org.keycloak.storage.ldap.LDAPStorageProvider の継承関係図
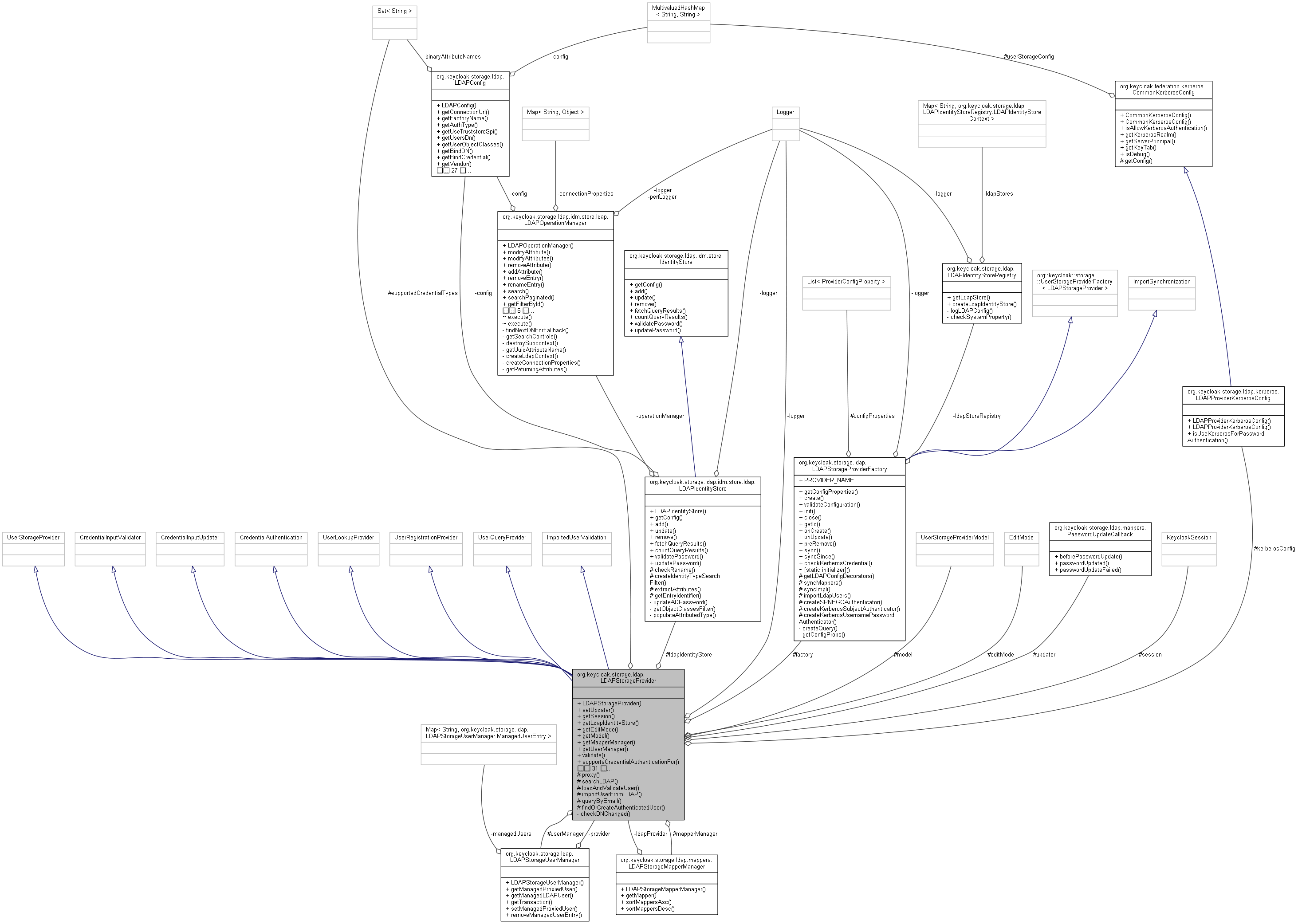
org.keycloak.storage.ldap.LDAPStorageProvider 連携図
公開メンバ関数 | |
| LDAPStorageProvider (LDAPStorageProviderFactory factory, KeycloakSession session, ComponentModel model, LDAPIdentityStore ldapIdentityStore) | |
| void | setUpdater (PasswordUpdateCallback updater) |
| KeycloakSession | getSession () |
| LDAPIdentityStore | getLdapIdentityStore () |
| EditMode | getEditMode () |
| UserStorageProviderModel | getModel () |
| LDAPStorageMapperManager | getMapperManager () |
| LDAPStorageUserManager | getUserManager () |
| UserModel | validate (RealmModel realm, UserModel local) |
| boolean | supportsCredentialAuthenticationFor (String type) |
| List< UserModel > | searchForUserByUserAttribute (String attrName, String attrValue, RealmModel realm) |
| boolean | synchronizeRegistrations () |
| UserModel | addUser (RealmModel realm, String username) |
| boolean | removeUser (RealmModel realm, UserModel user) |
| UserModel | getUserById (String id, RealmModel realm) |
| int | getUsersCount (RealmModel realm) |
| List< UserModel > | getUsers (RealmModel realm) |
| List< UserModel > | getUsers (RealmModel realm, int firstResult, int maxResults) |
| List< UserModel > | searchForUser (String search, RealmModel realm) |
| List< UserModel > | searchForUser (String search, RealmModel realm, int firstResult, int maxResults) |
| List< UserModel > | searchForUser (Map< String, String > params, RealmModel realm) |
| List< UserModel > | searchForUser (Map< String, String > params, RealmModel realm, int firstResult, int maxResults) |
| List< UserModel > | getGroupMembers (RealmModel realm, GroupModel group) |
| List< UserModel > | getGroupMembers (RealmModel realm, GroupModel group, int firstResult, int maxResults) |
| List< UserModel > | loadUsersByUsernames (List< String > usernames, RealmModel realm) |
| UserModel | getUserByUsername (String username, RealmModel realm) |
| UserModel | getUserByEmail (String email, RealmModel realm) |
| void | preRemove (RealmModel realm) |
| void | preRemove (RealmModel realm, RoleModel role) |
| void | preRemove (RealmModel realm, GroupModel group) |
| boolean | validPassword (RealmModel realm, UserModel user, String password) |
| boolean | updateCredential (RealmModel realm, UserModel user, CredentialInput input) |
| void | disableCredentialType (RealmModel realm, UserModel user, String credentialType) |
| Set< String > | getDisableableCredentialTypes (RealmModel realm, UserModel user) |
| Set< String > | getSupportedCredentialTypes () |
| boolean | supportsCredentialType (String credentialType) |
| boolean | isConfiguredFor (RealmModel realm, UserModel user, String credentialType) |
| boolean | isValid (RealmModel realm, UserModel user, CredentialInput input) |
| CredentialValidationOutput | authenticate (RealmModel realm, CredentialInput cred) |
| void | close () |
| LDAPObject | loadLDAPUserByUsername (RealmModel realm, String username) |
限定公開メンバ関数 | |
| UserModel | proxy (RealmModel realm, UserModel local, LDAPObject ldapObject) |
| List< LDAPObject > | searchLDAP (RealmModel realm, Map< String, String > attributes, int maxResults) |
| LDAPObject | loadAndValidateUser (RealmModel realm, UserModel local) |
| UserModel | importUserFromLDAP (KeycloakSession session, RealmModel realm, LDAPObject ldapUser) |
| LDAPObject | queryByEmail (RealmModel realm, String email) |
| UserModel | findOrCreateAuthenticatedUser (RealmModel realm, String username) |
限定公開変数類 | |
| LDAPStorageProviderFactory | factory |
| KeycloakSession | session |
| UserStorageProviderModel | model |
| LDAPIdentityStore | ldapIdentityStore |
| EditMode | editMode |
| LDAPProviderKerberosConfig | kerberosConfig |
| PasswordUpdateCallback | updater |
| LDAPStorageMapperManager | mapperManager |
| LDAPStorageUserManager | userManager |
| final Set< String > | supportedCredentialTypes = new HashSet<>() |
非公開メンバ関数 | |
| void | checkDNChanged (RealmModel realm, UserModel local, LDAPObject ldapObject) |
静的非公開変数類 | |
| static final Logger | logger = Logger.getLogger(LDAPStorageProvider.class) |
詳解
- バージョン
- Revision
- 1
構築子と解体子
◆ LDAPStorageProvider()
|
inline |
LDAPStorageProviderFactory factory
Definition: LDAPStorageProvider.java:86
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
EditMode editMode
Definition: LDAPStorageProvider.java:90
UserStorageProvider.EditMode getEditMode()
Definition: LDAPConfig.java:222
boolean isAllowKerberosAuthentication()
Definition: CommonKerberosConfig.java:49
final Set< String > supportedCredentialTypes
Definition: LDAPStorageProvider.java:100
KeycloakSession session
Definition: LDAPStorageProvider.java:87
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
LDAPProviderKerberosConfig kerberosConfig
Definition: LDAPStorageProvider.java:91
LDAPStorageUserManager userManager
Definition: LDAPStorageProvider.java:94
LDAPStorageMapperManager mapperManager
Definition: LDAPStorageProvider.java:93
LDAPConfig getConfig()
Definition: LDAPIdentityStore.java:83
関数詳解
◆ addUser()
|
inline |
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
KeycloakSession session
Definition: LDAPStorageProvider.java:87
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
boolean synchronizeRegistrations()
Definition: LDAPStorageProvider.java:241
UserModel proxy(RealmModel realm, UserModel local, LDAPObject ldapObject)
Definition: LDAPStorageProvider.java:157
LDAPConfig getConfig()
Definition: LDAPIdentityStore.java:83
◆ authenticate()
|
inline |
679 SPNEGOAuthenticator spnegoAuthenticator = factory.createSPNEGOAuthenticator(spnegoToken, kerberosConfig);
686 // TODO: This assumes that LDAP "uid" is equal to kerberos principal name. Like uid "hnelson" and kerberos principal "hnelson@KEYCLOAK.ORG".
687 // Check if it's correct or if LDAP attribute for mapping kerberos principal should be available (For ApacheDS it seems to be attribute "krb5PrincipalName" but on MSAD it's likely different)
692 logger.warnf("Kerberos/SPNEGO authentication succeeded with username [%s], but couldn't find or create user with federation provider [%s]", username, model.getName());
700 return new CredentialValidationOutput(user, CredentialValidationOutput.Status.AUTHENTICATED, state);
LDAPStorageProviderFactory factory
Definition: LDAPStorageProvider.java:86
static final Logger logger
Definition: LDAPStorageProvider.java:84
boolean isAllowKerberosAuthentication()
Definition: CommonKerberosConfig.java:49
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
LDAPProviderKerberosConfig kerberosConfig
Definition: LDAPStorageProvider.java:91
SPNEGOAuthenticator createSPNEGOAuthenticator(String spnegoToken, CommonKerberosConfig kerberosConfig)
Definition: LDAPStorageProviderFactory.java:616
UserModel findOrCreateAuthenticatedUser(RealmModel realm, String username)
Definition: LDAPStorageProvider.java:723
void authenticate()
Definition: SPNEGOAuthenticator.java:61
◆ checkDNChanged()
|
inlineprivate |
static final Logger logger
Definition: LDAPStorageProvider.java:84
KeycloakSession session
Definition: LDAPStorageProvider.java:87
◆ close()
◆ disableCredentialType()
|
inline |
◆ findOrCreateAuthenticatedUser()
|
inlineprotected |
Called after successful kerberos authentication
- 引数
-
realm realm username username without realm prefix
- 戻り値
- finded or newly created user
728 logger.warnf("User with username [%s] already exists, but is not linked to provider [%s]", username, model.getName());
735 logger.warnf("User with username [%s] aready exists and is linked to provider [%s] but is not valid. Stale LDAP_ID on local user is: %s",
748 logger.debugf("Kerberos authenticated user [%s] not in Keycloak storage. Creating him", username);
UserModel getUserByUsername(String username, RealmModel realm)
Definition: LDAPStorageProvider.java:476
static final Logger logger
Definition: LDAPStorageProvider.java:84
LDAPObject loadAndValidateUser(RealmModel realm, UserModel local)
Definition: LDAPStorageProvider.java:455
KeycloakSession session
Definition: LDAPStorageProvider.java:87
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
UserModel proxy(RealmModel realm, UserModel local, LDAPObject ldapObject)
Definition: LDAPStorageProvider.java:157
◆ getDisableableCredentialTypes()
|
inline |
◆ getEditMode()
|
inline |
EditMode editMode
Definition: LDAPStorageProvider.java:90
◆ getGroupMembers() [1/2]
|
inline |
List< UserModel > getGroupMembers(RealmModel realm, GroupModel group)
Definition: LDAPStorageProvider.java:370
◆ getGroupMembers() [2/2]
|
inline |
376 List<ComponentModel> mappers = realm.getComponents(model.getId(), LDAPStorageMapper.class.getName());
List< ComponentModel > sortMappersAsc(Collection< ComponentModel > mappers)
Definition: LDAPStorageMapperManager.java:50
LDAPStorageMapper getMapper(ComponentModel mapperModel)
Definition: LDAPStorageMapperManager.java:40
List< UserModel > getGroupMembers(RealmModel realm, GroupModel group, int firstResult, int maxResults)
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
LDAPStorageMapperManager mapperManager
Definition: LDAPStorageProvider.java:93
◆ getLdapIdentityStore()
|
inline |
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
◆ getMapperManager()
|
inline |
LDAPStorageMapperManager mapperManager
Definition: LDAPStorageProvider.java:93
◆ getModel()
|
inline |
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
◆ getSession()
|
inline |
KeycloakSession session
Definition: LDAPStorageProvider.java:87
◆ getSupportedCredentialTypes()
|
inline |
final Set< String > supportedCredentialTypes
Definition: LDAPStorageProvider.java:100
◆ getUserByEmail()
|
inline |
546 // If email attribute mapper is set to "Always Read Value From LDAP" the user may be in Keycloak DB with an old email address
548 throw new ModelDuplicateException("User with username '" + ldapUsername + "' already exists in Keycloak. It conflicts with LDAP user with email '" + email + "'");
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
UserModel importUserFromLDAP(KeycloakSession session, RealmModel realm, LDAPObject ldapUser)
Definition: LDAPStorageProvider.java:485
LDAPObject queryByEmail(RealmModel realm, String email)
Definition: LDAPStorageProvider.java:521
KeycloakSession session
Definition: LDAPStorageProvider.java:87
LDAPConfig getConfig()
Definition: LDAPIdentityStore.java:83
◆ getUserById()
|
inline |
UserModel getUserByUsername(String username, RealmModel realm)
Definition: LDAPStorageProvider.java:476
LDAPStorageUserManager userManager
Definition: LDAPStorageProvider.java:94
UserModel getManagedProxiedUser(String userId)
Definition: LDAPStorageUserManager.java:41
◆ getUserByUsername()
|
inline |
UserModel importUserFromLDAP(KeycloakSession session, RealmModel realm, LDAPObject ldapUser)
Definition: LDAPStorageProvider.java:485
LDAPObject loadLDAPUserByUsername(RealmModel realm, String username)
Definition: LDAPStorageProvider.java:752
KeycloakSession session
Definition: LDAPStorageProvider.java:87
◆ getUserManager()
|
inline |
LDAPStorageUserManager userManager
Definition: LDAPStorageProvider.java:94
◆ getUsers() [1/2]
|
inline |
◆ getUsers() [2/2]
|
inline |
◆ getUsersCount()
|
inline |
◆ importUserFromLDAP()
|
inlineprotected |
493 InMemoryUserAdapter adapter = new InMemoryUserAdapter(session, realm, new StorageId(model.getId(), ldapUsername).getId());
499 List<ComponentModel> mappers = realm.getComponents(model.getId(), LDAPStorageMapper.class.getName());
515 logger.debugf("Imported new user from LDAP to Keycloak DB. Username: [%s], Email: [%s], LDAP_ID: [%s], LDAP Entry DN: [%s]", imported.getUsername(), imported.getEmail(),
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
LDAPStorageMapper getMapper(ComponentModel mapperModel)
Definition: LDAPStorageMapperManager.java:40
void onImportUserFromLDAP(LDAPObject ldapUser, UserModel user, RealmModel realm, boolean isCreate)
static final Logger logger
Definition: LDAPStorageProvider.java:84
KeycloakSession session
Definition: LDAPStorageProvider.java:87
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
LDAPStorageMapperManager mapperManager
Definition: LDAPStorageProvider.java:93
List< ComponentModel > sortMappersDesc(Collection< ComponentModel > mappers)
Definition: LDAPStorageMapperManager.java:54
UserModel proxy(RealmModel realm, UserModel local, LDAPObject ldapObject)
Definition: LDAPStorageProvider.java:157
LDAPConfig getConfig()
Definition: LDAPIdentityStore.java:83
◆ isConfiguredFor()
|
inline |
Set< String > getSupportedCredentialTypes()
Definition: LDAPStorageProvider.java:647
◆ isValid()
|
inline |
665 if (input.getType().equals(UserCredentialModel.PASSWORD) && !session.userCredentialManager().isConfiguredLocally(realm, user, UserCredentialModel.PASSWORD)) {
boolean validPassword(RealmModel realm, UserModel user, String password)
Definition: LDAPStorageProvider.java:569
KeycloakSession session
Definition: LDAPStorageProvider.java:87
◆ loadAndValidateUser()
|
inlineprotected |
- 引数
-
local
- 戻り値
- ldapUser corresponding to local user or null if user is no longer in LDAP
470 logger.warnf("LDAP User invalid. ID doesn't match. ID from LDAP [%s], LDAP ID from local DB: [%s]", ldapUser.getUuid(), local.getFirstAttribute(LDAPConstants.LDAP_ID));
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
LDAPObject loadLDAPUserByUsername(RealmModel realm, String username)
Definition: LDAPStorageProvider.java:752
static final Logger logger
Definition: LDAPStorageProvider.java:84
LDAPStorageUserManager userManager
Definition: LDAPStorageProvider.java:94
LDAPObject getManagedLDAPUser(String userId)
Definition: LDAPStorageUserManager.java:46
LDAPConfig getConfig()
Definition: LDAPIdentityStore.java:83
◆ loadLDAPUserByUsername()
|
inline |
757 Condition usernameCondition = conditionsBuilder.equal(usernameMappedAttribute, username, EscapeStrategy.DEFAULT);
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
String getUsernameLdapAttribute()
Definition: LDAPConfig.java:188
LDAPConfig getConfig()
Definition: LDAPIdentityStore.java:83
◆ loadUsersByUsernames()
|
inline |
static final Logger logger
Definition: LDAPStorageProvider.java:84
KeycloakSession session
Definition: LDAPStorageProvider.java:87
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
◆ preRemove() [1/3]
|
inline |
◆ preRemove() [2/3]
|
inline |
◆ preRemove() [3/3]
|
inline |
◆ proxy()
|
inlineprotected |
182 List<ComponentModel> mappers = realm.getComponents(model.getId(), LDAPStorageMapper.class.getName());
List< ComponentModel > sortMappersAsc(Collection< ComponentModel > mappers)
Definition: LDAPStorageMapperManager.java:50
UserModel proxy(LDAPObject ldapUser, UserModel delegate, RealmModel realm)
LDAPStorageMapper getMapper(ComponentModel mapperModel)
Definition: LDAPStorageMapperManager.java:40
EditMode editMode
Definition: LDAPStorageProvider.java:90
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
void setManagedProxiedUser(UserModel proxiedUser, LDAPObject ldapObject)
Definition: LDAPStorageUserManager.java:61
LDAPStorageUserManager userManager
Definition: LDAPStorageProvider.java:94
LDAPStorageMapperManager mapperManager
Definition: LDAPStorageProvider.java:93
UserModel getManagedProxiedUser(String userId)
Definition: LDAPStorageUserManager.java:41
void checkDNChanged(RealmModel realm, UserModel local, LDAPObject ldapObject)
Definition: LDAPStorageProvider.java:194
◆ queryByEmail()
|
inlineprotected |
◆ removeUser()
|
inline |
281 if (editMode == UserStorageProvider.EditMode.READ_ONLY || editMode == UserStorageProvider.EditMode.UNSYNCED) {
282 logger.warnf("User '%s' can't be deleted in LDAP as editMode is '%s'. Deleting user just from Keycloak DB, but he will be re-imported from LDAP again once searched in Keycloak", user.getUsername(), editMode.toString());
288 logger.warnf("User '%s' can't be deleted from LDAP as it doesn't exist here", user.getUsername());
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
void removeManagedUserEntry(String userId)
Definition: LDAPStorageUserManager.java:73
static final Logger logger
Definition: LDAPStorageProvider.java:84
EditMode editMode
Definition: LDAPStorageProvider.java:90
LDAPObject loadAndValidateUser(RealmModel realm, UserModel local)
Definition: LDAPStorageProvider.java:455
LDAPStorageUserManager userManager
Definition: LDAPStorageProvider.java:94
void remove(LDAPObject ldapObject)
Definition: LDAPIdentityStore.java:152
◆ searchForUser() [1/4]
|
inline |
List< UserModel > searchForUser(String search, RealmModel realm)
Definition: LDAPStorageProvider.java:323
◆ searchForUser() [2/4]
|
inline |
List< UserModel > searchForUser(String search, RealmModel realm)
Definition: LDAPStorageProvider.java:323
◆ searchForUser() [3/4]
|
inline |
List< UserModel > searchForUser(String search, RealmModel realm)
Definition: LDAPStorageProvider.java:323
◆ searchForUser() [4/4]
|
inline |
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
UserModel importUserFromLDAP(KeycloakSession session, RealmModel realm, LDAPObject ldapUser)
Definition: LDAPStorageProvider.java:485
List< LDAPObject > searchLDAP(RealmModel realm, Map< String, String > attributes, int maxResults)
Definition: LDAPStorageProvider.java:405
KeycloakSession session
Definition: LDAPStorageProvider.java:87
LDAPConfig getConfig()
Definition: LDAPIdentityStore.java:83
◆ searchForUserByUserAttribute()
|
inline |
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
UserModel importUserFromLDAP(KeycloakSession session, RealmModel realm, LDAPObject ldapUser)
Definition: LDAPStorageProvider.java:485
KeycloakSession session
Definition: LDAPStorageProvider.java:87
LDAPConfig getConfig()
Definition: LDAPIdentityStore.java:83
◆ searchLDAP()
|
inlineprotected |
413 Condition usernameCondition = conditionsBuilder.equal(UserModel.USERNAME, attributes.get(UserModel.USERNAME), EscapeStrategy.NON_ASCII_CHARS_ONLY);
425 Condition emailCondition = conditionsBuilder.equal(UserModel.EMAIL, attributes.get(UserModel.EMAIL), EscapeStrategy.NON_ASCII_CHARS_ONLY);
432 if (attributes.containsKey(UserModel.FIRST_NAME) || attributes.containsKey(UserModel.LAST_NAME)) {
438 ldapQuery.addWhereCondition(conditionsBuilder.equal(UserModel.FIRST_NAME, attributes.get(UserModel.FIRST_NAME), EscapeStrategy.NON_ASCII_CHARS_ONLY));
◆ setUpdater()
|
inline |
PasswordUpdateCallback updater
Definition: LDAPStorageProvider.java:92
◆ supportsCredentialAuthenticationFor()
|
inline |
boolean isAllowKerberosAuthentication()
Definition: CommonKerberosConfig.java:49
LDAPProviderKerberosConfig kerberosConfig
Definition: LDAPStorageProvider.java:91
◆ supportsCredentialType()
|
inline |
Set< String > getSupportedCredentialTypes()
Definition: LDAPStorageProvider.java:647
◆ synchronizeRegistrations()
|
inline |
◆ updateCredential()
|
inline |
600 if (!CredentialModel.PASSWORD.equals(input.getType()) || ! (input instanceof PasswordUserCredentialModel)) return false;
610 PolicyError error = session.getProvider(PasswordPolicyManagerProvider.class).validate(realm, user, password);
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
void passwordUpdateFailed(UserModel user, LDAPObject ldapUser, PasswordUserCredentialModel password, ModelException exception)
PasswordUpdateCallback updater
Definition: LDAPStorageProvider.java:92
EditMode editMode
Definition: LDAPStorageProvider.java:90
LDAPObject loadAndValidateUser(RealmModel realm, UserModel local)
Definition: LDAPStorageProvider.java:455
KeycloakSession session
Definition: LDAPStorageProvider.java:87
void passwordUpdated(UserModel user, LDAPObject ldapUser, PasswordUserCredentialModel password)
LDAPIdentityStore getLdapIdentityStore()
Definition: LDAPStorageProvider.java:126
LDAPOperationDecorator beforePasswordUpdate(UserModel user, LDAPObject ldapUser, PasswordUserCredentialModel password)
◆ validate()
|
inline |
LDAPObject loadAndValidateUser(RealmModel realm, UserModel local)
Definition: LDAPStorageProvider.java:455
UserModel proxy(RealmModel realm, UserModel local, LDAPObject ldapObject)
Definition: LDAPStorageProvider.java:157
◆ validPassword()
|
inline |
570 if (kerberosConfig.isAllowKerberosAuthentication() && kerberosConfig.isUseKerberosForPasswordAuthentication()) {
572 KerberosUsernamePasswordAuthenticator authenticator = factory.createKerberosUsernamePasswordAuthenticator(kerberosConfig);
583 List<ComponentModel> mappers = realm.getComponents(model.getId(), LDAPStorageMapper.class.getName());
LDAPStorageProviderFactory factory
Definition: LDAPStorageProvider.java:86
LDAPIdentityStore ldapIdentityStore
Definition: LDAPStorageProvider.java:89
LDAPStorageMapper getMapper(ComponentModel mapperModel)
Definition: LDAPStorageMapperManager.java:40
boolean validUser(String username, String password)
Definition: KerberosUsernamePasswordAuthenticator.java:88
static final Logger logger
Definition: LDAPStorageProvider.java:84
boolean isAllowKerberosAuthentication()
Definition: CommonKerberosConfig.java:49
org.keycloak.storage.ldap.kerberos.LDAPProviderKerberosConfig.isUseKerberosForPasswordAuthentication
boolean isUseKerberosForPasswordAuthentication()
Definition: LDAPProviderKerberosConfig.java:41
void validatePassword(LDAPObject user, String password)
Definition: LDAPIdentityStore.java:232
KerberosUsernamePasswordAuthenticator createKerberosUsernamePasswordAuthenticator(CommonKerberosConfig kerberosConfig)
Definition: LDAPStorageProviderFactory.java:625
LDAPObject loadAndValidateUser(RealmModel realm, UserModel local)
Definition: LDAPStorageProvider.java:455
UserStorageProviderModel model
Definition: LDAPStorageProvider.java:88
LDAPProviderKerberosConfig kerberosConfig
Definition: LDAPStorageProvider.java:91
boolean onAuthenticationFailure(LDAPObject ldapUser, UserModel user, AuthenticationException ldapException, RealmModel realm)
LDAPStorageMapperManager mapperManager
Definition: LDAPStorageProvider.java:93
List< ComponentModel > sortMappersDesc(Collection< ComponentModel > mappers)
Definition: LDAPStorageMapperManager.java:54
メンバ詳解
◆ editMode
|
protected |
◆ factory
|
protected |
◆ kerberosConfig
|
protected |
◆ ldapIdentityStore
|
protected |
◆ logger
|
staticprivate |
◆ mapperManager
|
protected |
◆ model
|
protected |
◆ session
|
protected |
◆ supportedCredentialTypes
|
protected |
◆ updater
|
protected |
◆ userManager
|
protected |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/doxygen/keycloak/federation/src/federation/ldap/src/main/java/org/keycloak/storage/ldap/LDAPStorageProvider.java
 1.8.13
1.8.13