org.gluu.oxtrust.ldap.service.ProfileConfigurationService の継承関係図
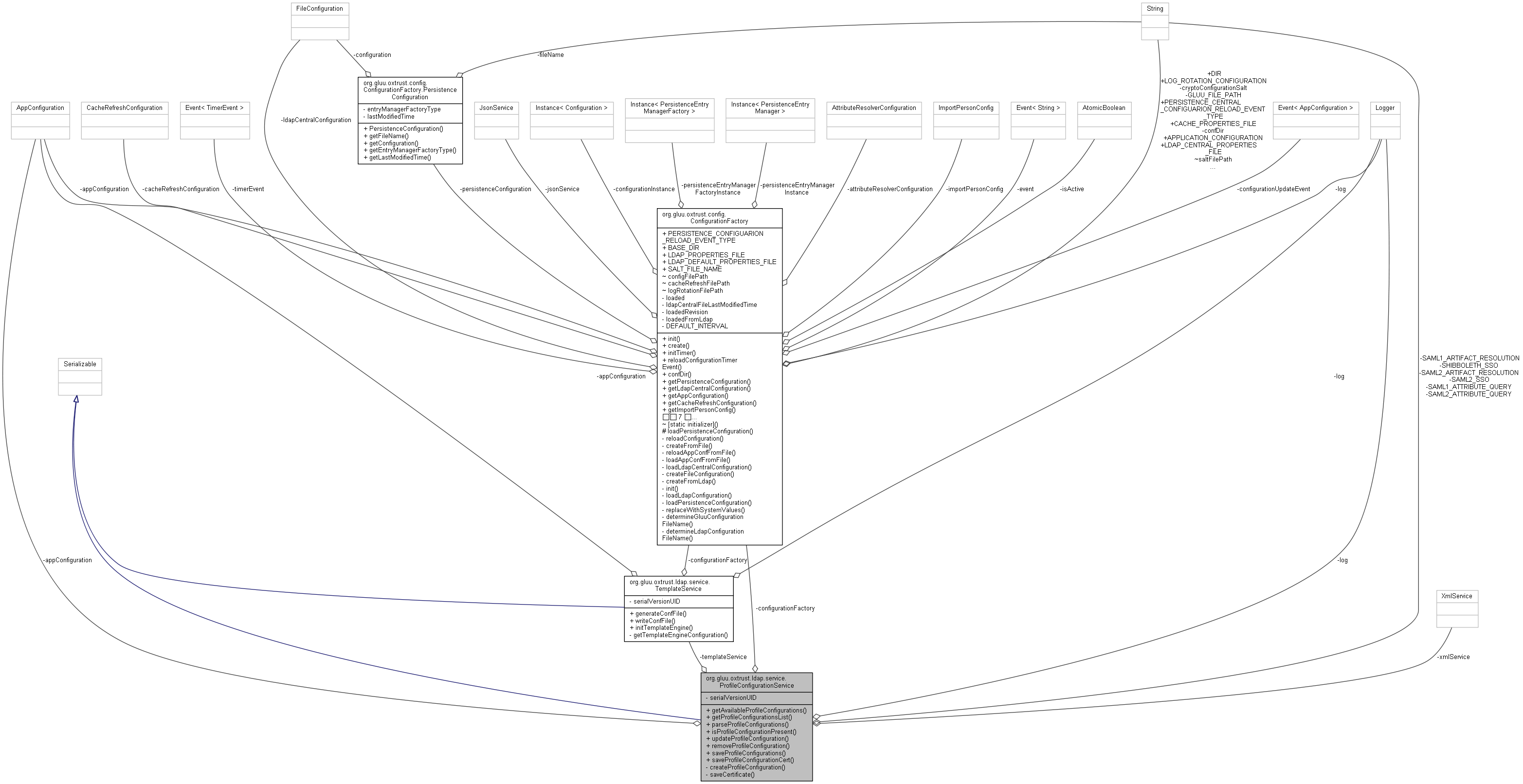
org.gluu.oxtrust.ldap.service.ProfileConfigurationService 連携図
公開メンバ関数 | |
| List< ProfileConfiguration > | getAvailableProfileConfigurations () |
| List< ProfileConfiguration > | getProfileConfigurationsList (GluuSAMLTrustRelationship trustRelationship) |
| void | parseProfileConfigurations (GluuSAMLTrustRelationship trustRelationship) throws SAXException, IOException, ParserConfigurationException, FactoryConfigurationError, XPathExpressionException |
| boolean | isProfileConfigurationPresent (GluuSAMLTrustRelationship trustRelationship, ProfileConfiguration profileConfiguration) |
| void | updateProfileConfiguration (GluuSAMLTrustRelationship trustRelationship, ProfileConfiguration profileConfiguration) |
| void | removeProfileConfiguration (GluuSAMLTrustRelationship trustRelationship, ProfileConfiguration profileConfiguration) |
| void | saveProfileConfigurations (GluuSAMLTrustRelationship trustRelationship, Map< String, FileUploadWrapper > fileWrappers) |
| String | saveProfileConfigurationCert (String profileConfigurationCertFileName, InputStream stream) |
非公開メンバ関数 | |
| ProfileConfiguration | createProfileConfiguration (String profileConfigurationName) |
| void | saveCertificate (GluuSAMLTrustRelationship trustRelationship, Map< String, FileUploadWrapper > fileWrappers, String name) |
非公開変数類 | |
| Logger | log |
| TemplateService | templateService |
| XmlService | xmlService |
| ConfigurationFactory | configurationFactory |
| AppConfiguration | appConfiguration |
静的非公開変数類 | |
| static final long | serialVersionUID = -4691360522345319673L |
| static final String | SHIBBOLETH_SSO = "ShibbolethSSO" |
| static final String | SAML1_ARTIFACT_RESOLUTION = "SAML1ArtifactResolution" |
| static final String | SAML1_ATTRIBUTE_QUERY = "SAML1AttributeQuery" |
| static final String | SAML2_SSO = "SAML2SSO" |
| static final String | SAML2_ARTIFACT_RESOLUTION = "SAML2ArtifactResolution" |
| static final String | SAML2_ATTRIBUTE_QUERY = "SAML2AttributeQuery" |
詳解
Provides operations with metadata filters
関数詳解
◆ createProfileConfiguration()
|
inlineprivate |
static final String SAML1_ATTRIBUTE_QUERY
Definition: ProfileConfigurationService.java:56
static final String SAML2_SSO
Definition: ProfileConfigurationService.java:57
static final String SAML2_ATTRIBUTE_QUERY
Definition: ProfileConfigurationService.java:59
static final String SAML1_ARTIFACT_RESOLUTION
Definition: ProfileConfigurationService.java:55
static final String SHIBBOLETH_SSO
Definition: ProfileConfigurationService.java:54
static final String SAML2_ARTIFACT_RESOLUTION
Definition: ProfileConfigurationService.java:58
◆ getAvailableProfileConfigurations()
|
inline |
78 // File profileConfigurationFolder = new File(configurationFactory.DIR + "shibboleth3" + File.separator + "idp" + File.separator + "ProfileConfiguration");
79 File profileConfigurationFolder = new File(idpTemplatesLocation + "shibboleth3" + File.separator + "idp" + File.separator + "ProfileConfiguration");
91 profileConfigurations.add(createProfileConfiguration(profileConfigurationTemplate.getName().split("ProfileConfiguration")[0]));
String getIDPTemplatesLocation()
Definition: ConfigurationFactory.java:542
ProfileConfiguration createProfileConfiguration(String profileConfigurationName)
Definition: ProfileConfigurationService.java:98
ConfigurationFactory configurationFactory
Definition: ProfileConfigurationService.java:71
◆ getProfileConfigurationsList()
|
inline |
◆ isProfileConfigurationPresent()
|
inline |
◆ parseProfileConfigurations()
|
inline |
167 if (xmlDocument.getFirstChild().getAttributes().getNamedItem("xsi:type").getNodeValue().contains(SHIBBOLETH_SSO)) {
170 profileConfiguration.setIncludeAttributeStatement(Boolean.parseBoolean(xmlDocument.getFirstChild().getAttributes()
172 profileConfiguration.setAssertionLifetime(Integer.parseInt(xmlDocument.getFirstChild().getAttributes()
174 profileConfiguration.setSignResponses(xmlDocument.getFirstChild().getAttributes().getNamedItem("signResponses")
176 profileConfiguration.setSignAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("signAssertions")
178 profileConfiguration.setSignRequests(xmlDocument.getFirstChild().getAttributes().getNamedItem("signRequests")
180 Node attribute = xmlDocument.getFirstChild().getAttributes().getNamedItem("signingCredentialRef");
189 if (xmlDocument.getFirstChild().getAttributes().getNamedItem("xsi:type").getNodeValue().contains(SAML1_ARTIFACT_RESOLUTION)) {
190 ProfileConfiguration profileConfiguration = createProfileConfiguration(SAML1_ARTIFACT_RESOLUTION);
192 profileConfiguration.setSignResponses(xmlDocument.getFirstChild().getAttributes().getNamedItem("signResponses")
194 profileConfiguration.setSignAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("signAssertions")
196 profileConfiguration.setSignRequests(xmlDocument.getFirstChild().getAttributes().getNamedItem("signRequests")
198 Node attribute = xmlDocument.getFirstChild().getAttributes().getNamedItem("signingCredentialRef");
203 trustRelationship.getProfileConfigurations().put(SAML1_ARTIFACT_RESOLUTION, profileConfiguration);
207 if (xmlDocument.getFirstChild().getAttributes().getNamedItem("xsi:type").getNodeValue().contains(SAML1_ATTRIBUTE_QUERY)) {
210 profileConfiguration.setAssertionLifetime(Integer.parseInt(xmlDocument.getFirstChild().getAttributes()
212 profileConfiguration.setSignResponses(xmlDocument.getFirstChild().getAttributes().getNamedItem("signResponses")
214 profileConfiguration.setSignAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("signAssertions")
216 profileConfiguration.setSignRequests(xmlDocument.getFirstChild().getAttributes().getNamedItem("signRequests")
218 Node attribute = xmlDocument.getFirstChild().getAttributes().getNamedItem("signingCredentialRef");
227 if (xmlDocument.getFirstChild().getAttributes().getNamedItem("xsi:type").getNodeValue().contains(SAML2_SSO)) {
230 profileConfiguration.setIncludeAttributeStatement(Boolean.parseBoolean(xmlDocument.getFirstChild().getAttributes()
232 profileConfiguration.setAssertionLifetime(Integer.parseInt(xmlDocument.getFirstChild().getAttributes()
234 profileConfiguration.setAssertionProxyCount(Integer.parseInt(xmlDocument.getFirstChild().getAttributes()
236 profileConfiguration.setSignResponses(xmlDocument.getFirstChild().getAttributes().getNamedItem("signResponses")
238 profileConfiguration.setSignAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("signAssertions")
240 profileConfiguration.setSignRequests(xmlDocument.getFirstChild().getAttributes().getNamedItem("signRequests")
242 profileConfiguration.setEncryptAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("encryptAssertions")
244 profileConfiguration.setEncryptNameIds(xmlDocument.getFirstChild().getAttributes().getNamedItem("encryptNameIds")
246 Node attribute = xmlDocument.getFirstChild().getAttributes().getNamedItem("signingCredentialRef");
255 if (xmlDocument.getFirstChild().getAttributes().getNamedItem("xsi:type").getNodeValue().contains(SAML2_ARTIFACT_RESOLUTION)) {
256 ProfileConfiguration profileConfiguration = createProfileConfiguration(SAML2_ARTIFACT_RESOLUTION);
258 profileConfiguration.setSignResponses(xmlDocument.getFirstChild().getAttributes().getNamedItem("signResponses")
260 profileConfiguration.setSignAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("signAssertions")
262 profileConfiguration.setSignRequests(xmlDocument.getFirstChild().getAttributes().getNamedItem("signRequests")
264 profileConfiguration.setEncryptAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("encryptNameIds")
266 profileConfiguration.setEncryptNameIds(xmlDocument.getFirstChild().getAttributes().getNamedItem("encryptNameIds")
268 Node attribute = xmlDocument.getFirstChild().getAttributes().getNamedItem("signingCredentialRef");
273 trustRelationship.getProfileConfigurations().put(SAML2_ARTIFACT_RESOLUTION, profileConfiguration);
277 if (xmlDocument.getFirstChild().getAttributes().getNamedItem("xsi:type").getNodeValue().contains(SAML2_ATTRIBUTE_QUERY)) {
280 profileConfiguration.setAssertionLifetime(Integer.parseInt(xmlDocument.getFirstChild().getAttributes()
282 profileConfiguration.setAssertionProxyCount(Integer.parseInt(xmlDocument.getFirstChild().getAttributes()
284 profileConfiguration.setSignResponses(xmlDocument.getFirstChild().getAttributes().getNamedItem("signResponses")
286 profileConfiguration.setSignAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("signAssertions")
288 profileConfiguration.setSignRequests(xmlDocument.getFirstChild().getAttributes().getNamedItem("signRequests")
290 profileConfiguration.setEncryptAssertions(xmlDocument.getFirstChild().getAttributes().getNamedItem("encryptNameIds")
292 profileConfiguration.setEncryptNameIds(xmlDocument.getFirstChild().getAttributes().getNamedItem("encryptNameIds")
294 Node attribute = xmlDocument.getFirstChild().getAttributes().getNamedItem("signingCredentialRef");
static final String SAML1_ATTRIBUTE_QUERY
Definition: ProfileConfigurationService.java:56
static final String SAML2_SSO
Definition: ProfileConfigurationService.java:57
static final String SAML2_ATTRIBUTE_QUERY
Definition: ProfileConfigurationService.java:59
ProfileConfiguration createProfileConfiguration(String profileConfigurationName)
Definition: ProfileConfigurationService.java:98
static final String SAML1_ARTIFACT_RESOLUTION
Definition: ProfileConfigurationService.java:55
static final String SHIBBOLETH_SSO
Definition: ProfileConfigurationService.java:54
static final String SAML2_ARTIFACT_RESOLUTION
Definition: ProfileConfigurationService.java:58
XmlService xmlService
Definition: ProfileConfigurationService.java:68
◆ removeProfileConfiguration()
|
inline |
◆ saveCertificate()
|
inlineprivate |
433 String profileConfigurationCertFileName = StringHelper.removePunctuation(name + trustRelationship.getInum());
434 saveProfileConfigurationCert(profileConfigurationCertFileName, fileWrappers.get(name).getStream());
436 .setProfileConfigurationCertFileName(StringHelper.removePunctuation(profileConfigurationCertFileName));
String saveProfileConfigurationCert(String profileConfigurationCertFileName, InputStream stream)
Definition: ProfileConfigurationService.java:441
◆ saveProfileConfigurationCert()
|
inline |
445 throw new InvalidConfigurationException("Failed to save Profile Configuration file due to undefined IDP root folder");
448 String idpMetadataFolder = appConfiguration.getShibboleth3IdpRootDir() + File.separator + SHIB3_IDP_METADATA_FOLDER + File.separator + "credentials" + File.separator;
AppConfiguration appConfiguration
Definition: ProfileConfigurationService.java:74
Logger log
Definition: ProfileConfigurationService.java:62
◆ saveProfileConfigurations()
|
inline |
330 ProfileConfiguration profileConfiguration = trustRelationship.getProfileConfigurations().get(SHIBBOLETH_SSO);
331 context.put(SHIBBOLETH_SSO + "IncludeAttributeStatement", profileConfiguration.isIncludeAttributeStatement());
338 String certName = trustRelationship.getProfileConfigurations().get(SHIBBOLETH_SSO).getProfileConfigurationCertFileName();
345 ProfileConfiguration profileConfiguration = trustRelationship.getProfileConfigurations().get(SAML1_ARTIFACT_RESOLUTION);
346 context.put(SAML1_ARTIFACT_RESOLUTION + "SignResponses", profileConfiguration.getSignResponses());
347 context.put(SAML1_ARTIFACT_RESOLUTION + "SignAssertions", profileConfiguration.getSignAssertions());
348 context.put(SAML1_ARTIFACT_RESOLUTION + "SignRequests", profileConfiguration.getSignRequests());
358 ProfileConfiguration profileConfiguration = trustRelationship.getProfileConfigurations().get(SAML1_ATTRIBUTE_QUERY);
359 context.put(SAML1_ATTRIBUTE_QUERY + "AssertionLifetime", profileConfiguration.getAssertionLifetime());
361 context.put(SAML1_ATTRIBUTE_QUERY + "SignAssertions", profileConfiguration.getSignAssertions());
364 String certName = trustRelationship.getProfileConfigurations().get(SAML1_ATTRIBUTE_QUERY).getProfileConfigurationCertFileName();
371 ProfileConfiguration profileConfiguration = trustRelationship.getProfileConfigurations().get(SAML2_SSO);
372 context.put(SAML2_SSO + "IncludeAttributeStatement", profileConfiguration.isIncludeAttributeStatement());
381 String certName = trustRelationship.getProfileConfigurations().get(SAML2_SSO).getProfileConfigurationCertFileName();
388 ProfileConfiguration profileConfiguration = trustRelationship.getProfileConfigurations().get(SAML2_ARTIFACT_RESOLUTION);
389 context.put(SAML2_ARTIFACT_RESOLUTION + "SignResponses", profileConfiguration.getSignResponses());
390 context.put(SAML2_ARTIFACT_RESOLUTION + "SignAssertions", profileConfiguration.getSignAssertions());
391 context.put(SAML2_ARTIFACT_RESOLUTION + "SignRequests", profileConfiguration.getSignRequests());
392 context.put(SAML2_ARTIFACT_RESOLUTION + "EncryptAssertions", profileConfiguration.getEncryptAssertions());
393 context.put(SAML2_ARTIFACT_RESOLUTION + "EncryptNameIds", profileConfiguration.getEncryptNameIds());
403 ProfileConfiguration profileConfiguration = trustRelationship.getProfileConfigurations().get(SAML2_ATTRIBUTE_QUERY);
404 context.put(SAML2_ATTRIBUTE_QUERY + "AssertionLifetime", profileConfiguration.getAssertionLifetime());
405 context.put(SAML2_ATTRIBUTE_QUERY + "AssertionProxyCount", profileConfiguration.getAssertionProxyCount());
407 context.put(SAML2_ATTRIBUTE_QUERY + "SignAssertions", profileConfiguration.getSignAssertions());
409 context.put(SAML2_ATTRIBUTE_QUERY + "EncryptAssertions", profileConfiguration.getEncryptAssertions());
410 context.put(SAML2_ATTRIBUTE_QUERY + "EncryptNameIds", profileConfiguration.getEncryptNameIds());
412 String certName = trustRelationship.getProfileConfigurations().get(SAML2_ATTRIBUTE_QUERY).getProfileConfigurationCertFileName();
423 templateService.generateConfFile(profileConfigurationName + "ProfileConfiguration.xml", context));
static final String SAML1_ATTRIBUTE_QUERY
Definition: ProfileConfigurationService.java:56
static final String SAML2_SSO
Definition: ProfileConfigurationService.java:57
static final String SAML2_ATTRIBUTE_QUERY
Definition: ProfileConfigurationService.java:59
void saveCertificate(GluuSAMLTrustRelationship trustRelationship, Map< String, FileUploadWrapper > fileWrappers, String name)
Definition: ProfileConfigurationService.java:431
static final String SAML1_ARTIFACT_RESOLUTION
Definition: ProfileConfigurationService.java:55
static final String SHIBBOLETH_SSO
Definition: ProfileConfigurationService.java:54
static final String SAML2_ARTIFACT_RESOLUTION
Definition: ProfileConfigurationService.java:58
TemplateService templateService
Definition: ProfileConfigurationService.java:65
String generateConfFile(String template, VelocityContext context)
Definition: TemplateService.java:51
◆ updateProfileConfiguration()
|
inline |
メンバ詳解
◆ appConfiguration
|
private |
◆ configurationFactory
|
private |
◆ log
|
private |
◆ SAML1_ARTIFACT_RESOLUTION
|
staticprivate |
◆ SAML1_ATTRIBUTE_QUERY
|
staticprivate |
◆ SAML2_ARTIFACT_RESOLUTION
|
staticprivate |
◆ SAML2_ATTRIBUTE_QUERY
|
staticprivate |
◆ SAML2_SSO
|
staticprivate |
◆ serialVersionUID
|
staticprivate |
◆ SHIBBOLETH_SSO
|
staticprivate |
◆ templateService
|
private |
◆ xmlService
|
private |
このクラス詳解は次のファイルから抽出されました:
- D:/AppData/OpenId/gluu/src/oxTrust/server/src/main/java/org/gluu/oxtrust/ldap/service/ProfileConfigurationService.java
 1.8.13
1.8.13