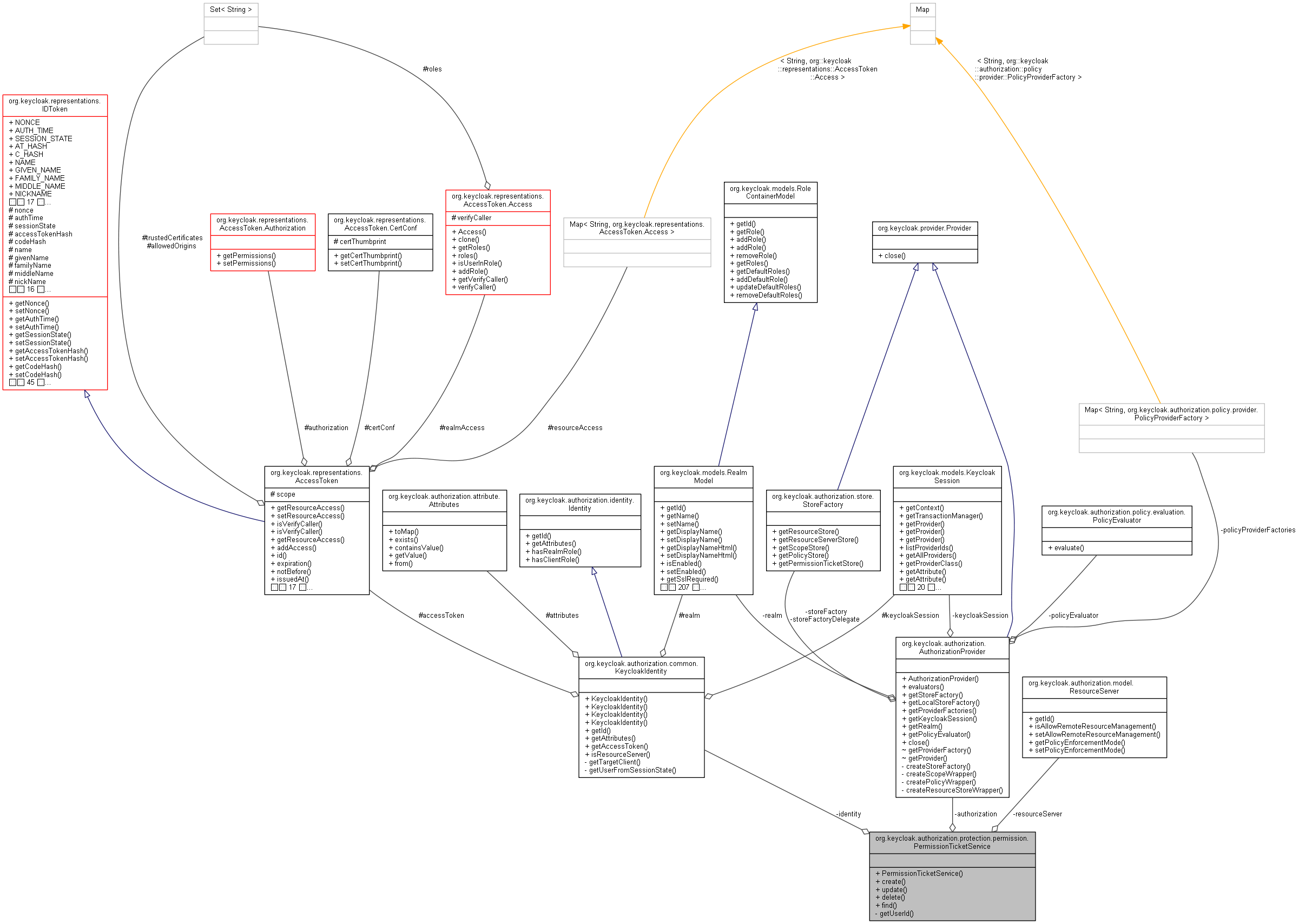
org.keycloak.authorization.protection.permission.PermissionTicketService 連携図
公開メンバ関数 | |
| PermissionTicketService (KeycloakIdentity identity, ResourceServer resourceServer, AuthorizationProvider authorization) | |
| Response | create (PermissionTicketRepresentation representation) |
| Response | update (PermissionTicketRepresentation representation) |
| Response | delete (@PathParam("id") String id) |
| Response | find (@QueryParam("scopeId") String scopeId, @QueryParam("resourceId") String resourceId, @QueryParam("owner") String owner, @QueryParam("requester") String requester, @QueryParam("granted") Boolean granted, @QueryParam("returnNames") Boolean returnNames, @QueryParam("first") Integer firstResult, @QueryParam("max") Integer maxResult) |
非公開メンバ関数 | |
| String | getUserId (String userIdOrName) |
非公開変数類 | |
| final AuthorizationProvider | authorization |
| final KeycloakIdentity | identity |
| final ResourceServer | resourceServer |
詳解
構築子と解体子
◆ PermissionTicketService()
|
inline |
final ResourceServer resourceServer
Definition: PermissionTicketService.java:61
final AuthorizationProvider authorization
Definition: PermissionTicketService.java:59
final KeycloakIdentity identity
Definition: PermissionTicketService.java:60
関数詳解
◆ create()
|
inline |
75 throw new ErrorResponseException(OAuthErrorException.INVALID_REQUEST, "invalid_permission", Response.Status.BAD_REQUEST);
77 throw new ErrorResponseException("invalid_permission", "created permissions should not have id", Response.Status.BAD_REQUEST);
79 throw new ErrorResponseException("invalid_permission", "created permissions should have resource", Response.Status.BAD_REQUEST);
81 throw new ErrorResponseException("invalid_permission", "created permissions should have scope or scopeName", Response.Status.BAD_REQUEST);
83 throw new ErrorResponseException("invalid_permission", "created permissions should have requester or requesterName", Response.Status.BAD_REQUEST);
87 if (resource == null ) throw new ErrorResponseException("invalid_resource_id", "Resource set with id [" + representation.getResource() + "] does not exists in this server.", Response.Status.BAD_REQUEST);
90 throw new ErrorResponseException("not_authorised", "permissions for [" + representation.getResource() + "] can be only created by the owner", Response.Status.FORBIDDEN);
94 user = this.authorization.getKeycloakSession().userStorageManager().getUserById(representation.getRequester(), this.authorization.getRealm());
96 user = this.authorization.getKeycloakSession().userStorageManager().getUserByUsername(representation.getRequesterName(), this.authorization.getRealm());
99 throw new ErrorResponseException("invalid_permission", "Requester does not exists in this server as user.", Response.Status.BAD_REQUEST);
110 throw new ErrorResponseException("invalid_scope", "Scope [" + representation.getScope() + "] is invalid", Response.Status.BAD_REQUEST);
112 throw new ErrorResponseException("invalid_scope", "Scope [" + representation.getScopeName() + "] is invalid", Response.Status.BAD_REQUEST);
117 throw new ErrorResponseException("invalid_resource_id", "Resource set with id [" + representation.getResource() + "] does not have Scope [" + scope.getName() + "]", Response.Status.BAD_REQUEST);
125 throw new ErrorResponseException("invalid_permission", "Permission already exists", Response.Status.BAD_REQUEST);
127 PermissionTicket ticket = ticketStore.create(resource.getId(), scope.getId(), user.getId(), resourceServer);
final ResourceServer resourceServer
Definition: PermissionTicketService.java:61
final AuthorizationProvider authorization
Definition: PermissionTicketService.java:59
PermissionTicketStore getPermissionTicketStore()
Scope findByName(String name, String resourceServerId)
final KeycloakIdentity identity
Definition: PermissionTicketService.java:60
ScopeStore getScopeStore()
RealmModel getRealm()
Definition: AuthorizationProvider.java:169
StoreFactory getStoreFactory()
Definition: AuthorizationProvider.java:109
KeycloakSession getKeycloakSession()
Definition: AuthorizationProvider.java:165
Resource findById(String id, String resourceServerId)
UserProvider userStorageManager()
String getId()
Definition: KeycloakIdentity.java:214
String getId()
ResourceStore getResourceStore()
UserModel getUserById(String id, RealmModel realm)
UserModel getUserByUsername(String username, RealmModel realm)
◆ delete()
|
inline |
162 throw new ErrorResponseException(OAuthErrorException.INVALID_REQUEST, "invalid_ticket", Response.Status.BAD_REQUEST);
169 throw new ErrorResponseException(OAuthErrorException.INVALID_REQUEST, "invalid_ticket", Response.Status.BAD_REQUEST);
172 if (!ticket.getOwner().equals(this.identity.getId()) && !this.identity.isResourceServer() && !ticket.getRequester().equals(this.identity.getId()))
173 throw new ErrorResponseException("not_authorised", "permissions for [" + ticket.getResource() + "] can be deleted only by the owner, the requester, or the resource server", Response.Status.FORBIDDEN);
final ResourceServer resourceServer
Definition: PermissionTicketService.java:61
final AuthorizationProvider authorization
Definition: PermissionTicketService.java:59
boolean isResourceServer()
Definition: KeycloakIdentity.java:232
PermissionTicketStore getPermissionTicketStore()
final KeycloakIdentity identity
Definition: PermissionTicketService.java:60
StoreFactory getStoreFactory()
Definition: AuthorizationProvider.java:109
PermissionTicket findById(String id, String resourceServerId)
String getId()
Definition: KeycloakIdentity.java:214
String getId()
◆ find()
|
inline |
222 return Response.ok().entity(permissionTicketStore.find(filters, resourceServer.getId(), firstResult != null ? firstResult : -1, maxResult != null ? maxResult : Constants.DEFAULT_MAX_RESULTS)
224 .map(permissionTicket -> ModelToRepresentation.toRepresentation(permissionTicket, authorization, returnNames == null ? false : returnNames))
final ResourceServer resourceServer
Definition: PermissionTicketService.java:61
final AuthorizationProvider authorization
Definition: PermissionTicketService.java:59
PermissionTicketStore getPermissionTicketStore()
StoreFactory getStoreFactory()
Definition: AuthorizationProvider.java:109
PermissionTicket findById(String id, String resourceServerId)
String getUserId(String userIdOrName)
Definition: PermissionTicketService.java:229
String getId()
◆ getUserId()
|
inlineprivate |
String getId()
final AuthorizationProvider authorization
Definition: PermissionTicketService.java:59
RealmModel getRealm()
Definition: AuthorizationProvider.java:169
KeycloakSession getKeycloakSession()
Definition: AuthorizationProvider.java:165
UserProvider users()
◆ update()
|
inline |
138 throw new ErrorResponseException(OAuthErrorException.INVALID_REQUEST, "invalid_ticket", Response.Status.BAD_REQUEST);
145 throw new ErrorResponseException(OAuthErrorException.INVALID_REQUEST, "invalid_ticket", Response.Status.BAD_REQUEST);
149 throw new ErrorResponseException("not_authorised", "permissions for [" + representation.getResource() + "] can be updated only by the owner or by the resource server", Response.Status.FORBIDDEN);
final ResourceServer resourceServer
Definition: PermissionTicketService.java:61
final AuthorizationProvider authorization
Definition: PermissionTicketService.java:59
boolean isResourceServer()
Definition: KeycloakIdentity.java:232
PermissionTicketStore getPermissionTicketStore()
final KeycloakIdentity identity
Definition: PermissionTicketService.java:60
StoreFactory getStoreFactory()
Definition: AuthorizationProvider.java:109
PermissionTicket findById(String id, String resourceServerId)
String getId()
Definition: KeycloakIdentity.java:214
String getId()
メンバ詳解
◆ authorization
|
private |
◆ identity
|
private |
◆ resourceServer
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/src/keycloak/src/main/java/org/keycloak/authorization/protection/permission/PermissionTicketService.java
 1.8.13
1.8.13