUserSession(RealmModel realm, UserModel user, String loginUsername, String ipAddress, String authMethod, boolean rememberMe, String brokerSessionId, String brokerUserId)
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
UserModel importUserFromExternalIdentity(BrokeredIdentityContext context)
Definition: TokenEndpoint.java:922
Response exchangeClientToClient(UserModel targetUser, UserSessionModel targetUserSession)
Definition: TokenEndpoint.java:801
ClientModel client
Definition: TokenEndpoint.java:117
final RealmModel realm
Definition: TokenEndpoint.java:143
void setNote(String name, String value)
UserSessionProvider sessions()
KeycloakSession session
Definition: TokenEndpoint.java:128
ClientConnection clientConnection
Definition: TokenEndpoint.java:140
List< IdentityProviderModel > getIdentityProviders()
◆ exchangeToIdentityProvider()
|
inline |
782 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_REQUEST, "Invalid issuer", Response.Status.BAD_REQUEST);
785 IdentityProvider provider = IdentityBrokerService.getIdentityProvider(session, realm, requestedIssuer);
789 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_REQUEST, "Issuer does not support token exchange", Response.Status.BAD_REQUEST);
794 throw new CorsErrorResponseException(cors, OAuthErrorException.ACCESS_DENIED, "Client not allowed to exchange", Response.Status.FORBIDDEN);
796 Response response = ((ExchangeTokenToIdentityProviderToken)provider).exchangeFromToken(session.getContext().getUri(), event, client, targetUserSession, targetUser, formParams);
final EventBuilder event
Definition: TokenEndpoint.java:144
KeycloakContext getContext()
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
ClientModel client
Definition: TokenEndpoint.java:117
final RealmModel realm
Definition: TokenEndpoint.java:143
KeycloakUriInfo getUri()
IdentityProviderModel getIdentityProviderByAlias(String alias)
KeycloakSession session
Definition: TokenEndpoint.java:128
◆ generateS256CodeChallenge()
|
inlineprivate |
◆ importUserFromExternalIdentity()
|
inlineprotected |
933 Set<IdentityProviderMapperModel> mappers = realm.getIdentityProviderMappersByAlias(context.getIdpConfig().getAlias());
937 IdentityProviderMapper target = (IdentityProviderMapper)sessionFactory.getProviderFactory(IdentityProviderMapper.class, mapper.getIdentityProviderMapper());
942 FederatedIdentityModel federatedIdentityModel = new FederatedIdentityModel(providerId, context.getId(),
945 UserModel user = this.session.users().getUserByFederatedIdentity(federatedIdentityModel, realm);
949 logger.debugf("Federated user not found for provider '%s' and broker username '%s'.", providerId, context.getUsername());
967 throw new CorsErrorResponseException(cors, Errors.INVALID_TOKEN, "User already exists", Response.Status.BAD_REQUEST);
974 throw new CorsErrorResponseException(cors, Errors.INVALID_TOKEN, "User already exists", Response.Status.BAD_REQUEST);
985 federatedIdentityModel = new FederatedIdentityModel(context.getIdpConfig().getAlias(), context.getId(),
993 IdentityProviderMapper target = (IdentityProviderMapper)sessionFactory.getProviderFactory(IdentityProviderMapper.class, mapper.getIdentityProviderMapper());
999 logger.debugf("Email verified automatically after registration of user '%s' through Identity provider '%s' ", user.getUsername(), context.getIdpConfig().getAlias());
1005 throw new CorsErrorResponseException(cors, Errors.INVALID_TOKEN, "Invalid Token", Response.Status.BAD_REQUEST);
1008 if (session.getProvider(BruteForceProtector.class).isTemporarilyDisabled(session, realm, user)) {
1010 throw new CorsErrorResponseException(cors, Errors.INVALID_TOKEN, "Invalid Token", Response.Status.BAD_REQUEST);
1018 IdentityProviderMapper target = (IdentityProviderMapper)sessionFactory.getProviderFactory(IdentityProviderMapper.class, mapper.getIdentityProviderMapper());
boolean isBruteForceProtected()
KeycloakSessionFactory getKeycloakSessionFactory()
void addFederatedIdentity(RealmModel realm, UserModel user, FederatedIdentityModel socialLink)
boolean isRegistrationEmailAsUsername()
Set< IdentityProviderMapperModel > getIdentityProviderMappersByAlias(String brokerAlias)
final RealmModel realm
Definition: TokenEndpoint.java:143
< T extends Provider > T getProvider(Class< T > clazz)
static final Logger logger
Definition: TokenEndpoint.java:115
< T extends Provider > ProviderFactory< T > getProviderFactory(Class< T > clazz)
boolean isDuplicateEmailsAllowed()
UserModel getUserByFederatedIdentity(FederatedIdentityModel socialLink, RealmModel realm)
KeycloakSession session
Definition: TokenEndpoint.java:128
UserModel getUserByEmail(String email, RealmModel realm)
void setEnabled(boolean enabled)
UserModel addUser(RealmModel realm, String id, String username, boolean addDefaultRoles, boolean addDefaultRequiredActions)
UserModel getUserByUsername(String username, RealmModel realm)
UserProvider users()
◆ introspect()
|
inline |
◆ isValidPkceCodeVerifier()
|
inlineprivate |
1146 logger.infof(" Error: PKCE codeVerifier length under lower limit , codeVerifier = %s", codeVerifier);
1150 logger.infof(" Error: PKCE codeVerifier length over upper limit , codeVerifier = %s", codeVerifier);
static final Pattern VALID_CODE_VERIFIER_PATTERN
Definition: TokenEndpoint.java:125
static final Logger logger
Definition: TokenEndpoint.java:115
◆ permissionGrant()
|
inline |
1036 // we allow public clients to authenticate using a bearer token, where the token should be a valid access token.
1037 // public clients don't have secret and should be able to obtain a RPT by providing an access token previously issued by the server
1042 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Invalid bearer token", Status.UNAUTHORIZED);
1069 // if a claim token is provided, we check if the format is a OpenID Connect IDToken and assume the token represents the identity asking for permissions
1070 if (AuthorizationTokenService.CLAIM_TOKEN_FORMAT_ID_TOKEN.equalsIgnoreCase(claimTokenFormat)) {
1074 // In order to support cases where the client is obtaining permissions on its on behalf, we issue a temporary access token
1075 accessTokenString = AccessTokenResponse.class.cast(clientCredentialsGrant().getEntity()).getToken();
1079 AuthorizationTokenService.KeycloakAuthorizationRequest authorizationRequest = new AuthorizationTokenService.KeycloakAuthorizationRequest(session.getProvider(AuthorizationProvider.class), tokenManager, event, this.request, cors);
1091 throw new CorsErrorResponseException(cors, "invalid_rpt", "RPT signature is invalid", Status.FORBIDDEN);
1099 authorizationRequest.setSubjectToken(formParams.getFirst("subject_token") != null ? formParams.getFirst("subject_token") : accessTokenString);
1103 authorizationRequest.setSubmitRequest(submitRequest == null ? true : Boolean.valueOf(submitRequest));
ClientModel getClientByClientId(String clientId)
final EventBuilder event
Definition: TokenEndpoint.java:144
HttpHeaders headers
Definition: TokenEndpoint.java:137
Response clientCredentialsGrant()
Definition: TokenEndpoint.java:585
KeycloakContext getContext()
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
HttpRequest request
Definition: TokenEndpoint.java:131
Set< String > allowedOrigins
Definition: Cors.java:62
TokenManager tokens()
ClientModel client
Definition: TokenEndpoint.java:117
final TokenManager tokenManager
Definition: TokenEndpoint.java:142
void checkClient()
Definition: TokenEndpoint.java:227
final RealmModel realm
Definition: TokenEndpoint.java:143
< T extends Provider > T getProvider(Class< T > clazz)
KeycloakUriInfo getUri()
< T extends Token > T decode(String token, Class< T > clazz)
KeycloakSession session
Definition: TokenEndpoint.java:128
void setClient(ClientModel client)
◆ preflight()
|
inline |
212 return Cors.add(request, Response.ok()).auth().preflight().allowedMethods("POST", "OPTIONS").build();
HttpHeaders headers
Definition: TokenEndpoint.java:137
HttpRequest request
Definition: TokenEndpoint.java:131
static final Logger logger
Definition: TokenEndpoint.java:115
◆ processGrantRequest()
|
inline |
160 cors = Cors.add(request).auth().allowedMethods("POST").auth().exposedHeaders(Cors.ACCESS_CONTROL_ALLOW_METHODS);
167 // with a value of "no-store" as well as the "Pragma" response header field with a value of "no-cache".
Response clientCredentialsGrant()
Definition: TokenEndpoint.java:585
String grantType
Definition: TokenEndpoint.java:148
Action action
Definition: TokenEndpoint.java:146
Response tokenExchange()
Definition: TokenEndpoint.java:657
void checkSsl()
Definition: TokenEndpoint.java:215
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
HttpRequest request
Definition: TokenEndpoint.java:131
HttpResponse httpResponse
Definition: TokenEndpoint.java:134
Response refreshTokenGrant()
Definition: TokenEndpoint.java:448
void checkClient()
Definition: TokenEndpoint.java:227
Response codeToToken()
Definition: TokenEndpoint.java:271
void checkRealm()
Definition: TokenEndpoint.java:221
void checkGrantType()
Definition: TokenEndpoint.java:241
Response resourceOwnerPasswordCredentialsGrant()
Definition: TokenEndpoint.java:516
static Cors add(HttpRequest request, ResponseBuilder response)
Definition: Cors.java:78
Response permissionGrant()
Definition: TokenEndpoint.java:1026
◆ refreshTokenGrant()
|
inline |
451 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_REQUEST, "No refresh token", Response.Status.BAD_REQUEST);
457 TokenManager.RefreshResult result = tokenManager.refreshAccessToken(session, session.getContext().getUri(), clientConnection, realm, client, refreshToken, event, headers, request);
462 AuthenticatedClientSessionModel clientSession = userSession.getAuthenticatedClientSessionByClient(client.getId());
472 throw new CorsErrorResponseException(cors, e.getError(), e.getDescription(), Response.Status.UNAUTHORIZED);
475 throw new CorsErrorResponseException(cors, e.getError(), e.getDescription(), Response.Status.BAD_REQUEST);
final EventBuilder event
Definition: TokenEndpoint.java:144
HttpHeaders headers
Definition: TokenEndpoint.java:137
KeycloakContext getContext()
void updateClientSession(AuthenticatedClientSessionModel clientSession)
Definition: TokenEndpoint.java:484
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
HttpRequest request
Definition: TokenEndpoint.java:131
UserSessionModel getUserSession(RealmModel realm, String id)
ClientModel client
Definition: TokenEndpoint.java:117
final TokenManager tokenManager
Definition: TokenEndpoint.java:142
final RealmModel realm
Definition: TokenEndpoint.java:143
default AuthenticatedClientSessionModel getAuthenticatedClientSessionByClient(String clientUUID)
Definition: UserSessionModel.java:67
KeycloakUriInfo getUri()
static final Logger logger
Definition: TokenEndpoint.java:115
UserSessionProvider sessions()
KeycloakSession session
Definition: TokenEndpoint.java:128
ClientConnection clientConnection
Definition: TokenEndpoint.java:140
void updateUserSessionFromClientAuth(UserSessionModel userSession)
Definition: TokenEndpoint.java:510
◆ resourceOwnerPasswordCredentialsGrant()
|
inline |
521 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Client not allowed for direct access grants", Response.Status.BAD_REQUEST);
526 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_CLIENT, "Client requires user consent", Response.Status.BAD_REQUEST);
530 RootAuthenticationSessionModel rootAuthSession = new AuthenticationSessionManager(session).createAuthenticationSession(realm, false);
535 authSession.setClientNote(OIDCLoginProtocol.ISSUER, Urls.realmIssuer(session.getContext().getUri().getBaseUri(), realm.getName()));
558 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_GRANT, "Invalid user credentials", Response.Status.UNAUTHORIZED);
568 TokenManager.AccessTokenResponseBuilder responseBuilder = tokenManager.responseBuilder(realm, client, event, session, userSession, clientSessionCtx)
final EventBuilder event
Definition: TokenEndpoint.java:144
KeycloakContext getContext()
boolean isDirectAccessGrantsEnabled()
boolean isConsentRequired()
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
HttpRequest request
Definition: TokenEndpoint.java:131
HttpResponse httpResponse
Definition: TokenEndpoint.java:134
ClientModel client
Definition: TokenEndpoint.java:117
final TokenManager tokenManager
Definition: TokenEndpoint.java:142
final RealmModel realm
Definition: TokenEndpoint.java:143
KeycloakUriInfo getUri()
String getName()
KeycloakSession session
Definition: TokenEndpoint.java:128
ClientConnection clientConnection
Definition: TokenEndpoint.java:140
void updateUserSessionFromClientAuth(UserSessionModel userSession)
Definition: TokenEndpoint.java:510
◆ tokenExchange()
|
inline |
670 String realmIssuerUrl = Urls.realmIssuer(session.getContext().getUri().getBaseUri(), realm.getName());
681 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_TOKEN, "Invalid token type, must be access token", Response.Status.BAD_REQUEST);
695 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_TOKEN, "Invalid token type, must be access token", Response.Status.BAD_REQUEST);
699 AuthenticationManager.AuthResult authResult = AuthenticationManager.verifyIdentityToken(session, realm, session.getContext().getUri(), clientConnection, true, true, false, subjectToken, headers);
703 throw new CorsErrorResponseException(cors, OAuthErrorException.INVALID_TOKEN, "Invalid token", Response.Status.BAD_REQUEST);
723 throw new CorsErrorResponseException(cors, OAuthErrorException.ACCESS_DENIED, "Client not allowed to exchange", Response.Status.FORBIDDEN);
734 throw new CorsErrorResponseException(cors, OAuthErrorException.ACCESS_DENIED, "Client not allowed to exchange", Response.Status.FORBIDDEN);
738 // no token is being exchanged, this is a direct exchange. Client must be authenticated, not public, and must be allowed
743 throw new CorsErrorResponseException(cors, OAuthErrorException.ACCESS_DENIED, "Client not allowed to exchange", Response.Status.FORBIDDEN);
746 if (!AdminPermissions.management(session, realm).users().canClientImpersonate(client, requestedUser)) {
749 throw new CorsErrorResponseException(cors, OAuthErrorException.ACCESS_DENIED, "Client not allowed to exchange", Response.Status.FORBIDDEN);
754 tokenSession = session.sessions().createUserSession(realm, requestedUser, requestedUser.getUsername(), clientConnection.getRemoteAddr(), "impersonate", false, null, null);
HttpHeaders headers
Definition: TokenEndpoint.java:137
KeycloakContext getContext()
String getRemoteAddr()
UserSessionModel createUserSession(RealmModel realm, UserModel user, String loginUsername, String ipAddress, String authMethod, boolean rememberMe, String brokerSessionId, String brokerUserId)
Response exchangeToIdentityProvider(UserModel targetUser, UserSessionModel targetUserSession, String requestedIssuer)
Definition: TokenEndpoint.java:776
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
void removeUserSession(RealmModel realm, UserSessionModel session)
Response exchangeClientToClient(UserModel targetUser, UserSessionModel targetUserSession)
Definition: TokenEndpoint.java:801
ClientModel client
Definition: TokenEndpoint.java:117
final RealmModel realm
Definition: TokenEndpoint.java:143
KeycloakUriInfo getUri()
String getName()
UserSessionProvider sessions()
KeycloakSession session
Definition: TokenEndpoint.java:128
Response exchangeExternalToken(String issuer, String subjectToken)
Definition: TokenEndpoint.java:875
ClientConnection clientConnection
Definition: TokenEndpoint.java:140
UserModel getUserById(String id, RealmModel realm)
UserModel getUserByUsername(String username, RealmModel realm)
boolean isPublicClient()
UserProvider users()
◆ updateClientSession()
|
inlineprivate |
494 logger.debugf("Adapter Session '%s' saved in ClientSession for client '%s'. Host is '%s'", adapterSessionId, client.getClientId(), adapterSessionHost);
MultivaluedMap< String, String > formParams
Definition: TokenEndpoint.java:116
ClientModel client
Definition: TokenEndpoint.java:117
static final Logger logger
Definition: TokenEndpoint.java:115
String getClientId()
◆ updateUserSessionFromClientAuth()
|
inlineprivate |
Map< String, String > clientAuthAttributes
Definition: TokenEndpoint.java:118
メンバ詳解
◆ action
|
private |
◆ client
|
private |
◆ clientAuthAttributes
|
private |
◆ clientConnection
|
private |
◆ cors
|
private |
◆ event
|
private |
◆ formParams
|
private |
◆ grantType
|
private |
◆ headers
|
private |
◆ httpResponse
|
private |
◆ logger
|
staticprivate |
◆ realm
|
private |
◆ request
|
private |
◆ session
|
private |
◆ tokenManager
|
private |
◆ VALID_CODE_VERIFIER_PATTERN
|
staticprivate |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/src/keycloak/src/main/java/org/keycloak/protocol/oidc/endpoints/TokenEndpoint.java
 1.8.13
1.8.13