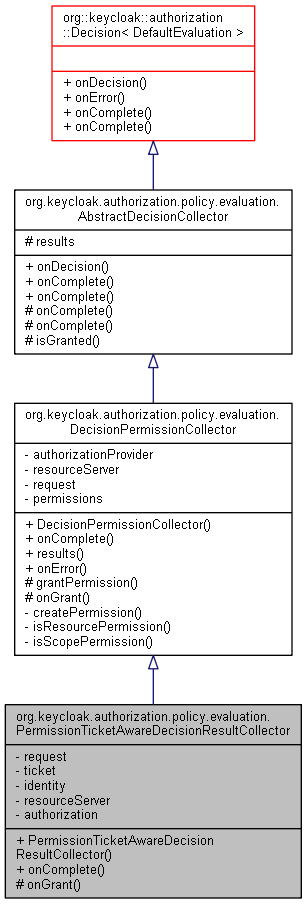
org.keycloak.authorization.policy.evaluation.PermissionTicketAwareDecisionResultCollector の継承関係図
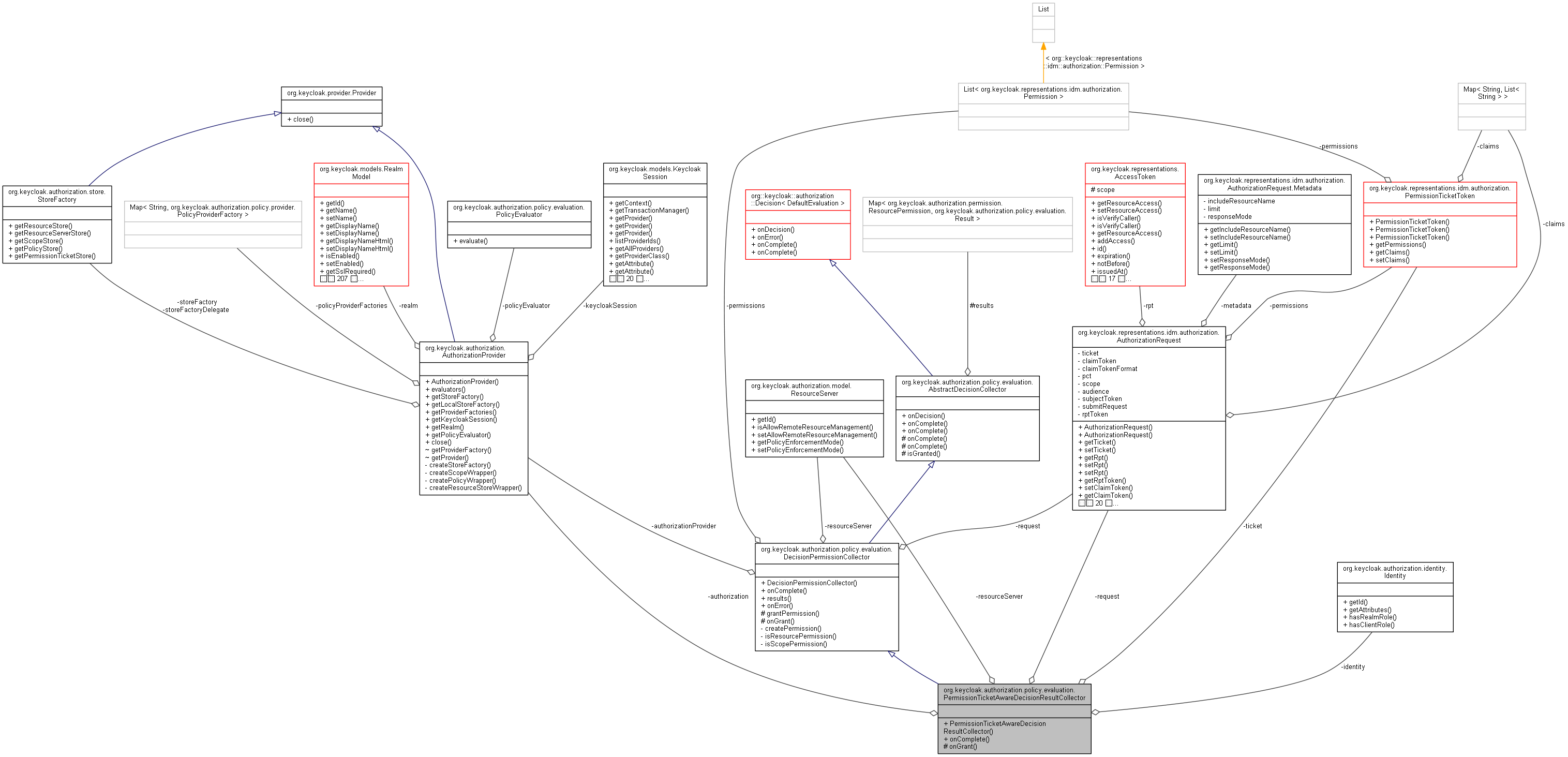
org.keycloak.authorization.policy.evaluation.PermissionTicketAwareDecisionResultCollector 連携図
公開メンバ関数 | |
| PermissionTicketAwareDecisionResultCollector (AuthorizationRequest request, PermissionTicketToken ticket, Identity identity, ResourceServer resourceServer, AuthorizationProvider authorization) | |
| void | onComplete () |
| void | onComplete (Result result) |
| void | onComplete (ResourcePermission permission) |
| Collection< Permission > | results () |
| void | onError (Throwable cause) |
| void | onDecision (DefaultEvaluation evaluation) |
| void | onDecision (D evaluation) |
限定公開メンバ関数 | |
| void | onGrant (Permission grantedPermission) |
| void | onComplete (Collection< Result > permissions) |
| void | grantPermission (AuthorizationProvider authorizationProvider, List< Permission > permissions, ResourcePermission permission, Collection< Scope > grantedScopes, ResourceServer resourceServer, AuthorizationRequest request, Result result) |
| boolean | isGranted (Result.PolicyResult policyResult) |
限定公開変数類 | |
| final Map< ResourcePermission, Result > | results = new LinkedHashMap<>() |
非公開変数類 | |
| final AuthorizationRequest | request |
| PermissionTicketToken | ticket |
| final Identity | identity |
| ResourceServer | resourceServer |
| final AuthorizationProvider | authorization |
詳解
構築子と解体子
◆ PermissionTicketAwareDecisionResultCollector()
|
inline |
final AuthorizationRequest request
Definition: PermissionTicketAwareDecisionResultCollector.java:48
final Identity identity
Definition: PermissionTicketAwareDecisionResultCollector.java:50
PermissionTicketToken ticket
Definition: PermissionTicketAwareDecisionResultCollector.java:49
final AuthorizationProvider authorization
Definition: PermissionTicketAwareDecisionResultCollector.java:52
ResourceServer resourceServer
Definition: PermissionTicketAwareDecisionResultCollector.java:51
関数詳解
◆ grantPermission()
|
inlineprotectedinherited |
140 Set<String> scopeNames = grantedScopes.stream().map(Scope::getName).collect(Collectors.toSet());
148 resourceStore.findByScope(grantedScopes.stream().map(Scope::getId).collect(Collectors.toList()), resourceServer.getId(), resource1 -> permissions.add(createPermission(resource, scopeNames, permission.getClaims(), request)));
String getName()
Permission createPermission(Resource resource, Set< String > scopes, Map< String, Set< String >> claims, AuthorizationRequest request)
Definition: DecisionPermissionCollector.java:156
StoreFactory getStoreFactory()
Definition: AuthorizationProvider.java:109
String getId()
final ResourceServer resourceServer
Definition: DecisionPermissionCollector.java:45
final List< Permission > permissions
Definition: DecisionPermissionCollector.java:47
final AuthorizationProvider authorizationProvider
Definition: DecisionPermissionCollector.java:44
String getId()
final AuthorizationRequest request
Definition: DecisionPermissionCollector.java:46
ResourceStore getResourceStore()
List< Resource > findByScope(List< String > id, String resourceServerId)
◆ isGranted()
|
inlineprotectedinherited |
◆ onComplete() [1/4]
|
inlineinherited |
62 grantPermission(authorizationProvider, permissions, permission, resource != null ? resource.getScopes() : requestedScopes, resourceServer, request, result);
83 } else if (resource != null && resource.isOwnerManagedAccess() && "uma".equals(policy.getType())) {
126 grantPermission(authorizationProvider, permissions, permission, grantedScopes, resourceServer, request, result);
static boolean isScopePermission(Policy policy)
Definition: DecisionPermissionCollector.java:185
boolean isGranted(Result.PolicyResult policyResult)
Definition: AbstractDecisionCollector.java:98
final ResourceServer resourceServer
Definition: DecisionPermissionCollector.java:45
final List< Permission > permissions
Definition: DecisionPermissionCollector.java:47
final AuthorizationProvider authorizationProvider
Definition: DecisionPermissionCollector.java:44
final AuthorizationRequest request
Definition: DecisionPermissionCollector.java:46
static boolean isResourcePermission(Policy policy)
Definition: DecisionPermissionCollector.java:181
void grantPermission(AuthorizationProvider authorizationProvider, List< Permission > permissions, ResourcePermission permission, Collection< Scope > grantedScopes, ResourceServer resourceServer, AuthorizationRequest request, Result result)
Definition: DecisionPermissionCollector.java:139
◆ onComplete() [2/4]
|
inlineinherited |
org.keycloak.authorization.Decision< D extends Evaluation >を実装しています。
final Map< ResourcePermission, Result > results
Definition: AbstractDecisionCollector.java:35
void onComplete()
Definition: AbstractDecisionCollector.java:77
◆ onComplete() [3/4]
|
inline |
org.keycloak.authorization.Decision< D extends Evaluation >を実装しています。
103 resource = resourceStore.findByName(permission.getResourceId(), identity.getId(), resourceServer.getId());
106 if (resource == null || !resource.isOwnerManagedAccess() || resource.getOwner().equals(identity.getId()) || resource.getOwner().equals(resourceServer.getId())) {
123 List<PermissionTicket> tickets = authorization.getStoreFactory().getPermissionTicketStore().find(filters, resource.getResourceServer().getId(), -1, -1);
126 authorization.getStoreFactory().getPermissionTicketStore().create(resource.getId(), null, identity.getId(), resource.getResourceServer());
144 List<PermissionTicket> tickets = authorization.getStoreFactory().getPermissionTicketStore().find(filters, resource.getResourceServer().getId(), -1, -1);
147 authorization.getStoreFactory().getPermissionTicketStore().create(resource.getId(), scope.getId(), identity.getId(), resource.getResourceServer());
final AuthorizationRequest request
Definition: PermissionTicketAwareDecisionResultCollector.java:48
String getId()
final Identity identity
Definition: PermissionTicketAwareDecisionResultCollector.java:50
PermissionTicketToken ticket
Definition: PermissionTicketAwareDecisionResultCollector.java:49
PermissionTicketStore getPermissionTicketStore()
Scope findByName(String name, String resourceServerId)
String getName()
List< Permission > getPermissions()
Definition: PermissionTicketToken.java:64
final AuthorizationProvider authorization
Definition: PermissionTicketAwareDecisionResultCollector.java:52
ScopeStore getScopeStore()
StoreFactory getStoreFactory()
Definition: AuthorizationProvider.java:109
ResourceServer resourceServer
Definition: PermissionTicketAwareDecisionResultCollector.java:51
PermissionTicket create(String resourceId, String scopeId, String requester, ResourceServer resourceServer)
final List< Permission > permissions
Definition: DecisionPermissionCollector.java:47
List< PermissionTicket > find(Map< String, String > attributes, String resourceServerId, int firstResult, int maxResult)
boolean isSubmitRequest()
Definition: AuthorizationRequest.java:181
String getId()
ResourceStore getResourceStore()
◆ onComplete() [4/4]
|
inlineprotectedinherited |
◆ onDecision() [1/2]
|
inherited |
◆ onDecision() [2/2]
|
inlineinherited |
69 results.computeIfAbsent(permission, p -> new Result(p, evaluation)).policy(parentPolicy).policy(evaluation.getPolicy(), evaluation.getEffect());
72 results.computeIfAbsent(permission, p -> new Result(p, evaluation)).setStatus(evaluation.getEffect());
final Map< ResourcePermission, Result > results
Definition: AbstractDecisionCollector.java:35
◆ onError()
|
inlineinherited |
◆ onGrant()
|
inlineprotected |
65 // Removes permissions (represented by {@code ticket}) granted by any user-managed policy so we don't create unnecessary permission tickets.
72 if (permission.getResourceId() == null || permission.getResourceId().equals(grantedPermission.getResourceId())) {
PermissionTicketToken ticket
Definition: PermissionTicketAwareDecisionResultCollector.java:49
List< Permission > getPermissions()
Definition: PermissionTicketToken.java:64
final List< Permission > permissions
Definition: DecisionPermissionCollector.java:47
◆ results()
|
inlineinherited |
final List< Permission > permissions
Definition: DecisionPermissionCollector.java:47
メンバ詳解
◆ authorization
|
private |
◆ identity
|
private |
◆ request
|
private |
◆ resourceServer
|
private |
◆ results
|
protectedinherited |
◆ ticket
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/src/keycloak/src/main/java/org/keycloak/authorization/policy/evaluation/PermissionTicketAwareDecisionResultCollector.java
 1.8.13
1.8.13