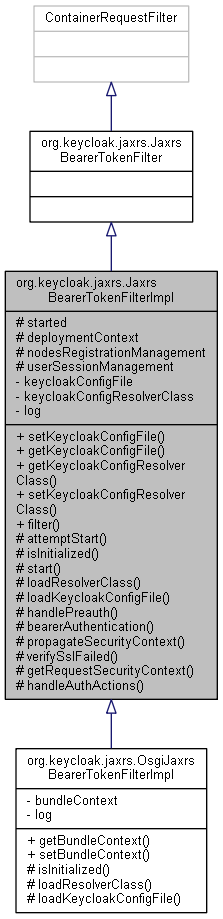
org.keycloak.jaxrs.JaxrsBearerTokenFilterImpl の継承関係図
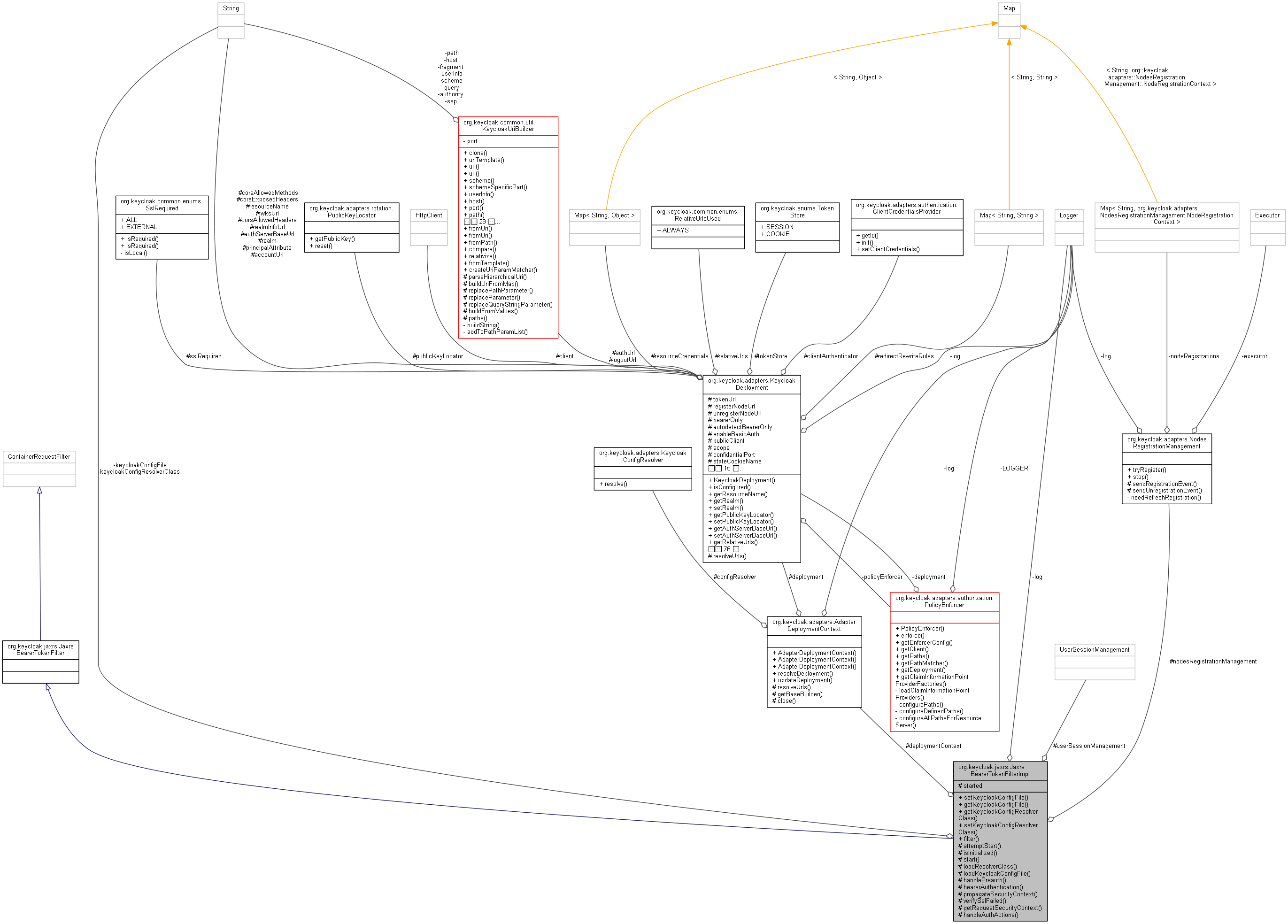
org.keycloak.jaxrs.JaxrsBearerTokenFilterImpl 連携図
クラス | |
| class | EmptyUserSessionManagement |
公開メンバ関数 | |
| void | setKeycloakConfigFile (String configFile) |
| String | getKeycloakConfigFile () |
| String | getKeycloakConfigResolverClass () |
| void | setKeycloakConfigResolverClass (String keycloakConfigResolverClass) |
| void | filter (ContainerRequestContext request) throws IOException |
限定公開メンバ関数 | |
| void | attemptStart () |
| boolean | isInitialized () |
| void | start () |
| Class<? extends KeycloakConfigResolver > | loadResolverClass () |
| InputStream | loadKeycloakConfigFile () |
| boolean | handlePreauth (JaxrsHttpFacade facade) |
| void | bearerAuthentication (JaxrsHttpFacade facade, ContainerRequestContext request, KeycloakDeployment resolvedDeployment) |
| void | propagateSecurityContext (JaxrsHttpFacade facade, ContainerRequestContext request, KeycloakDeployment resolvedDeployment, BearerTokenRequestAuthenticator bearer) |
| boolean | verifySslFailed (JaxrsHttpFacade facade, KeycloakDeployment deployment) |
| SecurityContext | getRequestSecurityContext (ContainerRequestContext request) |
| void | handleAuthActions (JaxrsHttpFacade facade, KeycloakDeployment deployment) |
限定公開変数類 | |
| volatile boolean | started |
| AdapterDeploymentContext | deploymentContext |
| NodesRegistrationManagement | nodesRegistrationManagement |
| UserSessionManagement | userSessionManagement = new EmptyUserSessionManagement() |
非公開変数類 | |
| String | keycloakConfigFile |
| String | keycloakConfigResolverClass |
静的非公開変数類 | |
| static final Logger | log = Logger.getLogger("" + JaxrsBearerTokenFilterImpl.class) |
詳解
- バージョン
- Revision
- 1
関数詳解
◆ attemptStart()
|
inlineprotected |
94 throw new IllegalStateException("Filter already started. Make sure to specify just keycloakConfigResolver or keycloakConfigFile but not both");
void start()
Definition: JaxrsBearerTokenFilterImpl.java:108
boolean isInitialized()
Definition: JaxrsBearerTokenFilterImpl.java:104
volatile boolean started
Definition: JaxrsBearerTokenFilterImpl.java:64
static final Logger log
Definition: JaxrsBearerTokenFilterImpl.java:60
◆ bearerAuthentication()
|
inlineprotected |
209 BearerTokenRequestAuthenticator authenticator = new BearerTokenRequestAuthenticator(resolvedDeployment);
boolean verifySslFailed(JaxrsHttpFacade facade, KeycloakDeployment deployment)
Definition: JaxrsBearerTokenFilterImpl.java:278
void handleAuthActions(JaxrsHttpFacade facade, KeycloakDeployment deployment)
Definition: JaxrsBearerTokenFilterImpl.java:291
static final Logger log
Definition: JaxrsBearerTokenFilterImpl.java:60
void propagateSecurityContext(JaxrsHttpFacade facade, ContainerRequestContext request, KeycloakDeployment resolvedDeployment, BearerTokenRequestAuthenticator bearer)
Definition: JaxrsBearerTokenFilterImpl.java:241
◆ filter()
|
inline |
KeycloakDeployment resolveDeployment(HttpFacade facade)
Definition: AdapterDeploymentContext.java:86
SecurityContext getRequestSecurityContext(ContainerRequestContext request)
Definition: JaxrsBearerTokenFilterImpl.java:287
void bearerAuthentication(JaxrsHttpFacade facade, ContainerRequestContext request, KeycloakDeployment resolvedDeployment)
Definition: JaxrsBearerTokenFilterImpl.java:208
boolean handlePreauth(JaxrsHttpFacade facade)
Definition: JaxrsBearerTokenFilterImpl.java:195
AdapterDeploymentContext deploymentContext
Definition: JaxrsBearerTokenFilterImpl.java:66
NodesRegistrationManagement nodesRegistrationManagement
Definition: JaxrsBearerTokenFilterImpl.java:69
void tryRegister(final KeycloakDeployment resolvedDeployment)
Definition: NodesRegistrationManagement.java:42
◆ getKeycloakConfigFile()
|
inline |
String keycloakConfigFile
Definition: JaxrsBearerTokenFilterImpl.java:62
◆ getKeycloakConfigResolverClass()
|
inline |
String keycloakConfigResolverClass
Definition: JaxrsBearerTokenFilterImpl.java:63
◆ getRequestSecurityContext()
|
inlineprotected |
◆ handleAuthActions()
|
inlineprotected |
◆ handlePreauth()
|
inlineprotected |
196 PreAuthActionsHandler handler = new PreAuthActionsHandler(userSessionManagement, deploymentContext, facade);
UserSessionManagement userSessionManagement
Definition: JaxrsBearerTokenFilterImpl.java:70
AdapterDeploymentContext deploymentContext
Definition: JaxrsBearerTokenFilterImpl.java:66
◆ isInitialized()
|
inlineprotected |
String keycloakConfigFile
Definition: JaxrsBearerTokenFilterImpl.java:62
String keycloakConfigResolverClass
Definition: JaxrsBearerTokenFilterImpl.java:63
◆ loadKeycloakConfigFile()
|
inlineprotected |
String keycloakConfigFile
Definition: JaxrsBearerTokenFilterImpl.java:62
static final Logger log
Definition: JaxrsBearerTokenFilterImpl.java:60
◆ loadResolverClass()
|
inlineprotected |
140 return (Class<? extends KeycloakConfigResolver>)getClass().getClassLoader().loadClass(keycloakConfigResolverClass);
144 return (Class<? extends KeycloakConfigResolver>)Thread.currentThread().getContextClassLoader().loadClass(keycloakConfigResolverClass);
String keycloakConfigResolverClass
Definition: JaxrsBearerTokenFilterImpl.java:63
◆ propagateSecurityContext()
|
inlineprotected |
242 RefreshableKeycloakSecurityContext skSession = new RefreshableKeycloakSecurityContext(resolvedDeployment, null, bearer.getTokenString(), bearer.getToken(), null, null, null);
244 // Not needed to do resteasy specifics as KeycloakSecurityContext can be always retrieved from SecurityContext by typecast SecurityContext.getUserPrincipal to KeycloakPrincipal
249 final KeycloakPrincipal<RefreshableKeycloakSecurityContext> principal = new KeycloakPrincipal<RefreshableKeycloakSecurityContext>(principalName, skSession);
SecurityContext getRequestSecurityContext(ContainerRequestContext request)
Definition: JaxrsBearerTokenFilterImpl.java:287
◆ setKeycloakConfigFile()
|
inline |
String keycloakConfigFile
Definition: JaxrsBearerTokenFilterImpl.java:62
void attemptStart()
Definition: JaxrsBearerTokenFilterImpl.java:92
◆ setKeycloakConfigResolverClass()
|
inline |
void attemptStart()
Definition: JaxrsBearerTokenFilterImpl.java:92
String keycloakConfigResolverClass
Definition: JaxrsBearerTokenFilterImpl.java:63
◆ start()
|
inlineprotected |
110 throw new IllegalStateException("Filter already started. Make sure to specify just keycloakConfigResolver or keycloakConfigFile but not both");
125 throw new IllegalArgumentException("You need to specify either keycloakConfigResolverClass or keycloakConfigFile in configuration");
130 log.info("Keycloak is using a per-deployment configuration loaded from: " + keycloakConfigFile);
String keycloakConfigFile
Definition: JaxrsBearerTokenFilterImpl.java:62
InputStream loadKeycloakConfigFile()
Definition: JaxrsBearerTokenFilterImpl.java:151
Class<? extends KeycloakConfigResolver > loadResolverClass()
Definition: JaxrsBearerTokenFilterImpl.java:138
volatile boolean started
Definition: JaxrsBearerTokenFilterImpl.java:64
AdapterDeploymentContext deploymentContext
Definition: JaxrsBearerTokenFilterImpl.java:66
static final Logger log
Definition: JaxrsBearerTokenFilterImpl.java:60
String keycloakConfigResolverClass
Definition: JaxrsBearerTokenFilterImpl.java:63
NodesRegistrationManagement nodesRegistrationManagement
Definition: JaxrsBearerTokenFilterImpl.java:69
◆ verifySslFailed()
|
inlineprotected |
メンバ詳解
◆ deploymentContext
|
protected |
◆ keycloakConfigFile
|
private |
◆ keycloakConfigResolverClass
|
private |
◆ log
|
staticprivate |
◆ nodesRegistrationManagement
|
protected |
◆ started
|
protected |
◆ userSessionManagement
|
protected |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/keycloak/doxygen/src/adapters/oidc/jaxrs-oauth-client/src/main/java/org/keycloak/jaxrs/JaxrsBearerTokenFilterImpl.java
 1.8.13
1.8.13