限定公開メンバ関数 | |
| JSONObject | headerToJSONObject () throws InvalidJwtException |
| JSONObject | payloadToJSONObject () throws JSONException |
非公開変数類 | |
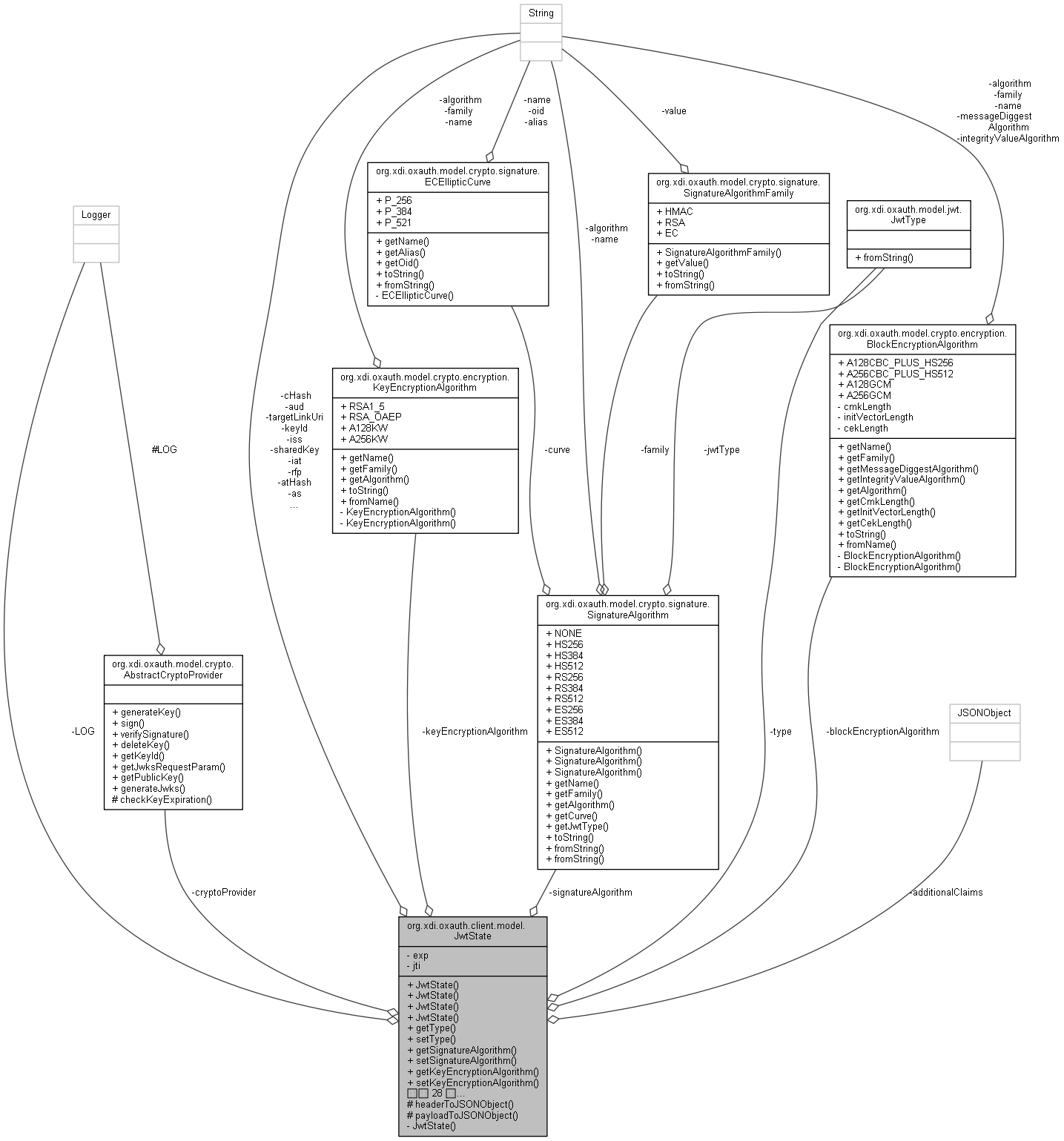
| JwtType | type |
| SignatureAlgorithm | signatureAlgorithm |
| KeyEncryptionAlgorithm | keyEncryptionAlgorithm |
| BlockEncryptionAlgorithm | blockEncryptionAlgorithm |
| String | keyId |
| String | rfp |
| String | iat |
| String | exp |
| String | iss |
| String | aud |
| String | targetLinkUri |
| String | as |
| String | jti |
| String | atHash |
| String | cHash |
| JSONObject | additionalClaims |
| String | sharedKey |
| AbstractCryptoProvider | cryptoProvider |
静的非公開変数類 | |
| static final Logger | LOG = Logger.getLogger(JwtState.class) |
詳解
- バージョン
- May 3, 2017
構築子と解体子
◆ JwtState() [1/5]
|
inline |
◆ JwtState() [2/5]
|
inline |
◆ JwtState() [3/5]
|
inline |
◆ JwtState() [4/5]
|
inline |
◆ JwtState() [5/5]
|
inlineprivate |
関数詳解
◆ getAdditionalClaims()
|
inline |
◆ getAs()
|
inline |
String identifying the authorization server that this request was sent to.
- 戻り値
- The authorization server
◆ getAtHash()
|
inline |
Access Token hash value. Its value is the base64url encoding of the left-most half of the hash of the octets of the ASCII representation of the "access_token" value, where the hash algorithm used is the hash algorithm used in the "alg" parameter of the State Token's JWS header. For instance, if the "alg" is "RS256", hash the "access_token" value with SHA-256, then take the left-most 128 bits and base64url encode them. The "at_hash" value is a case sensitive string. This is REQUIRED if the JWT [RFC7519] state token is being produced by the AS and issued with a "access_token" in the authorization response.
- 戻り値
- The access token hash value
◆ getAud()
|
inline |
String identifying the client that this state value is intended for.
- 戻り値
- The audience
◆ getBlockEncryptionAlgorithm()
|
inline |
◆ getcHash()
|
inline |
Code hash value. Its value is the base64url encoding of the left-most half of the hash of the octets of the ASCII representation of the "code" value, where the hash algorithm used is the hash algorithm used in the "alg" header parameter of the State Token's JWS [RFC7515] header. For instance, if the "alg" is "HS512", hash the "code" value with SHA-512, then take the left-most 256 bits and base64url encode them. The "c_hash" value is a case sensitive string. This is REQUIRED if the JWT [RFC7519] state token is being produced by the AS and issued with a "code" in the authorization response.
- 戻り値
- The code hash value
◆ getEncodedJwt() [1/2]
|
inline |
◆ getEncodedJwt() [2/2]
|
inline |
◆ getExp()
|
inline |
The expiration time claim identifies the expiration time on or after which the JWT MUST NOT be accepted for processing. The processing of the "exp" claim requires that the current date/time MUST be before the expiration date/time listed in the "exp" claim. Implementers MAY provide for some small leeway, usually no more than a few minutes, to account for clock skew. Its value MUST be a number containing an IntDate value.
- 戻り値
- The expiration time value
◆ getIat()
|
inline |
Timestamp of when this Authorization Request was issued.
- 戻り値
- The Issued at value
◆ getIss()
|
inline |
String identifying the party that issued this state value.
- 戻り値
- The issuer value
◆ getJti()
|
inline |
The "jti" (JWT ID) claim provides a unique identifier for the JWT. The identifier value MUST be assigned in a manner that ensures that there is a negligible probability that the same value will be accidentally assigned to a different data object. The "jti" claim can be used to prevent the JWT from being replayed. The "jti" value is a case-sensitive string.
- 戻り値
- The JWT ID
◆ getKeyEncryptionAlgorithm()
|
inline |
◆ getKeyId()
|
inline |
Identifier of the key used to sign this state token at the issuer. Identifier of the key used to encrypt this JWT state token at the issuer.
- 戻り値
- The key identifier
◆ getRfp()
|
inline |
String containing a verifiable identifier for the browser session, that cannot be guessed by a third party. The verification of this element by the client protects it from accepting authorization responses generated in response to forged requests generated by third parties.
- 戻り値
- The Request Forgery Protection value
◆ getSignatureAlgorithm()
|
inline |
◆ getTargetLinkUri()
|
inline |
URI containing the location the user agent is to be redirected to after authorization.
- 戻り値
- The target link URI
◆ getType()
|
inline |
◆ headerToJSONObject()
|
inlineprotected |
◆ payloadToJSONObject()
|
inlineprotected |
◆ setAdditionalClaims()
|
inline |
◆ setAs()
|
inline |
String identifying the authorization server that this request was sent to.
- 引数
-
as The authorization server
◆ setAtHash()
|
inline |
Access Token hash value. Its value is the base64url encoding of the left-most half of the hash of the octets of the ASCII representation of the "access_token" value, where the hash algorithm used is the hash algorithm used in the "alg" parameter of the State Token's JWS header. For instance, if the "alg" is "RS256", hash the "access_token" value with SHA-256, then take the left-most 128 bits and base64url encode them. The "at_hash" value is a case sensitive string. This is REQUIRED if the JWT [RFC7519] state token is being produced by the AS and issued with a "access_token" in the authorization response.
- 引数
-
atHash The access token hash value
◆ setAud()
|
inline |
String identifying the client that this state value is intended for.
- 引数
-
aud The audience
◆ setBlockEncryptionAlgorithm()
|
inline |
◆ setcHash()
|
inline |
Code hash value. Its value is the base64url encoding of the left-most half of the hash of the octets of the ASCII representation of the "code" value, where the hash algorithm used is the hash algorithm used in the "alg" header parameter of the State Token's JWS [RFC7515] header. For instance, if the "alg" is "HS512", hash the "code" value with SHA-512, then take the left-most 256 bits and base64url encode them. The "c_hash" value is a case sensitive string. This is REQUIRED if the JWT [RFC7519] state token is being produced by the AS and issued with a "code" in the authorization response.
- 引数
-
cHash The code hash value
◆ setExp()
|
inline |
The expiration time claim identifies the expiration time on or after which the JWT MUST NOT be accepted for processing. The processing of the "exp" claim requires that the current date/time MUST be before the expiration date/time listed in the "exp" claim. Implementers MAY provide for some small leeway, usually no more than a few minutes, to account for clock skew. Its value MUST be a number containing an IntDate value.
- 引数
-
exp The expiration time value
◆ setIat()
|
inline |
Timestamp of when this Authorization Request was issued.
- 引数
-
iat The Issued at value
◆ setIss()
|
inline |
String identifying the party that issued this state value.
- 引数
-
iss The issuer value
◆ setJti()
|
inline |
The "jti" (JWT ID) claim provides a unique identifier for the JWT. The identifier value MUST be assigned in a manner that ensures that there is a negligible probability that the same value will be accidentally assigned to a different data object. The "jti" claim can be used to prevent the JWT from being replayed. The "jti" value is a case-sensitive string.
- 引数
-
jti The JWT ID
◆ setKeyEncryptionAlgorithm()
|
inline |
◆ setKeyId()
|
inline |
Identifier of the key used to sign this state token at the issuer. Identifier of the key used to encrypt this JWT state token at the issuer.
- 引数
-
keyId The key identifier
◆ setRfp()
|
inline |
String containing a verifiable identifier for the browser session, that cannot be guessed by a third party. The verification of this element by the client protects it from accepting authorization responses generated in response to forged requests generated by third parties.
- 引数
-
rfp The Request Forgery Protection value
◆ setSignatureAlgorithm()
|
inline |
◆ setTargetLinkUri()
|
inline |
URI containing the location the user agent is to be redirected to after authorization.
- 引数
-
targetLinkUri The target link URI
◆ setType()
|
inline |
メンバ詳解
◆ additionalClaims
|
private |
◆ as
|
private |
◆ atHash
|
private |
◆ aud
|
private |
◆ blockEncryptionAlgorithm
|
private |
◆ cHash
|
private |
◆ cryptoProvider
|
private |
◆ exp
|
private |
◆ iat
|
private |
◆ iss
|
private |
◆ jti
|
private |
◆ keyEncryptionAlgorithm
|
private |
◆ keyId
|
private |
◆ LOG
|
staticprivate |
◆ rfp
|
private |
◆ sharedKey
|
private |
◆ signatureAlgorithm
|
private |
◆ targetLinkUri
|
private |
◆ type
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/gluu/src/oxAuth/Client/src/main/java/org/xdi/oxauth/client/model/JwtState.java
 1.8.13
1.8.13